 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Cloud content delivery provider Cloudflare Inc. disclosed Tuesday that it was targeted by an attack similar to the one that breached Twilio.
Cloudflare said that some of its employees did fall for the attack, but it confirmed that none of its internal systems were compromised due to its own security technologies.
The hackers used what is called a social engineering or phishing attack. That’s when attackers craft text or email messages designed to trick an individual into giving up some kind of secure information. In this case, the attackers were seeking login credentials.
“This was a sophisticated attack targeting employees and systems in such a way that we believe most organizations would be likely to be breached,” Cloudflare’s Chief Executive Matthew Prince wrote, along with team members Daniel Stinson-Diess and Sourov Zaman.
The attack occurred swiftly and in less than a minute at more than 76 employees received SMS text messages on their personal and work phones. Some family members also received messages. The company said it has yet to determine how the attackers compiled a list of employee phone numbers.
In its post-mortem, Twilio said that the attackers were also sophisticated enough to match employee phone numbers to names.
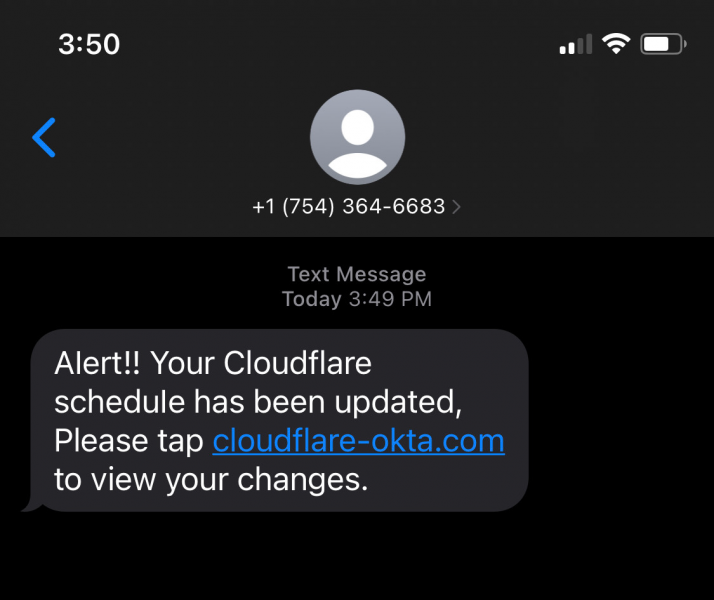
Employees who clicked on the link in the SMS phishing messages were taken to a fake Okta login page that was designed to steal employee login credentials and a generated Time-Based One Time Password. A time-based password works a lot like it sounds: A user receives one from a service that lasts a short period of time – often less than a minute – creating a type of two-factor authentication.
However, Cloudflare does not use time-based passwords; instead, it uses security codes generated by FIDO-2 complaint hardware keys from a vendor similar to YubiKey. This is a physical device with its own security token stored within it.
“While the attacker attempted to log in to our systems with the compromised username and password credentials, they could not get past the hard key requirement,” the Cloudflare team said.
Although the hackers’ intent was to steal credentials and gain access to the backend systems. The security team at Cloudflare further examined the attack progress and discovered that it was even more nefarious.
Once the credentials and TOTP code were entered, the page would then download remote access software called AnyDesk. Once installed, this would allow the attacker control of the victims’ machines without their knowledge. Cloudflare’s security team confirmed that none of the company’s employees made it to this step.
After thwarting the threat, Cloudflare determined the three employees who were affected and reset their credentials. The team then blocked any potential further attacks and reached out to other organizations, including Twilio, with additional information.
“Even though the attacker was not successful, we are making additional adjustments from what we’ve learned,” the team said. “We’re adjusting the settings for Cloudflare Gateway to restrict or sandbox access to sites running on domains that were registered within the last 24 hours.”
THANK YOU