 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
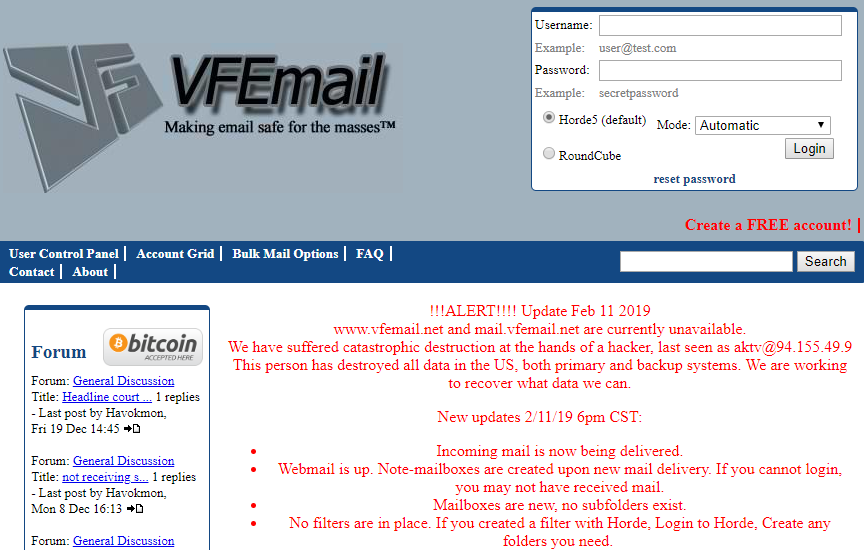
VFEmail, a service that pitches itself as “making email safe for the masses,” has suffered a “catastrophic” hack that destroyed all email and related data stored by the company dating back to 2011.
The hack took place Monday with no attempt of extortion or other intent other than the malicious deletion of the data hosted by the service.
“Yes, @VFEmail is effectively gone,” company owner Rick Romero said on Twitter today. “It will likely not return. I never thought anyone would care about my labor of love so much that they’d want to completely and thoroughly destroy it.”
On its website, VFEmail said the attacker had formatted the disks on every server, including backup servers.
Although the motivation for the hack is unknown, Ars Technica noted that given the wanton destruction of data, it’s possible VFEmail fell victim to a personal grudge.
Fausto Oliveira, principal security architect at Acceptto Corp., told SiliconANGLE that the fact that attackers could access and erase all the information demonstrates that the systems were not protected in an effective way.
“Critical systems, such as these that host customer data, must be protected with enhanced security and all operations must be protected using intelligent multifactor authentication solutions,” he said. “If those controls were in place, an operation that deviates from trusted behavior would have raised the friction toward the attackers and provide immutable logs showing that the attack was in progress, allowing VFEmail to react quickly and potentially stop the breach before data was destroyed.”
Kevin Stear, lead threat analyst at JASK Inc., said that there’s some indication that command line interface was used to reformat the disks. “If this is the case across the board for the potentially bricked servers, it implies that administrative credentials were compromised and that one or more admin accounts likely had extensive privileges across VFEmail’s entire infrastructure,” he noted.
As for the motive, Stear raised the possibility that the hacking group Armada Collective was making good on previous threats, or another malicious group had its own objectives.
“These types of destructive payloads are typically used for retribution — pain and suffering, degradation of capabilities — or a coverup,” Stear added. “For this reason, I would be very surprised if some or all of VFEmail’s data wasn’t breached or stolen prior to the destruct, which inhibits follow-on forensic analysis of the attack.”
Taking lessons from the hack, Balaji Parimi, chief executive officer of CloudKnox Security Inc., said the attack is a strong reminder to enterprises that a single keystroke or attack can destroy thousands of workloads and take down a business.
“Attacks of this magnitude — where the goal is simply to attack and destroy — are rare, but well within the power of attackers who gain access to infrastructure,” Parimi said. “Enterprises need to do a better job of mitigating the threat of overprivileged identities, and that begins with gaining an understanding of which identities have access to the types of privileges that can destroy their business and limiting those privileges to properly-trained, security-conscious personnel.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.