 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The data of more than 100 million Android app users has been found exposed because of misconfigurations relating to third-party services.
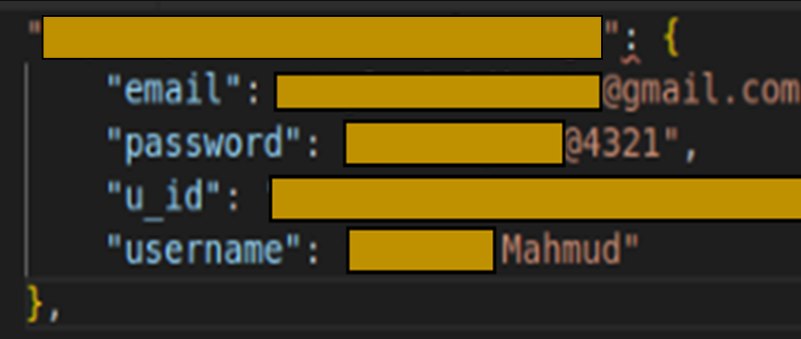
Detailed May 20 by researchers at Check Point Software Technologies Ltd., the exposure relates to 23 popular apps that put user’s personal data at risk through developer internal resources, such as access to update mechanisms and storage.
The potential breach primarily comes down to the use of real-time database access, a service that allows developers to store data on the cloud. The researchers found that they could recover sensitive information, including email addresses, passwords, private chats, device location, user identifiers and more, all because the apps didn’t secure the access between the app and the cloud database.
One example is an app called Astro Guru, which is described as a popular astrology, horoscope and palmistry app with more than 10 million downloads. The researchers could access personal information, including payment details, because of the unsecured way the data was synced through cloud-based real-time databases.
The researchers noted that although cloud storage on mobile applications is an elegant solution to access files, there can be serious implications if the developers embed the secret and access keys to the same service in their apps.
“Some of these issues uncovered in the Check Point research are similar to what we covered in the iPhone recorder incident,” Michael Isbitski, technical evangelist at application programming interface security startup Salt Security Inc., told SiliconANGLE. “Mobile application developers often make use of cloud-hosted databases and data storage, such as AWS S3, to store content for mobile clients.”
For some of the Android apps Check Point examined, he explained, developers were embedding connection keys for backend cloud storage directly into the mobile application code. “It’s a bad practice to hardcode and store static access keys into an app, which the app, in turn, uses to connect to an organization’s own backend APIs and third-party cloud APIs,” he said.
Ray Kelly, principal security engineer at cloud application security provider WhiteHat Security Inc., noted that developers tend to think that mobile backends are hidden from hackers, a practice known in the cybersecurity industry as “security through obscurity.”
“It’s akin to hiding your house key under your doormat and thinking your house is safe,” Kelly said. “Ensuring that a mobile application is secure requires that the application’s binary, network layer, backend storage and APIs are all tested thoroughly for security vulnerabilities that can lead to issues such as data leakage.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.