 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Google Cloud has updated its collection of security blueprints with the addition of a Secure Data Warehouse Blueprint that customers are free to implement to safeguard their cloud data.
Google’s security blueprints combine best practices with opinionated guidance to help customers build stronger security into their cloud deployments. In the case of its Secure Data Warehouse Blueprint, published today, it has created an actionable framework that’s designed to preserve the security, confidentiality and integrity of business data while it’s stored in cloud data warehouses, in transit or in use.
In a blog post, Google Senior Security Product Manager Andy Chang and Security & Compliance Customer Engineer Erlander Lo explained that the blueprint employs a unique, layered cybersecurity approach. It’s aimed at minimizing the amount of infrastructure admins need to manage, reducing the potential attack surface for hackers.
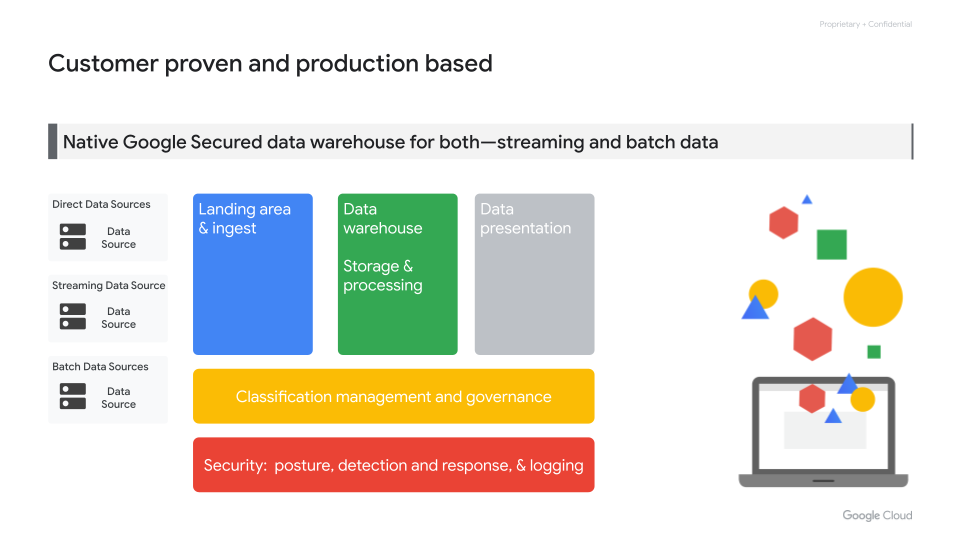
The blueprint encompasses four layers. There’s a “landing area layer” that handles how batch or streaming data is ingested, as well as a “data warehouse layer” that covers storage and de-identification of data. In addition, a “classification and data governance layer” manages encryption and data classification taxonomy, and a “security posture layer” aids in detection, monitoring and response.
Chang and Lo said the blueprint will benefit customers in a number of ways, with the main focus being on providing strong baseline security and flexibility. One of the main advantages is that it allows teams to use “infrastructure as code” techniques to analyze their security controls and compare these against their enterprise requirements for creating, deploying and operating data systems. IaC also simplifies regulatory and compliance reviews.
The layered security approach also makes it easy to demonstrate to security, risk and compliance teams exactly which security controls have been implemented. For example, the diagram below illustrates not just the security services built into the architecture, but how they work together to protect data:
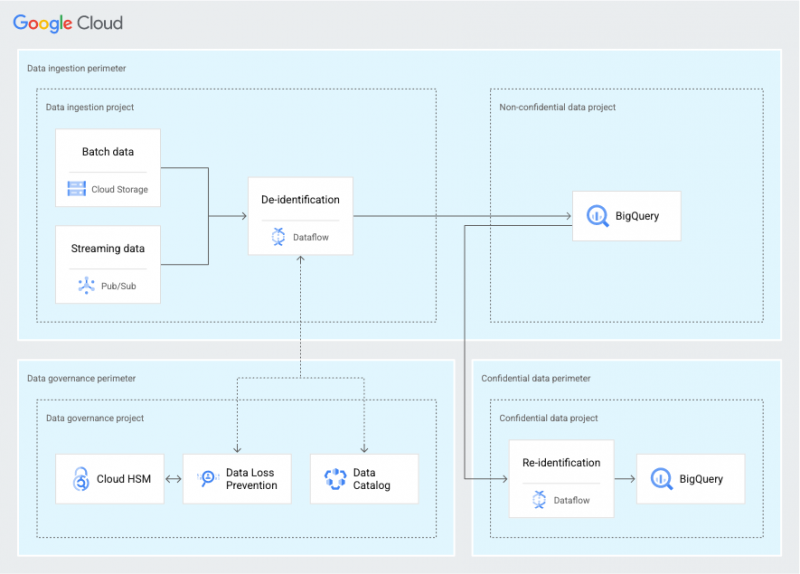
Another benefit of Google’s reference architecture is that it allows users to monitor and define where data can and cannot flow. They can establish perimeters that constrain data to specific projects and services in order to minimize the risk of data exfiltration.
Further controls can be added, such as preventing the use of external IPs from accessing data and ensuring data in transit only flows through trusted networks. And the blueprint provides fine-grained identity and access management policies to limit access to different data sets, based on how sensitive they are.
Moreover, the blueprint helps to facilitate complex compliance requirements. For instance, users can address data minimization requirements through Google Cloud Data Loss Prevention’s cryptographic transformation tools. Meanwhile, data encryption is handled using keys managed using Google Cloud HSM
The blueprint also describes how companies can use security tools such as Google Cloud Security Command Center for threat detection and Security Health Analytics. That way, they can continuously monitor each project covered by the blueprint to minimize the risk of misconfigurations.
Google said its Secure Data Warehouse Blueprint has been reviewed by the Google Cybersecurity Action Team and a third-party security team. Customers can download the blueprint now, or alternatively download a ready-made secure data warehouse that’s good to go via the deployable Terraform.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.