 BIG DATA
BIG DATA
 BIG DATA
BIG DATA
 BIG DATA
BIG DATA
Splunk Inc. is boosting the multicloud data management capabilities it offers to enterprises to help them accelerate their cloud-driven digital transformations.
The company reeled off a long list of updates today during its annual Splunk .conf21 Virtual event that should ensure customers get a better handle on the masses of data they have stored in various different public clouds. The updates came alongside a major revamp of Splunk’s observability tools and key enhancements to Splunk Security Cloud, Splunk Enterprise Security and Splunk SOAR.
Splunk’s mission is to help enterprises investigate, analyze and act on data at any scale, and to do that they do need lots of help. As companies move to embrace the cloud in search of greater agility and resilience, their information technology environments become a lot more complex.
The main challenge for companies adopting multiclouds is being able to examine all of the information stored in those environments easily and in one place. To address this, Splunk has created a new Data Manager tool (below) for Splunk Enterprise and Splunk Cloud, now available in preview, that makes it easier to access cloud data from a single location, wherever it resides. The company says it enables simple, automated cloud-native data onboarding for information stored in Amazon Web Services and Microsoft 365, and soon, Google Cloud Platform and Microsoft Azure.
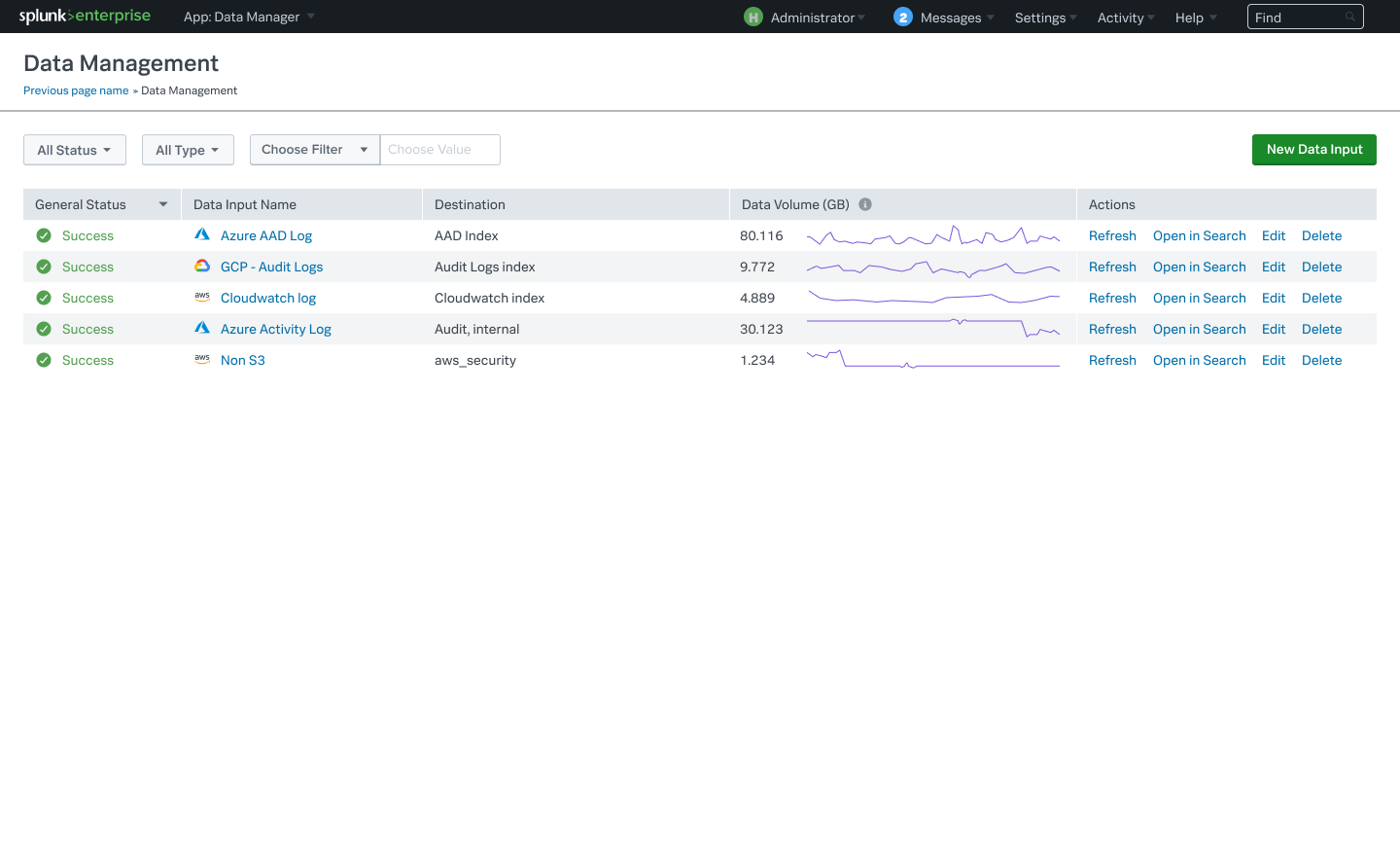
The new Splunk Ingest Actions tool, also in preview, makes it possible to take action on data in motion so companies can redact and filter it before deciding to route it to the Splunk Platform or external AWS S3 storage.
Users are getting improved indexing and storage options for their customer data as well. The new Flex Index, now available in preview for customers on workload pricing, provides more cost-effective data ingest, search and storage for what the company calls “lower-value data” that has long retention periods and is mainly used for historic forensic investigations or compliance purposes and little else.
On the cloud storage side, Splunk has added a new pricing tier for Microsoft Azure in preview called SmartStore. Already available on AWS and Google Cloud, this allows customers to scale their storage while maintaining control over costs.
Being able to store and index data is one thing. In addition, enterprises need a way to search it effectively. So the new Federated Search capability, available now, should be most welcome, as it provides companies with a unified search experience across the entire Splunk platform ecosystem.
The Splunk Mobile app also gets a useful update in the shape of Splunk Dashboard Studio, a feature that was previously limited to desktop and laptop users. With this, mobile users can turn data insights into visually compelling dashboards that can be easily understood and shared with others.
International Data Corp. analyst Archana Venkatraman welcomed today’s updates. Companies that rely on the cloud for their primary information technology infrastructure need tools to access, search and get quick answers from their data, she explained. “The data platform organizations choose should be cloud-centric and ingest data from multiple hybrid cloud sources effectively, at scale, and in an automated way,” Venkatraman said.
Splunk said customers that want to access the preview features in Splunk Enterprise need to sign up for the Splunk Enterprise Beta program first.
On the observability side, Splunk announced a string of updates to the Splunk Application Performance Monitoring, Splunk Real User Monitoring, Splunk Synthetic Monitoring, Splunk Log Observer, Splunk Infrastructure Monitoring and Splunk IT Service Intelligence tools
Splunk is making a big bet on the emerging observability niche that’s rapidly becoming a high priority for enterprises. With the shift to the cloud, companies have realized they need more ability to monitor and observe the data they’re working with across platforms. Visibility has become a must-have, Splunk responded quickly to that ask with the debut of its Observability Cloud in May.
“Observability has become a hot segment and, at the end of the day, there’s value that’s enabled from observability,” said John Furrier, host of theCUBE, SiliconANGLE Media’s livestreaming studio. “Observability is at the center of all the conversations, from monitoring, investing in on-premises or cloud infrastructure, and cybersecurity. If you don’t see data, you can’t understand what’s going on; you can’t measure it.”
Today’s updates to the Splunk Observability Platform include AlwaysOn Profiling for Splunk APM, which is now in preview and extends the platform’s full fidelity tracing back to customers through code-level visibility. The benefit is it helps companies to quickly fix any service bottlenecks, Splunk said, while identifying opportunities to optimize cloud resources and cut costs.
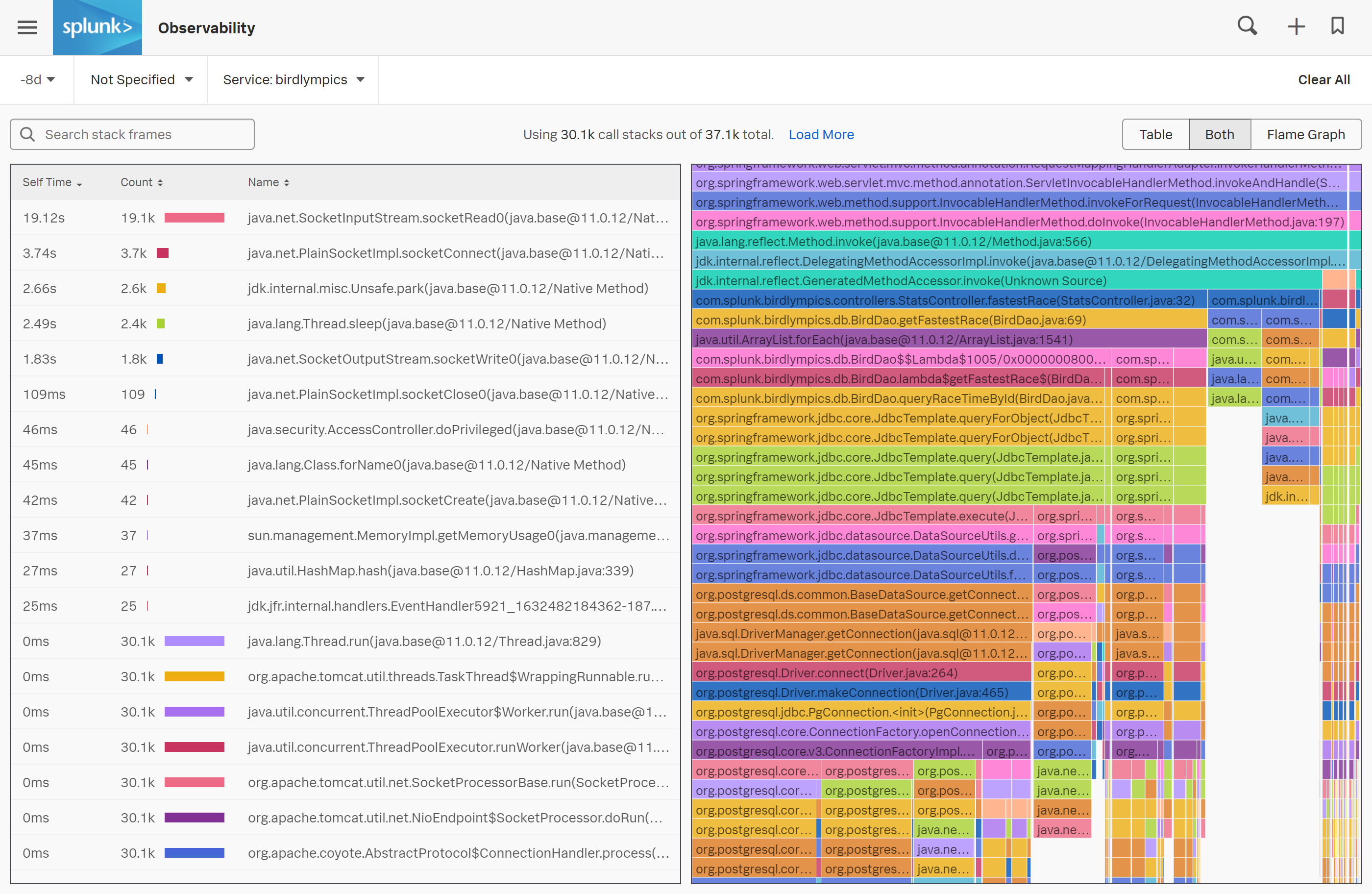
A second new capability, generally available now, is Splunk APM Database Visibility. With this, companies can automatically uncover slow queries that are the main cause of transaction latency, Splunk said, without needing to instrument the database first. That allows Splunk APM customers to monitor and troubleshoot application performance issues up to 80% faster, Splunk said.
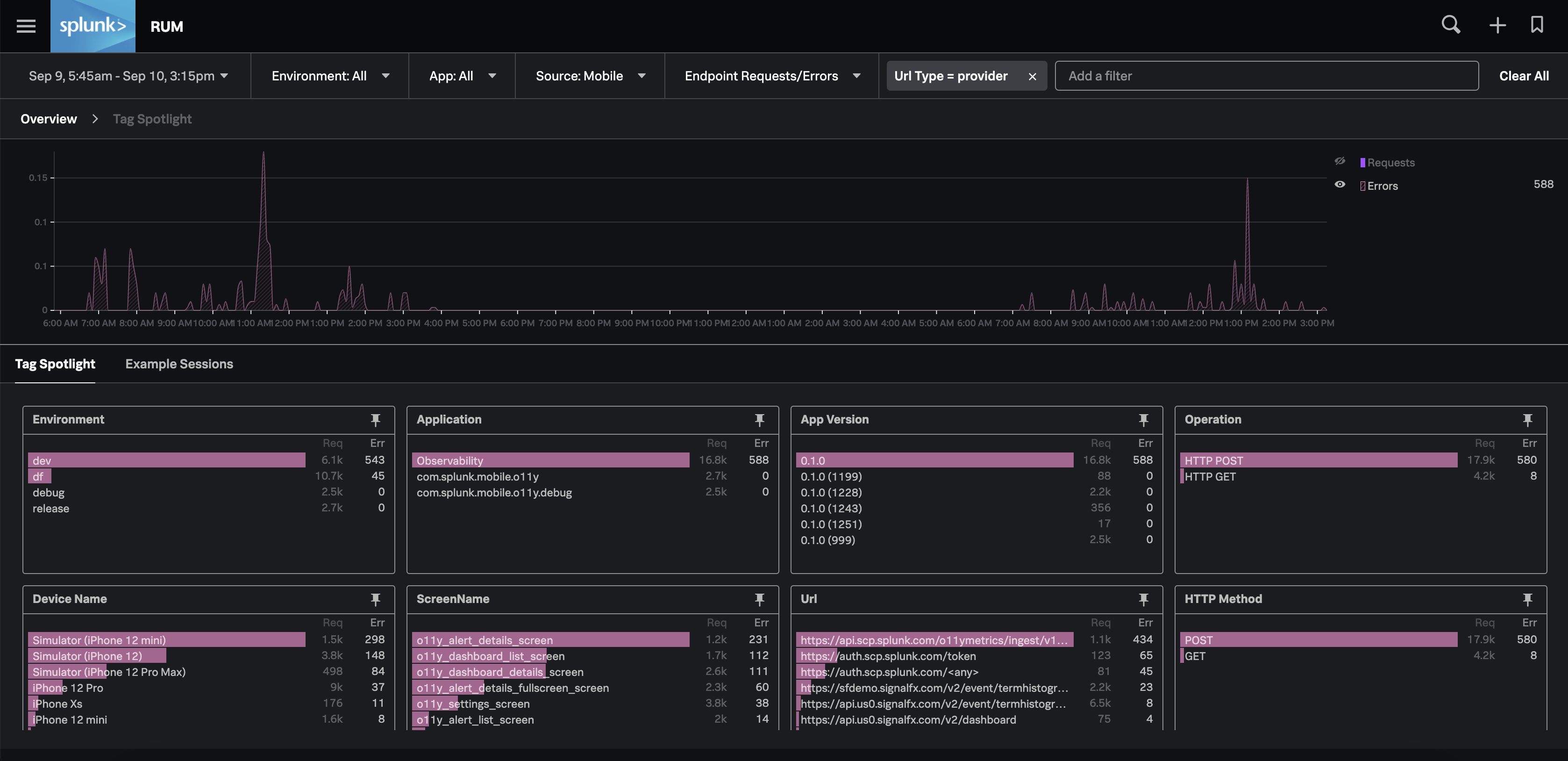
Other key updates include general availability of Splunk RUM for mobile applications. Splunk RUM is based on OpenTelemetry standards. OpenTelemetry is a key, open-source initiative led by Splunk that defines a standard for extraction of logs, traces and metric data from servers and applications that companies monitor. With Splunk RUM for Mobile, users gain more comprehensive monitoring capabilities and direct troubleshooting for native and hybrid applications on iOS and Android.
The security innovations announced today are mostly focused on adding greater visibility into cloud environments, in order to speed up time to detection, investigation and response. As Splunk explains, the shift to remote work and multicloud environments has big implications in terms of an evolving threat landscape. Many security products aren’t designed to integrate with one another, it says, so maintaining visibility across on-premises, hybrid and cloud environments can be too complex for security teams to handle. That can lead to blind spots that attackers can exploit.
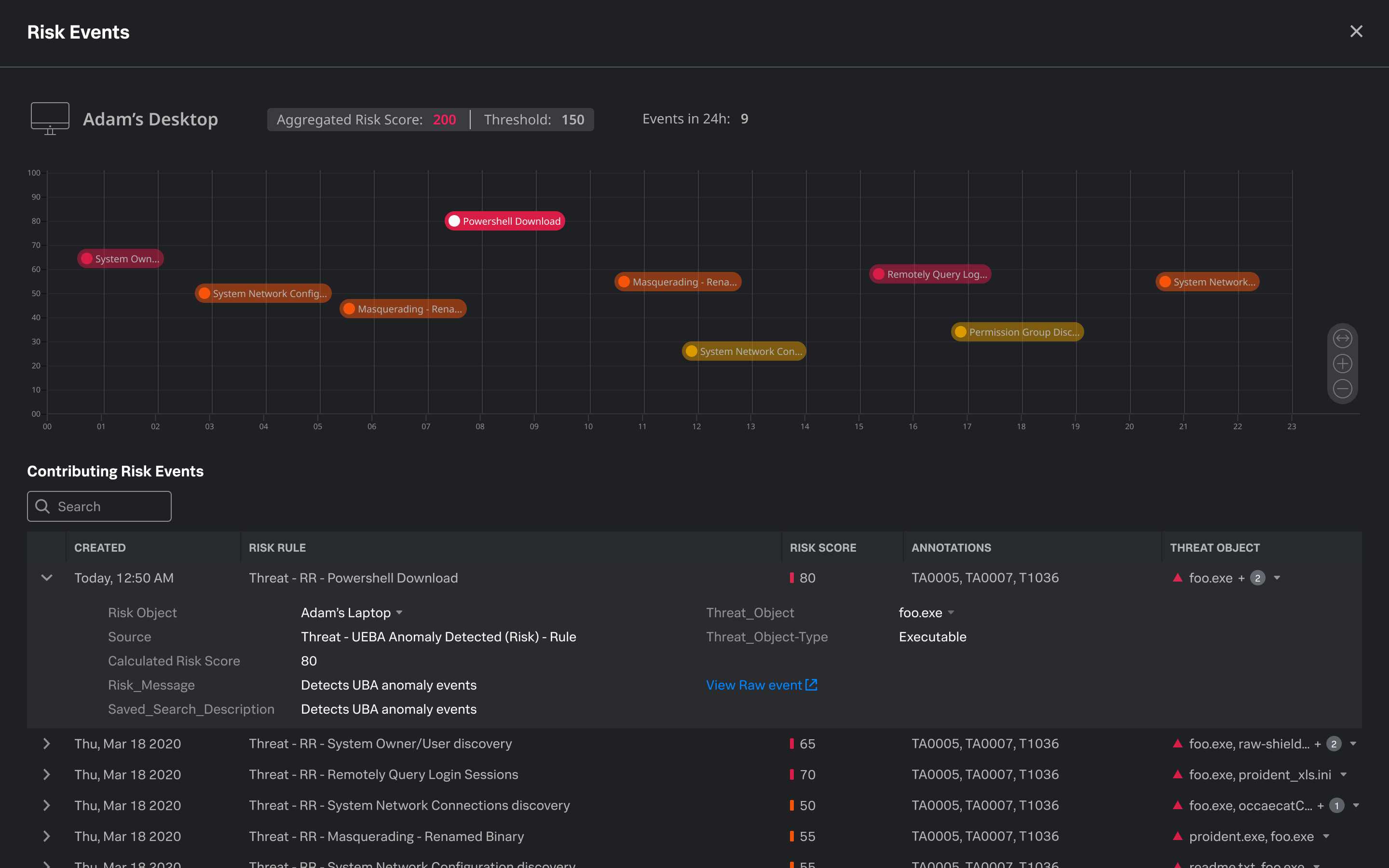
Splunk is addressing those blind spots through a cloud-delivered Security Operations Center approach that relies heavily on data analytics and automation. One of the key products is Splunk Enterprise Security, and today’s new release adds richer visualizations that make it easy to view key metrics and insights into a company’s overall health. The platform also gains Risk-Based Alerting, which Splunk said enhances threat detection while reducing alert volume by using artificial intelligence models to prioritize any threats and incidents the platform detects.
The Splunk SOAR platform that combines security infrastructure orchestration, playbook automation, case management capabilities and integrated threat intelligence gets some interesting new features too. Debuting today, the Splunk SOAR App Editor gives users a way to edit, test and create SOAR apps.
“This provides easy integration and automation between Splunk SOAR and commonly used third-party tools,” the company said. “Furthermore, there are more than 350 Splunk SOAR apps now available on Splunkbase, Splunk’s extensive ecosystem of partner and community-built technical integrations, which provides customers with a one-stop shop to extend the power of SOAR.”
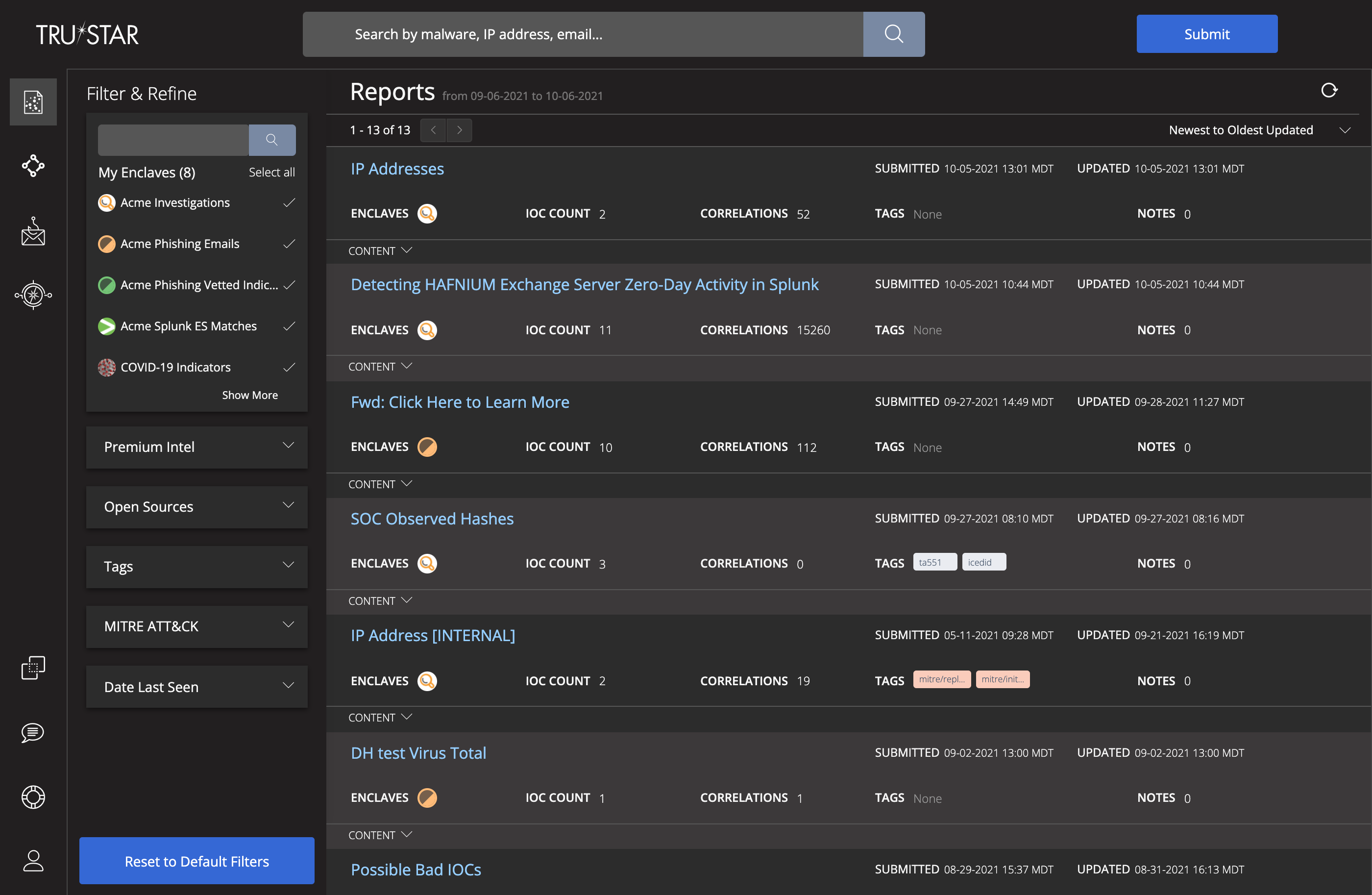
Splunk also added another intelligence source to SOAR. Having acquired TruSTAR Technology Inc. in May, that company’s platform has been transformed into a new offering within Splunk SOAR called Splunk Intelligence Management that helps customers to operationalize the various sources of security intelligence across all team, tools and partners and deliver insights directly into Splunk Enterprise Security and Splunk SOAR.
Finally, Splunk announced the creation of what it calls an “elite team of cybersecurity experts” that will be on hand to assist customers in the event they get hit by a cyberattack. The Splunk SURGe team will serve as a trusted adviser to support companies as they attempt to respond to and minimize the damage caused by any attack. It will also create response guides and in-depth analysis in the form of research papers and webinars to aid the wider community.
“SURGe is your partner during high-profile security incidents,” said Ryan Kovar, a distinguished security strategist at Splunk. “We’re here to provide details like who is behind a major cyberattack, details on the techniques being used and its implementation. We’ll also show you how to apply our trusted security research in your response workflow so that you can quickly identify exploits and act on it.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.