 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Security researchers at Palo Alto Network Inc.’s Unit 42 have identified the first-ever cryptojacking worm that spreads using Docker software containers.
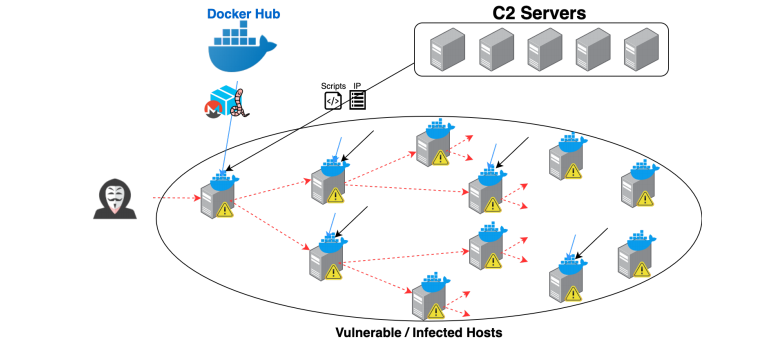
Dubbed “Graboid,” the worm spread to more than 2,000 unsecured Docker hosts and like other cryptocurrency worms before it, it utilizes the infected hosts to mine for the Monero cryptocurrency. Monero is a favorite cryptocurrency of hackers because it’s anonymous and extremely difficult to track. By contrast, bitcoin can be traced over a public ledger.
Those behind Graboid identify insecure Docker engines to start the infection process. Once the entry point is identified, the worm is deployed to start on its way.
While downloading a few scripts from a command and control server, the worm is essentially self-sufficient, starting cryptomining on the infected Docker host while looking for new victims. Graboid starts by randomly picking three potential targets for infection, installing the worm on the first target, and stops the miner on the second target, starting mining on the third target.
“This procedure leads to a very random mining behavior,” the researchers explained today. “If my host is compromised, the malicious container does not start immediately. Instead, I have to wait until another compromised host picks me and starts my mining process…. Essentially, the miner on every infected host is randomly controlled by all other infected hosts.”
On average, each miner was active 63% of the time and each mining period lasted for 250 seconds, making the activity difficult to detect since most endpoint protection software does not inspect data and activities inside containers.
The Unit 42 researchers worked with the Docker team to remove the malicious container images, but the risk of future infections from variants using similar techniques is real. “If a more potent worm is ever created to take a similar infiltration approach, it could cause much greater damage, so it’s imperative for organizations to safeguard their Docker hosts,” the researchers warned.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.