 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
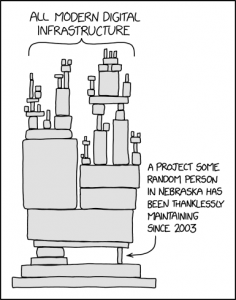
Image: xkcd.com
There’s a great cartoon that sums up the state of modern software. Titled “Dependency,” it shows a mass of digital infrastructure teetering on one small piece of open-source code. The image is ridiculous, but the issue is not a joke.
A 2020 audit of more than 1,250 commercial codebases found that 99% of them included at least one open-source component. This is indicative of the increasing use of open source and overall a testament to the strength and commitment of the community. But … and it’s a big but … 75% of that surveyed code contained known security vulnerabilities, and 65% of these known vulnerabilities were high-risk.
The reality is that almost all modern applications include open-source components, and there is no oversight to ensure they are maintained.
“It’s an amazing thing … that we have this rich commons of open-source software to build with,” said Donald Fischer (pictured), co-founder and chief executive officer of Tidelift Inc. “But we also have to be practical about it and say, ‘Hey, how are we going to work together to make sure that software … meets commercial, enterprise standards?’”
Fischer spoke with Dave Vellante, host of theCUBE, SiliconANGLE Media’s livestreaming studio, during the AWS Startup Showcase: Open Cloud Innovations event. They discussed the state of open-source security and how Tidelift’s solution solves the issue for enterprise while simultaneously supporting the developer community. (* Disclosure below.)
The problem was brought into stark relief on Dec. 9, when Chen Zhaojun of the Alibaba Cloud Security Team revealed the Java-based logging utility Apache Log4j 2 had a critical vulnerability that allowed it to be exploited to gain shell-level access to any server that has the software running on it. Fixing the issue, which has been named Log4Shell, ruined the holidays for many in the tech industry.
“Log4j is a really clarifying case for folks to understand what can seem a small part of your overall application estate can have a disproportionate impact on your operations,” Fischer said.
The vulnerability has a positive in that it has catalyzed organizations to go beyond fixing the immediate issue and to think proactively about how to put measures in place to prevent open-source vulnerabilities.
The United States government’s “Executive Order on Improving the Nations Cybersecurity,” released May 12, 2021, put the nation ahead of the game by drawing attention to the problem and directing organizations on how to respond to it, according to Fischer. Notably, the Order implemented hard requirements around federal agencies uses of open-source software by demanding a software bill of materials, known as an SBOM, from vendors that are doing business with the government. This is analogous to a list of ingredients on packaged food and provides a “ formal record containing the details and supply chain relationships of various components used in building software,” according to the Executive Order.
“The strategy there has been to expressly use the purchasing power of the U.S. government to level up industry as a whole and create the necessary incentives for organizations to take this seriously,” Fischer said.
There’s a huge gap, however, between taking a problem seriously and finding a way to address it. But address it the industry must.
The rise in cybercrime has made the good old “head in the sand” approach an incredibly bad idea. Not only because of the financial and reputational loss when the inevitable breach occurs, but because companies that do not take measures to secure their code are breaking the law.
The United States Federal Trade Commission recently made a direct warning to private companies and industry. Citing the $700 million settlement made by credit reporting agency Equifax Inc. after a data breach related to an open-source component, the FTC said in a blog post published on Jan. 4 that it “intends to use its full legal authority to pursue companies that failed to take reasonable steps to protect consumer data from exposure as a result of Log4j or similar known vulnerabilities in the future,” Fischer said.
Tidelift was founded after Fischer and his team, all open-source industry veterans, saw that while vendors existed for traditional systems-level open-source components and stacks such as Linux, Kubernetes and some databases, there was no vendor support for small Log4Shell-style projects.
According to Fischer, a typical enterprise inspected by Tidelift has upwards of 10,000 Log4j-like components flowing into their applications. This creates an almost insurmountable challenge for the software development teams charged with ensuring all those components meet reasonable commercial standards.
One way is through Tidelift’s purpose-built software solution that keeps track of third-party open source flowing into applications by inserting itself into a company’s DevSecOps toolchain, developer tooling, and application development process, according to Fischer.
“Think of it as next to the point in your release process where you run your unit test to ensure the business logic in the code that your team is writing is accurate,” he said. “We do an inspection to look at the state of the third-party open source, packages like Apache Log4j that are flowing into your application.”
The other side of Tidelift’s solution is more unusual. The company has created a community of independent open-source developers — the very people who create and maintain the smaller projects that form the foundation of the applications businesses rely on. And, they pay them.
A survey by Tideware found that many open-source developers are stressed out and underpaid but keep coding because they believe in the positive impact of what they are doing. So, it was a win-win situation to support them to follow that passion.
“We’re helping these open-source maintainers ‘go pro’ on an aspect of what they do around open source,” Fischer said.
That means the developers are incentivized to make sure their software meets enterprise standards for security and compliance, licensing, and accuracy and compatibility. It also means that instead of potentially abandoned and unmaintained projects enterprise IT teams can be sure the software they are using is current and trackable for that all-important SBOM.
“That’s good for our customers, and it’s good for everyone who relies on open-source software, which is really everyone in society these days,” Fischer said.
Here’s the complete video interview, part of SiliconANGLE’s and theCUBE’s coverage of the AWS Startup Showcase: Open Cloud Innovations event. (* Disclosure: Tidelift sponsored this segment of theCUBE. Neither Tidelift nor other sponsors have editorial control over content on theCUBE or SiliconANGLE.)
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.