 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A new botnet in the wild has been found, and it’s notable for one reason: It’s really cheap to operate.
Dubbed MasterMana by security researchers at Prevailion Inc. today, the botnet, believed to have been operating since December 2018, is described as a financial scam. Using infected systems in a botnet configuration, MasterMana seeks out other systems to infect, primarily stealing cryptocurrency wallet information but also user credentials and web histories.
Where the story gets interesting is that the entire operation is estimated to have cost those behind it $100 upfront to buy the Trojan script being used by the botnet and only $60 a month for a virtual private server. In short, it’s a very low sum for the damage that the botnet can cause.
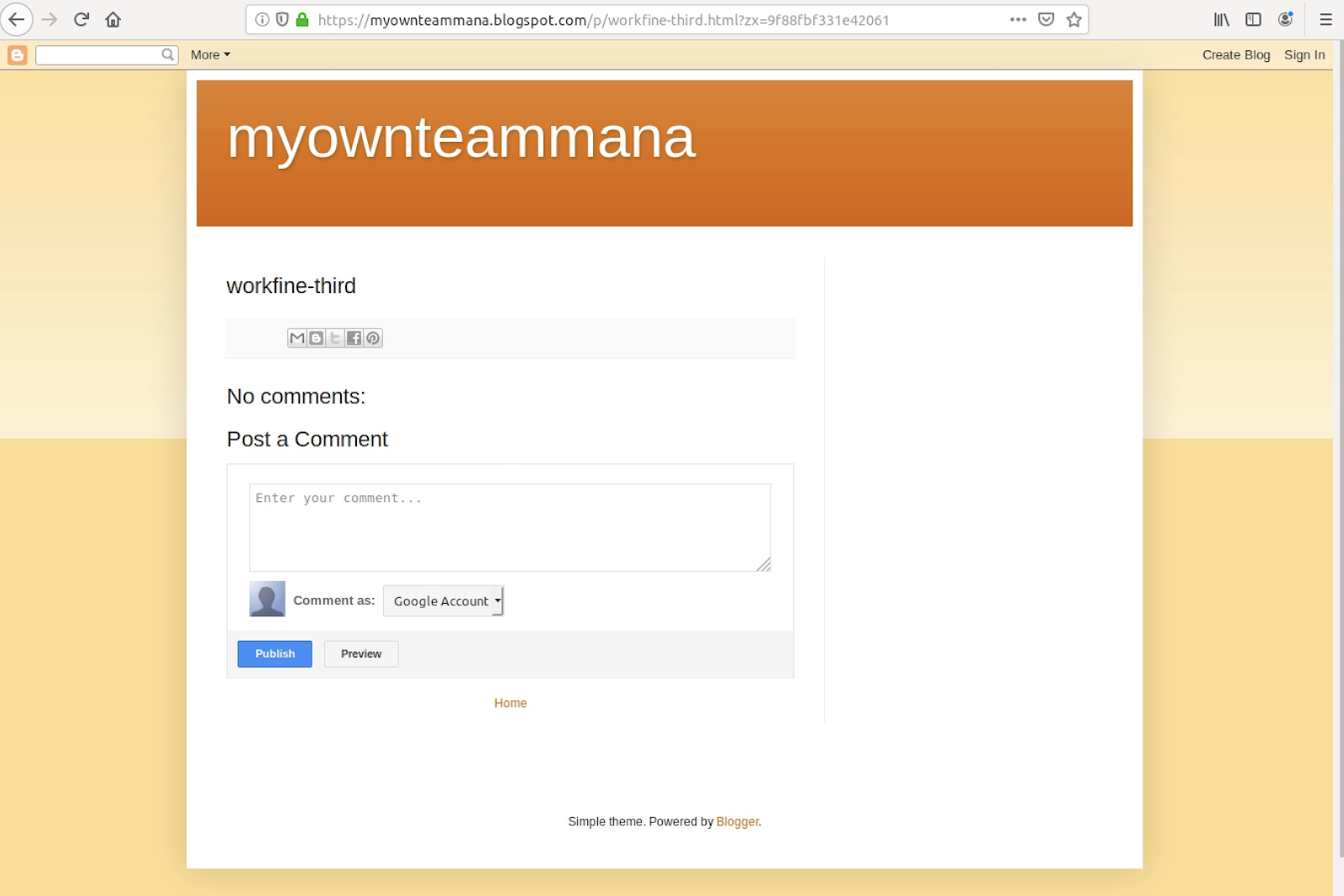
The way MasterMana keeps its costs down is by using free hosting sites to deliver its payload. Typical with these sorts of attacks, the infection path starts with phishing emails and in this case includes a malicious Microsoft Excel attachment.
When the attachment is opened, the script opens a Bit.ly link that redirects to a BlogSpot site (pictured above). The BlogSpot site then launches a legitimate Microsoft HTML Application Host utility to open a second-stage payload hosted on Pastebin. The script loaded from Pastebin then kills any running instances of Word, Excel, Powerpoint and Publisher.
It keeps on going as the script creates scheduled tasks and modifies a registry key to obtain the next payload. The last payload, which is scheduled, is then downloaded from another Pastebin URL. At this point, the Trojan is installed complete with its data-stealing ability.
It sounds somewhat complicated, but the use of free services such as Pastebin and BlogSpot to facilitate the infection allows those behind it to modify links and code along the way, building in multiple levels of redundancy should one of the links go down.
The Gorgon Group is believed to be behind the botnet. It’s a Pakistan-based threat group that may be state-sponsored.
The botnet is continuing to grow, with 3,000 machines identified so far. “While most companies fear they may become compromised by advanced actors, this particular report highlights that actors do not have to rely on advanced tools or techniques to have a serious business impact,” security researchers Danny Adamitis and Matt Thompson said.
THANK YOU