 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The United Nations and nongovernment organizations are being targeted by a sophisticated spear-phishing campaign that’s attempting to gain account credentials for Okta, Office 365 and Outlook.
Detected by security firm Lookout Inc. and publicized Thursday, the phishing campaign has been live since March 2019. It’s described as mobile-aware in that it can detect mobile devices.
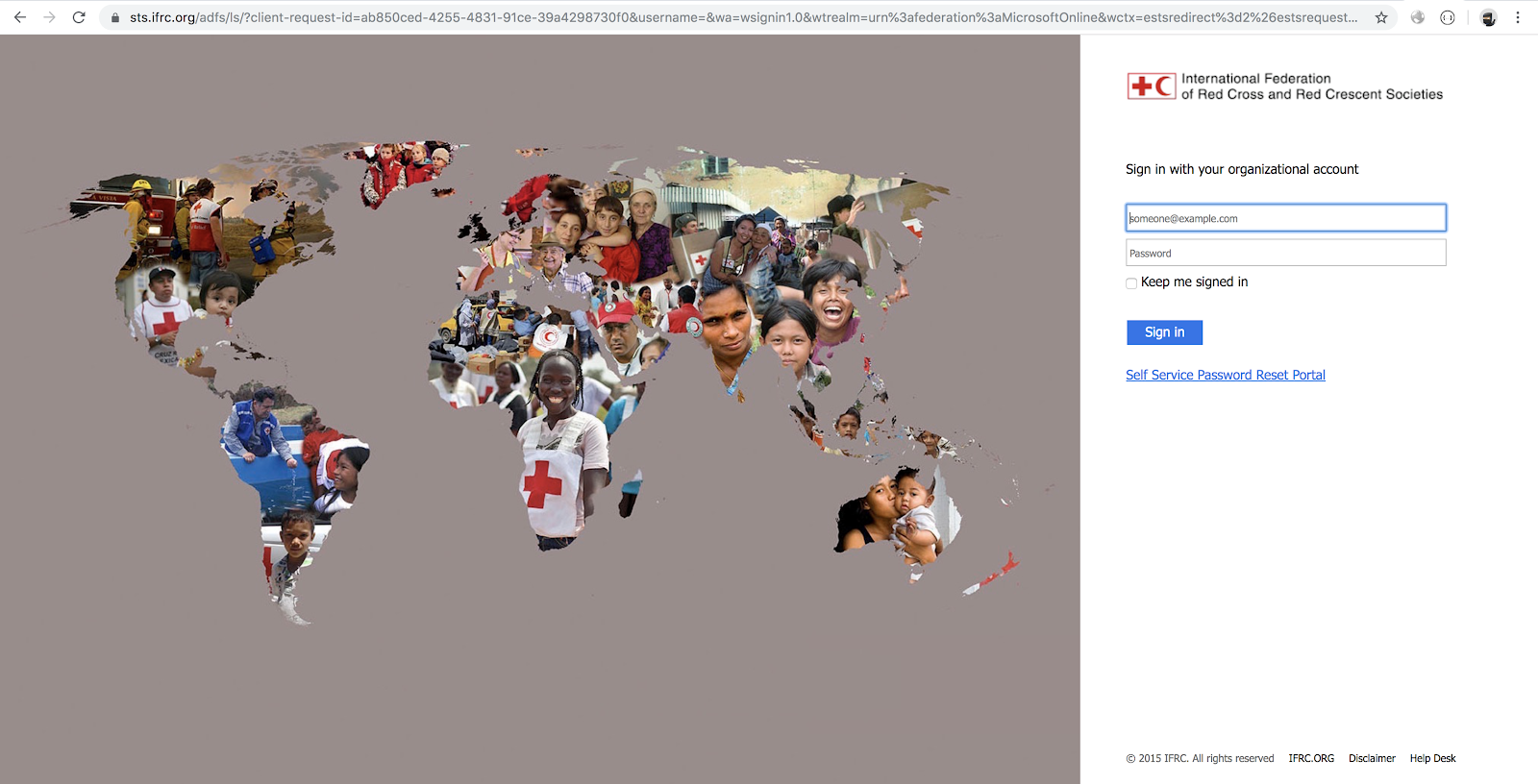
The campaign uses fake websites, such as the one pictured above, in an attempt to grab user credentials. But in a twist, it logs keystrokes in real time.
“Javascript code logic on the phishing pages detects if the page is being loaded on a mobile device and delivers mobile-specific content in that case,” the Lookout researchers explained. “Mobile web browsers also unintentionally help obfuscate phishing URLs by truncating them, making it harder for the victims to discover the deception.”
The use of a keylogger is also notable because it negates the need for a victim to complete attempting to log in, capturing the password regardless of that final process.
In a growing trend, the fake login pages were found to have had valid Secure Sockets Layer certificates at various points of time as well, giving the phishing landing pages a veneer of legitimacy.
According to the Malay Mail, the phishing sites were being hosted on a from a “bulletproof hosting service” in Malaysia that promises anonymous computing services insulated from investigators or governments. The name of the host was not disclosed but may have been a “dark web” hosting service that also provides hosting for illegal content on internet sites as well.
“The latest phishing campaign targeting officials from the United Nations, UNICEF, Red Cross and other humanitarian aid organizations demonstrates how sophisticated and highly convincing phishing attacks have become,” Alexander García-Tobar, chief executive officer and co-founder of business email compromise security firm Valimail Inc., told SiliconANGLE. “By using deviously coded phishing sites, hackers are attempting to steal login credentials and ultimately seek monetary gain or insider information.”
Most of these phishing sites never made it into widely used databases of bad links, García-Tobar added. “As a result, security tools focused on scanning the contents of email messages would not have flagged emails containing links to these sites,” he said.
Noting the unique aspects of the company Shlomi Gian, CEO at cybersecurity training firm CybeReady Learning Solutions Ltd., noted that the intensity and sophistication of phishing techniques are constantly rising.
“New phishing styles emerge frequently, but the core of these scams remains the same: An attempt to prompt email users to click a link or download an attachment that will trigger malicious activity and might result in a data breach,” Gian explained.
Jonathan Knudsen, senior security strategist at security firm Synopsys Inc., said the incident should be a wake-up call.
“Cybercriminals don’t care who you are or what you do; if you have something of value, they will try to take it,” he said. “Education and basic precautions are the key to avoiding phishing attacks. Users should know that anyone can construct a web site that looks just like the real thing, and anyone can get a legitimate certificate for a fake web site.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.