 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Criminal groups and even suspected state-sponsored hacking groups continue to exploit a serious vulnerability in Apache Log4j with ransomware and other forms of malware.
According to research from Check Point Software Technologies Ltd., the number of attacks seeking to take advantage of the vulnerability continues to rise, from 40,000 attacks on Dec. 11 through to more than 800,000 attacks on Dec. 13. The number of variants being used to exploit the vulnerability has also increased to 60 over the same period.
The number of attacks coupled with the severe nature of the vulnerability has prompted the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Agency to issue multiple warnings and order all federal agencies to patch the vulnerability by Dec. 24.
The patch in Logj4 version 2.15.10, addresses the vulnerability known in the Common Vulnerabilities and Exposures database as CVE-2021-44228. CISA noted that for the vulnerability to be remediated in products and services that use affected versions of Log4j, the maintainers of those products and services must implement this security update. The agency urged vendors to identify, mitigate and patch affected products using Log4j immediately, inform their end-users of products that contain the vulnerability and strongly urge them to prioritize software updates.
“Right now, every IT person in the world is trying to identify if their machines have vulnerable Log4j packages,” Mike Wiacek, founder and chief executive officer of cybersecurity company Stairwell Inc., told SiliconANGLE. “Attackers are winning because combatting unexpected major vulnerabilities like Log4j takes an incredible amount of time — and time to patch — particularly in large enterprises. And time is often the determining factor for the amount of damage from a breach.”
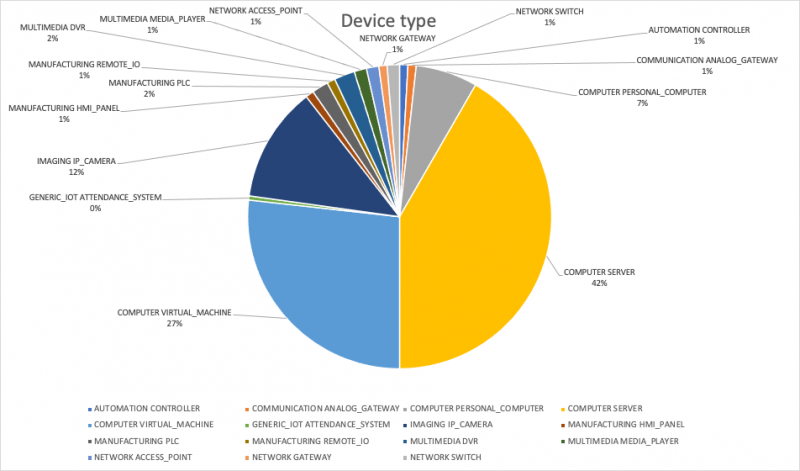
The sheer number of recorded attacks alone does not fully demonstrate how widespread the attacks are. Agentless device security platform firm Armis Inc. says it has detected Log4j/Log4shell attack attempts against 35% of its clients with new attacks every day.
The number of targeted devices (above) ranges across all sorts of devices, with the top three physical servers at 42%, virtual servers st 27% and internet-connected cameras at 12%. Armis has also spotted attack attempts against manufacturing devices such as HMI panels and controllers, as well as against attendance systems.
“This data clearly demonstrates the urgency to act now as the Log4j vulnerability is actively being exploited now and we expect to see these instances multiply as the week’s progress,” Armis Chief Technology Officer Nadir Izrael said. “It is vital that companies scan their environments now and administer workarounds as soon as they can to limit any lasting damage.”
While ransomware attacks exploiting Log4j have already gained attention, such as with the attack on workflow management solutions provider Kronos Inc., cybercriminals are using the vulnerability to deploy a wide range of malware against victims.
Through the deployment of a honey pot, researchers at Bitdefender S.R.L observed a range of attacks. Deployments include several botnets, including the Muhstik botnet that adds a backdown and deploys a crypto-miner, the XMRIG miner, a new form of ransomware called Khonsari, the Orcus remote access Trojan and reverse Bash shells that can be used for later attacks.
With many companies scrambling to patch the original Log4j vulnerability, a new vulnerability has appeared, called CVE-2021-45046. The vulnerability is found in Log4j version 2.15.10, the version that patches the original vulnerability and is described in the CVE database as the result of the update being “incomplete in certain nondefault configurations.”
“When a vulnerability is discovered and makes as much noise as Log4Shell, it invariably signals that there are additional vulnerabilities in the same software or fixes for that software and triggers additional research and discovery,” explained Casey Ellis, founder and CTO at crowdsourced security platform company Bugcrowd Inc. “In this case, the initial fix provided was developed in a way that mitigated the exploitable symptom but didn’t properly address the root cause.”
Apache has released another update, Logj4 2.16.0, to address the new vulnerability.
THANK YOU