 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
With an increasing number of threats to business security and the growth of application programming interface traffic, Google LLC’s cloud division today announced an API abuse detection dashboard powered by machine learning algorithms.
The new feature extends Google’s Apigee Advanced API Security dashboard and focuses on business logic attacks because they are notoriously difficult to detect and defend against. That’s because they tend to target APIs that are used for intellectual property, business processes and sensitive information, such as products, user data, the listing of goods and financial data.
“Organizations in every region and industry are increasingly producing and consuming APIs because they enable easier delivery of services and data in the digital environment,” Shelly Hershkovitz, a product manager at Google Cloud, told SiliconANGLE in an interview. “Because of that the API usage and traffic volumes have grown. For example, the volume of API traffic processed by Apigee over Black Friday and Cyber Monday has grown year-over-year for the past three years and between 2021 to 2022 it had an increase of 35%.”
With this increased traffic, there has also been a requisite increase in disruptions and security threats to APIs. The latest Google Security Research Report from Google Cloud noted that 50% of surveyed organizations suffered API security incidents in the past 12 months, and of those 77% delayed the release of new services and applications as a result. These incidents can be costly as well, according to a 2022 report from Imperva, which found that insecure APIs cost global organizations between $41 to $75 billion annually.
“We are focusing on business logic attacks such as scraping and anomalies,” Hershkovitz said.
One big example of an API scraping attack came out in 2021 when it was revealed that the information of 530 million Facebook users had been made publicly available on the dark web, the shady corner of the internet reachable with special software. At the time, Facebook revealed that this information had been gathered by “scraping,” which is where an attacker uses otherwise legitimate access to an API to download large amounts of sensitive amounts of data from it.
Ordinarily, this sort of behavior can be blocked using rules that limit the number of queries that can be made at a time from a specific internet address or API key in order to stop potential attacks. However, attackers can get clever by using multiple bots, internet addresses and more to sneak around rules and safeguards.
The same can be said about anomalous or deviant traffic attempting to subvert an API to gain escalated access and break into the network in order to modify or change the data that it outputs to other users. That’s particularly dangerous because it might be even more difficult for monitoring software to detect and the effects could be devastating, especially in regulated industries such as finance.
“The new machine learning models that power our Apigee API abuse detection have been trained and used by Google’s internal teams to protect some of the company’s public-facing APIs,” Hershkovitz said. “So now we’re bringing them into Apigee for our customers to better secure and protect their APIs.”
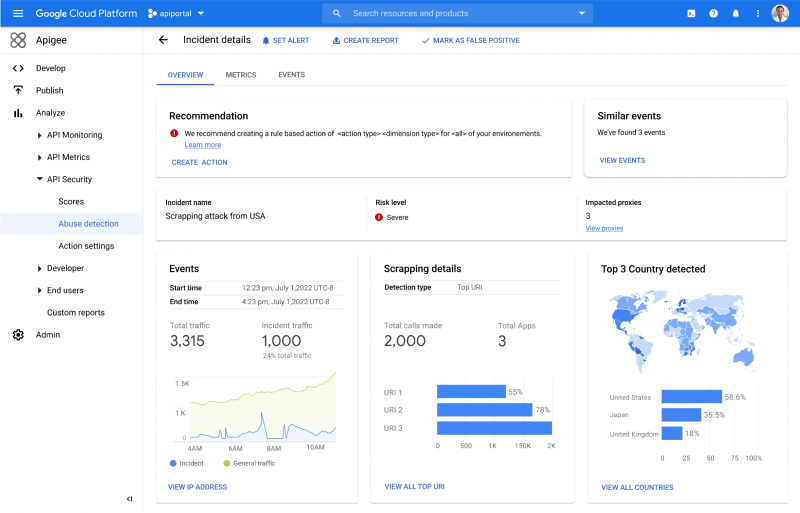
The models have been trained on years of traffic and based on best practices for threat detection, giving them the best possible ability to detect and model what should and shouldn’t be happening for API traffic. It is especially adept at sifting through alerts designed to detect less sophisticated attacks, which can generate a high volume of alerts, many of which are not critical, or helping to deal with a large number of bot attacks at once, which can help teams deal with the biggest problems faster.
In the dashboard, the machine learning-powered abuse detection algorithm will also surface critical events with “human-friendly” titles that attempt to capture the essential elements of the attack such as the source of the attack, the APIs affected and the duration of the attack so security teams can deal with the event faster.
The dashboard also provides a way to drill down into the attack and ways to cross-reference with other similar attacks along with recommendations on actions to remediate the event as quickly as possible.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.