 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Google Cloud said today it fended off what it believes was the largest Layer 7 distributed-denial-of-service attack ever seen, when an attacker attempted to disrupt one of its customers’ internet based services on June 1.
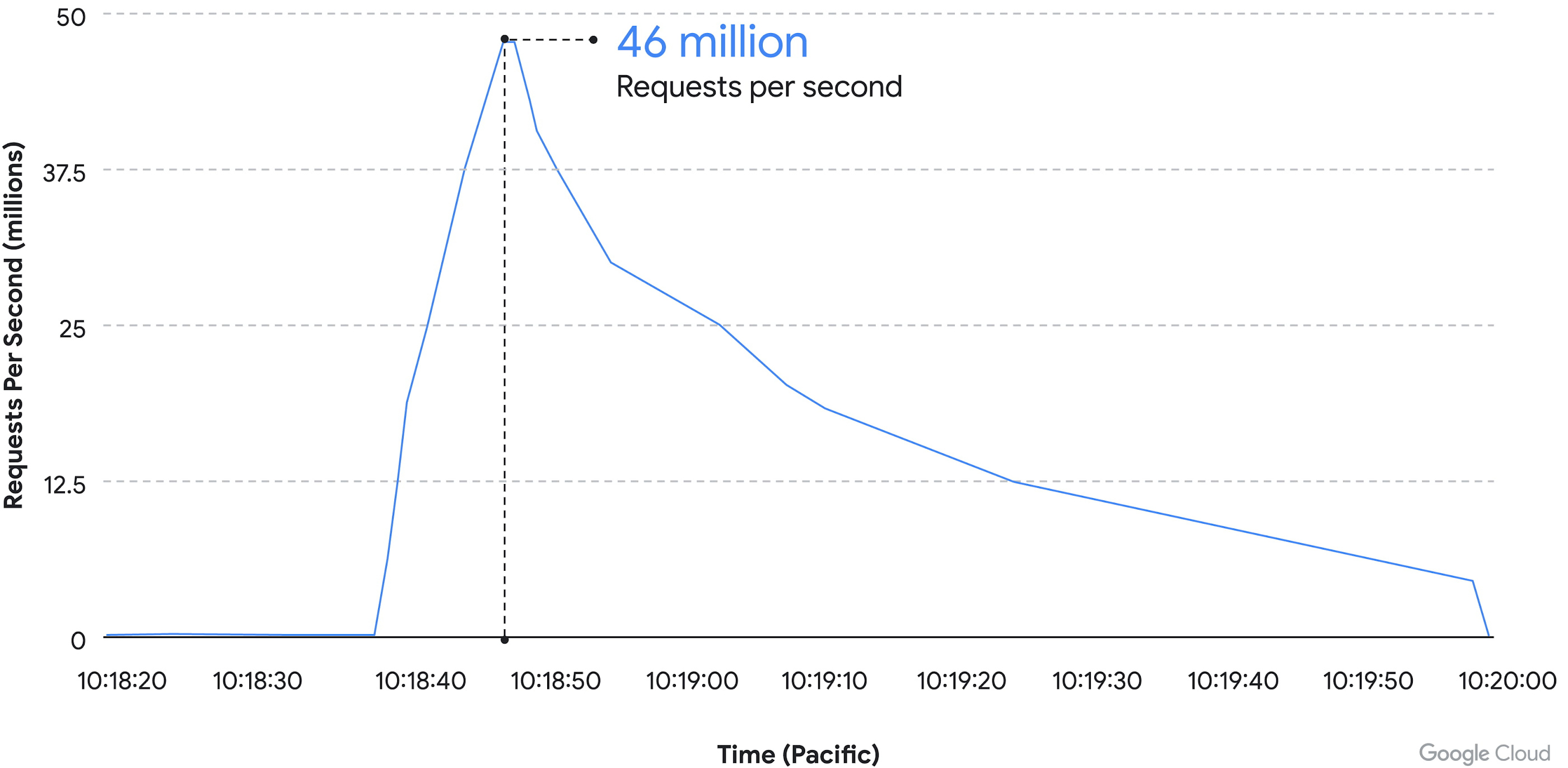
The DDoS attack peaked at a stunning 46 million requests per second using Hypertext Transfer Protocol Secure-based requests. “To give a sense of the scale of the attack, that is like receiving all of the daily requests to Wikipedia in just 10 seconds,” Google Cloud product manager Emil Kiner and technical lead Satya Konduru wrote in a blog post describing the incident.
Google added that the attack was 76% more powerful than the 26 million RPS attack that was encountered by Cloudflare Inc. during the same month, which had been regarded as the largest to date.
DDoS attacks are used by malicious persons or entities to take websites and applications offline. They do this by bombarding a service with millions of requests performed by bots. The June incident first kicked off with an assault that began with about 10,000 requests per second, before escalating to 100,000 RPS around eight minutes later.
Google Cloud’s anti-DDoS Cloud Armor immediately burst into action, generating an alert that enabled it to start blocking the malicious web traffic. “In the two minutes that followed, the attack began to ramp up, growing from 100,000 RPS to a peak of 46 million RPS,” Kiner and Konduru wrote.
Despite the massive escalation, the attackers were unable to disrupt the customer’s services, Google said.
“Since Cloud Armor was already blocking the attack traffic, the target workload continued to operate normally,” the employees wrote. “Over the next few minutes, the attack started to decrease in size, ultimately ending 69 minutes later at 10:54 a.m. Presumably the attacker likely determined they were not having the desired impact while incurring significant expenses to execute the attack.”
Google said that an investigation has led it to believe the DDoS attacks were perpetrated by the Meris botnet, which is made up of hundreds of thousands of infected internet modems and routers, many of which were sold by a company called MikroTik. It’s said that the botnet was created due to a vulnerability in MikroTik’s products that enables hackers to remotely control those devices.
The Meris botnet has been linked to a number of other high profile DDoS attacks in recent times, including a 22 million RPS attack against the Russian search company Yandex LLC last year. That was a powerful attack itself, but the recent assault uncovered by Google shows the Meris botnet has the ability to generate much more firepower. However, it remains to be seen if it has enough to take on Google’s Cloud Armor service.
Kiner and Konduru explained that Cloud Armor has the ability to establish a baseline model of normal traffic patterns for each customer’s website. It also has a rate-limiting capability that enables customers to carefully throttle malicious traffic while allowing legitimate requests to interact with the service as normal.
Constellation Research Inc. analyst Holger Mueller said that just as enterprises use the cloud to scale their business operations, so to can nefarious actors use it to boost their own illegal activities. As a result, cloud providers like Google Cloud need to come up with a way to protect their customers from these more powerful attackers.
“DDoS is a common way to attack websites and it’s good to see Google was able to thwart what is, so far, the largest such attack on record,” Mueller said. “What’s encouraging is that Google’s software also helped to identify the signature of the attack and was able to suggest rules to defend the Google customer. Google Armor scaled with software, as this is the only way to counter a software-driven attack. It is highly unlikely that the on-premises team of an enterprise would have been able to react as quickly and effectively, and that’s something executives may want to note.”
The failed attack is obviously a great advertisement for Google’s Cloud Armor service and it comes at a time when enterprises may show more interest in DDoS attack protection. A number of recent reports show that DDoS attacks have become more commonplace this year. For instance, Radware Ltd. said in a threat analysis report earlier this week that it saw a 203% increase in DDoS attacks against its customers in the first six months of the year, compared to the same period a year earlier.
The security firm AO Kaspersky Lab said in April that it believed DDoS attacks hit an all-time high in the first quarter of the year, increasing by 46% from the previous quarter. Both Kaspersky and Radware said Russia’s invasion of Ukraine has played a major role in the increase in DDoS attacks this year.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.