 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Palo Alto Networks Inc. is refreshing its cybersecurity product portfolio with an array of new capabilities for protecting enterprise public cloud environments from hacking attempts.
The company detailed the enhancements at its Ignite 2021 event today.
Publicly traded Palo Alto Networks is one of the industry’s largest makers of enterprise cybersecurity software. The company boasts more than 80,000 customers. Like other established players in the enterprise software market, Palo Alto Networks has in recent years made the public cloud a bigger focus of its product roadmap to address the fact that its customers are moving more and more of their workloads off-premises.
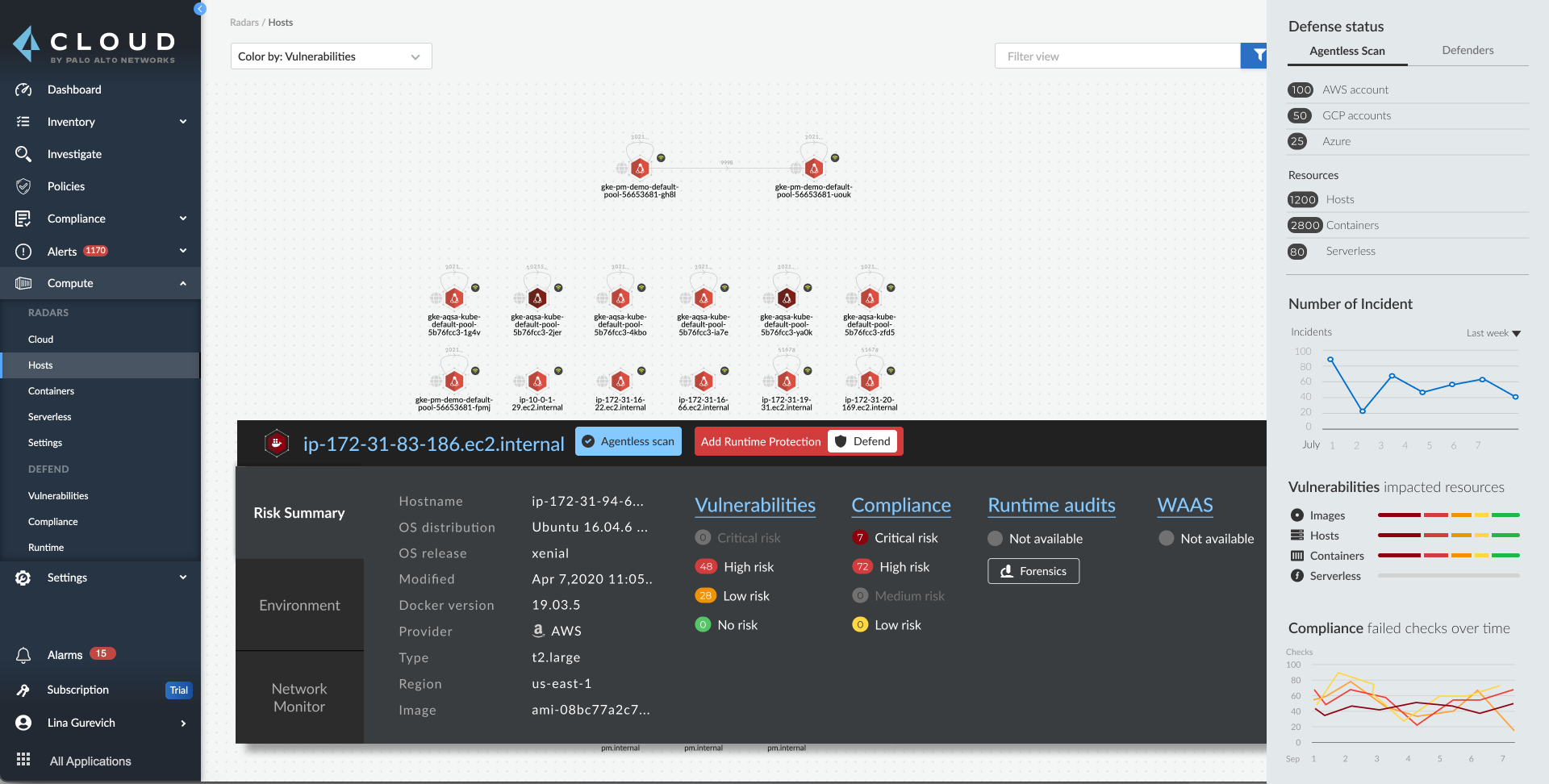
A core pillar of Palo Alto Networks’ public cloud strategy is its Prisma Cloud platform. It provides features for protecting applications that an organization runs on the major public clouds. The platform is among the products for which the company debuted updates at Ignite 2021 today.
The latest Prisma Cloud release, Prisma Cloud 3.0, adds features for detecting vulnerabilities in infrastructure-as-code templates.
When a company deploys a new application in its cloud environment, administrators must update the environment’s configuration settings to accommodate the changes. Configuration changes are necessary in many other cases as well. Increasingly, administrators update cloud settings not manually but rather using automated scripts known as infrastructure-as-code templates.
Scripts provide a faster and more convenient way to define configuration settings. They also reduce the chance of human error. But if implemented incorrectly, infrastructure-as-code templates can introduce cybersecurity risks by creating misconfigurations that increase the risk of a breach. According to Palo Alto Networks, the new Prisma Cloud release automatically spots vulnerabilities in infrastructure-as-code templates to help companies avoid misconfigurations that could be targeted by hackers.
“Our recent Unit 42 Cloud Threat Report shows the extent of emerging cloud code security risks: we found 63% of templates used in building cloud infrastructure contained misconfigurations that can expose environments to vulnerabilities,” said Ankur Shah, senior vice president of product management for Prisma Cloud. “Prisma Cloud’s new capabilities secure cloud environments from development to runtime in a single platform, shifting security left to proactively address issues that begin in development.”
Also new in Prisma Cloud 3.0 is an agentless security feature. Prisma Cloud finds cybersecurity issues by analyzing cybersecurity data from a company’s cloud environment. Until now, the platform collected cybersecurity data mainly using software agents, small programs installed in key parts of the cloud environment being monitored. Customers now have the option to deploy Prisma Cloud 3.0 without installing agents, which can be more convenient in some cases depending on how a company’s infrastructure is set up.
Prisma Cloud is designed to work with all the major public clouds. To make the platform a more compelling choice for companies taking a multicloud approach, Palo Alto Networks is adding improved Azure support. The platform can now help companies using Microsoft Corp.’s public cloud to detect cases where administrator accounts have broader access to cloud resources than is strictly necessary. Misconfigured accounts can cause risks in the event they’re breached by hackers.
At Ignite 2021, Palo Alto Networks also introduced Palo Alto Networks Next-Generation CASB. It’s a tool for securing the software-as-a-service applications that a company’s employees use as part of their day-to-day work. The offering will become available with Palo Alto Networks’ firewall products and its Prisma SASE offering.
According to the company, Next-Generation CASB helps enterprises detect software-as-a-service applications that employees are using without approval from the information technology team. Applications used without authorization can potentially contain cybersecurity vulnerabilities. For added measure, Next-Generation CASB uses machine learning to detect if sensitive business information is used in a way that may increase the risk of a data breach.
The threat detection capabilities of Palo Alto Networks’ product lineup are powered partly by WildFire, a homegrown malware detection engine. The engine determines if files are malicious by consulting cybersecurity data that Palo Alto Networks aggregates from its installed base of more than 80,000 organizations. Today, the company said that it’s making WildFire available as a standalone product to let customers apply its malware detection capabilities in new ways.
Palo Alto Networks has made several startup acquisitions in recent years to advance its cloud security roadmap. One of the company’s most recent acquisitions was the purchase of Bridgecrew for $156 million earlier this year. Bridgecrew developed a platform that helps companies detect and fix insecure configuration settings in their cloud environments.
THANK YOU