 CLOUD
CLOUD
 CLOUD
CLOUD
 CLOUD
CLOUD
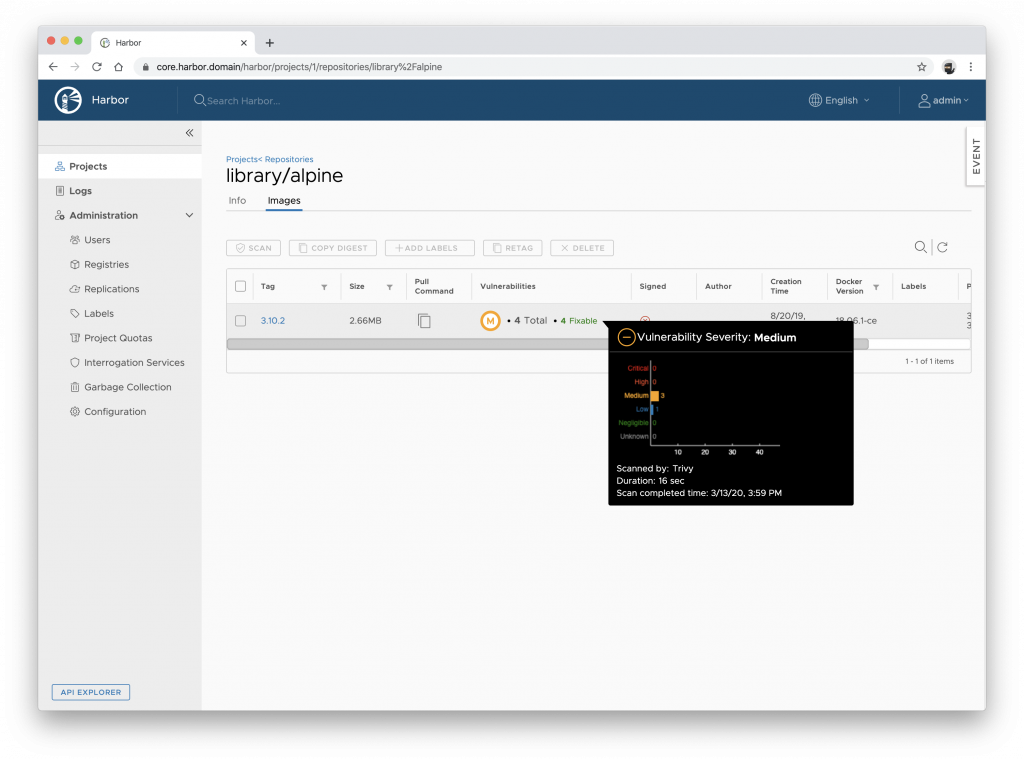
Container security startup Aqua Security Software Ltd. announced today that its open-source tool for scanning container images is now integrated by default with registries from Docker Inc. and the Mirantis Docker Enterprise platform, as well as Harbor, an open-source image registry project run by the Cloud Native Computing Foundation.
Aqua sells a Cloud Native Security Platform for software containers, which are used to host applications that can run on any computing platform.
Its software gives developers the ability to automate and improve container security and compliance posture, monitor usage and control user access. It provides granular controls over container and serverless security, supports both Docker and Windows containers, and can be deployed on-premises.
The Trivy scanner is just one component of Aqua’s platform, and was first released as an open-source project late last year. It has already attracted a “broad following” on the GitHub code hosting repository, the company said. The rapid adoption of Trivy is due to its ability to handle both operating systems and their programming language dependencies, which makes it easier to integrate with existing software development pipelines.
Trivy is available under an Apache Foundation license that allows royalty-free use and distribution.
Mirantis Inc., which acquired Docker Inc.’s enterprise platform last year, said it’s integrating Trivy with its trusted registry that runs on the Docker platform.
Trivy is also now the default image scanner in the latest version of Harbor. It allows users to secure container images through role-based access controls, and then scans the images for vulnerabilities. Once done, all trusted images are then verified as safe.
The software is just one of several open-source security projects aimed at cloud-native platforms that Aqua Security either leads or participates in, officials said. It’s also involved in the development of kube-bench, which is a tool that helps to determine if the cluster orchestration software is properly configured.
Aqua Security has also built a tool called kube-hunter, which is used to screen container clusters for vulnerabilities.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.