 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
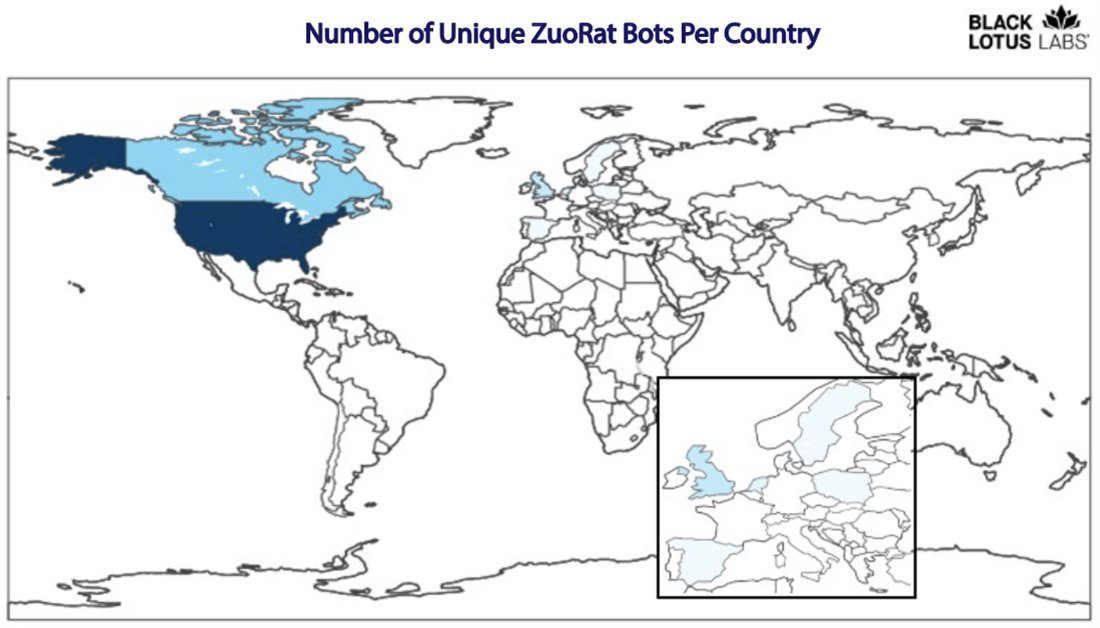
A newly discovered form of malware has been found to be actively targeting small office-home office routers in Europe and North America.
Dubbed “ZuoRAT” today by researchers at Lumen Technologies Inc.’s Black Lotus Labs, the malware is described as a multistage remote access trojan and is believed to have been active since 2020. The malware grants the hackers behind it the ability to gain access to the local network and additional systems on the local area network by hijacking communications to maintain an undetected foothold.
ZuoRAT is a file compiled for SOHO routers that can enumerate a host and internal LAN, capture packs transmitted over the infected device and perform man-in-the-middle attacks, including DNS and HTTPS hijacking. The captured data is then sent to a command-and-control server.
Routers getting hacked is not a new development, but the researchers note that where ZuoRAT is interesting is that compromising SOHO routers is seldom reported. The use of man-in-the-middle attacks targeting SOHO routers is said to be even rarer and suggests that those behind ZuoRAT demonstrate a high level of sophistication and are possibly a state-sponsored organization.
Why SOHO routers are being targeted is also speculated to reflect the shift to remote work driven by the COVID-19 pandemic. “The sudden shift to remote work spurred by the pandemic allowed a sophisticated adversary to seize this opportunity to subvert the traditional defense-in-depth posture of many well-established organizations,” the researchers write.
“SOHO firmware typically isn’t built with security in mind, especially pre-pandemic firmware where SOHO routers weren’t a big attack vector,” David Schloss, offensive security team lead at cybersecurity and IT risk advisory firm Echelon LP, told SiliconANGLE. “So, the only people screwing with it were people looking to create botnets.”
Casey Ellis, founder and chief technology officer at crowdsourced cybersecurity company Bugcrowd Inc., called this a “pretty decent” find. “There has been a lot of talk of SOHO exploitation but little evidence of it until now,” he said. “One point to call out is that IoT exploits have been far more actively traded in the offensive market since the onset of COVID.”
John Bambenek, principal threat hunter at security and operations analytics firm Netenrich Inc., warned that the problem with SOHO routers is that cost-conscious users often buy them, they lack robust security features and no one actively administers them so they never get patched or hardened.
“ZuoRAT’s targeting of SOHO routers makes it more threatening than anything else,” Bambenek explained. “Its feature set is similar to those you’d use in an advanced attack, but it is built for devices that likely have little in the way of defenses or detection capability.”
THANK YOU