 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
We seem to be in a trust deficit these days, as breaches – especially among security tech companies – continue unabated.
Ransomware attacks now have spread to data hostage events. The shady corner of the internet known as the dark web is getting larger and darker, with enormous tranches of new private data readily for sale and criminal abuse. We have social media to thank for fueling the fires of outrage, and now we can self-select the worldview of our social graph based on our own opinions.
And when it comes to data insecurity, various breaches and threats seem to make working and playing online more dangerous every day. There’s the cavalier approach with which Google LLC and Meta Platform Inc.’s Facebook continue to deal with user data. Then there was the breach by Chinese hackers of Equifax in 2017 that exposed nearly 150 million private data details, T-Mobile’s two breaches disclosed in January and May this year and several more that go back to 2018. Even the current tech darling ChatGPT was hit in March. Perhaps most ironic, Norton’s LifeLock, which supposedly protects your private data, was breached in January with more than 6,000 customer details leaked.
“Today’s most prevalent technologies make things less trustworthy,” Ted Gioia, a music blogger and podcaster, said recently in this podcast. “I look at a world in which there’s no shortage of information, but the real shortage is trust.”
Figuring out whom we can digitally trust – and fighting this trust deficit — is a hard problem. The security training association ISACA’s annual digital trust report, which came out earlier this week, surveyed more than 8,100 corporate security professionals who are either members of the association or who have taken one of its numerous certification courses, and it wasn’t pretty.
“Digital trust can be the difference between retaining reputations and customer loyalty after a major incident or suffering serious, time-consuming and expensive losses,” the authors write in the report’s introduction. But those bromides aside, the report is worth reading for its Cassandra-like warnings. For example, only 24% of the respondents are planning to increase budgets for digital trust activities. Even fewer say that their organization has a dedicated staff role for digital trust. And although the majority of respondents say it is important to have a framework for digital trust practices, only 20% currently use one.
Perhaps the most curious result is that 34% of the respondents say they do not currently but will likely have a chief trust officer, or director of digital trust, in the next five years. It is curious because this position seems to be on the way out in terms of trendy CXO-style executive labels, even though various high-tech firms such as SAP SE, Salesforce Inc. and Autodesk Inc. currently have chief trust officers. Some, such as Tom Patterson, who was the officer for Unisys Corp. for seven years, is now the managing director for emerging technology security at Accenture PLC. Others have had shorter tenures.
Back in 2017, Drew Nielsen asked if it was time for a chief trust officer to stake out an office on the executive floor and offer a better understanding about a company’s data as well as be a very visible data privacy champion. Ironically, he didn’t last long in that role for Druva Inc., and since then he has worked in various product marketing positions. “My position was to be more public facing and a broader role than security and compliance,” he told SiliconANGLE. He also pointed out that the typical CISO is mostly an internally-facing manager, but managing trust requires a more public focus.
Others who were initial pioneers of the position have taken other jobs in the years since then, according to anecdotal research on LinkedIn. And a search for the position on Glassdoor didn’t yield many results. Perhaps having a chief trust officer is more of an internal promotion than a hire from outside the organization. Or perhaps it is just on the way out as an actual executive position.
The security firm OneTrust LLC wrote in an undated but most likely old blog post that “in some businesses, a chief trust officer is a next-step evolution of a chief privacy officer, chief data officer or chief information security officer (CISO). In others, trust isn’t managed by a single person, but by bringing together groups of individuals across the company focused on building and sustaining trust.”
It hasn’t quite worked out that way. Drummond Reed is the director of trust services at Gen Digital Inc., the company that combined the security portfolios of Norton LifeLock Inc. and Avast plc. Many years ago, he held the title of chief trust officer at another acquired firm that supplies digital identity products.
“The title made a lot of sense years ago, but I haven’t seen many more of them recently,” he told SiliconANGLE. “Certainly, digital trust continues to be a hot topic, and should be more of a focus for organizations. It really should be a standard measure of success for numerous departments such as security, privacy and marketing.”
And that is part of the problem: Trust may be managed by multiple executives. That’s because trust cuts across so many different departments of a typical organization: security and breach response, customer relationships, and employee hiring and retention. Having a chief officer for trust means supervising both inward- and outward-facing departments, and trying to coordinate people who don’t normally collaborate with each other.
To that point is Eric Handy’s experience, who was the chief trust officer for two years at defense contracting firm Davidson Technologies Ltd. before recently leaving to seek new opportunities. “A lot of folks don’t understand what the job is, more so when it comes to internal responsibilities,” he told SiliconANGLE. “But I had P&L responsibility to manage our AI, data analytics and quantum computing departments, which we were just standing up then. My title really helped open a lot of doors, and I am glad that our board and CEO had the insight to improve our trustworthiness with these new products.”
This means that maintaining trust is really trying to manage a fragile and nonrenewable resource. It is fragile, because the actions of just one individual can destroy trust. Look at what happened earlier this year with 3CX Ltd. One person downloaded one piece of malware and disrupted two software supply chains. That one event drained the company’s trust reservoir, which will take some time to regain and refill.
Just like the energy conservationists promote moving to more renewable and resilient energy sources, organizations must do the same with promoting better trust-maintaining technologies. These include better authentication, better red team defensive strategies and better network governance. Even in the tech business, these are often the jobs of different teams, both inside and outside the information technology department.
Another issue is AI and large language models. “AI’s role with trust is a topic mentioned everywhere I go,” Reed said. “But AI could do as much to both improve and destroy trust. I think in the short term, AI erodes trust, so organizations will have to work harder and need to do a better job to verify identities, content, everything.” Gioia agrees: “The most obvious example of a trust problem right now is AI,” he says. “The model is based on training the AI on people who just spread disinformation.”
Mark Thomas of Escoute Consulting was quoted in the ISACA report saying, “Developing an independent, publicly available digital trust score for organizations is important.” To that end, Reed suggests that organizations develop a special “trust net promoter score” similar to the one used for rating customer satisfaction.
One effort along these lines was announced this week by the Linux Foundation, called Trust over IP. The initial press release says it’s setting up a separate foundation to create a global trust standard that will “use digital identity models that leverage interoperable digital wallets and credentials and the new W3C Verifiable Credentials standard to address these challenges to better manage risk, improve digital trust and protect all forms of identity online.” That is clearly a tall order, and it has already set up a series of working groups to develop the protocols (below) and governance pieces.
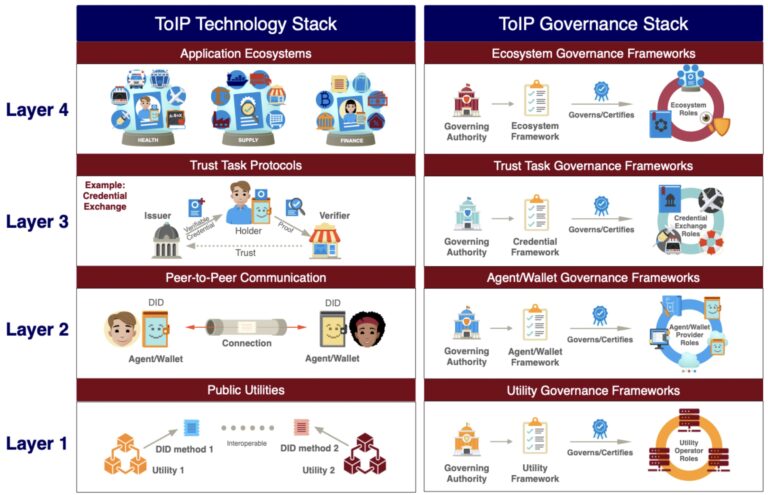
In the meantime, consulting firm Deloitte Touche Tohmatsu Ltd. has a five-point plan for increasing trust, including a more precise definition for your particular business circumstances, communicate how you will intend to build a trust-preserving culture and putting dynamic measures in place. But even it admits, “Companies are still only in early stages of adopting these strategies.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.