 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A Chinese state-sponsored hacking group is believed to be behind a new form of malware that’s targeting SMS text messages on servers run by telecommunications companies.
Detailed today by security researchers at FireEye Mandiant, the MESSAGETAP malware, from Chinese advanced persistent threat group APT41, was first spotted earlier this year. It was deployed against a telecommunications network provider in support of Chinese espionage efforts, according to the researchers.
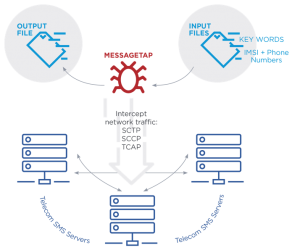 The malware was discovered on Linux servers operated as Short Message Service Center servers. SMSC servers route SMS messages to an intended recipient or store them until a recipient has come online. Once installed, MESSAGETAP, designed as a data miner, begins monitoring all network connections to and from the server, parsing both SMS message contents and related identifying data.
The malware was discovered on Linux servers operated as Short Message Service Center servers. SMSC servers route SMS messages to an intended recipient or store them until a recipient has come online. Once installed, MESSAGETAP, designed as a data miner, begins monitoring all network connections to and from the server, parsing both SMS message contents and related identifying data.
Using that data, the malware scans for keywords in the messages as well as phone numbers and IMSI numbers that match a predefined list. Those that match are then saved to a CSV file for later theft by those behind the malware.
SMS messages were not targeted by APT41 alone. The researchers said the group was also interacting with call detail record databases on infected services to query, save and steal records. Adding credence to the belief that the motivation was espionage, the CDR records corresponded to foreign high-ranking officials of interest to Chinese intelligence services.
“The use of MESSAGETAP and targeting of sensitive text messages and call detail records at scale is representative of the evolving nature of Chinese cyber espionage campaigns observed by FireEye,” the researchers wrote. “APT41 and multiple other threat groups attributed to Chinese state-sponsored actors have increased their targeting of upstream data entities since 2017. These organizations, located multiple layers above end-users, occupy critical information junctures in which data from multitudes of sources converge into single or concentrated nodes.”
MESSAGETAP follows a report Sept. 1 that an attack targeting iPhone, Android and Windows had its origins in China. In that case, it is believed that the attacks were primarily targeting the Uyghur community of the Middle Kingdom’s Xinjiang Uyghur Autonomous Region. Although Uyghurs may have been the primary target, the campaign is also believed to have infected others who inadvertently accessed infected websites used in the attack that had been indexed by Google LLC.
THANK YOU