 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Just this past week, ransom attacks have hit a major Spanish bank, a Canadian university and a legal software-as-a-service platform. So it’s good timing that two reports released in the past month from IBM Corp. and Amazon Web Services Inc. are providing guides to how to combat the terrible tide.
Although the raw number of ransom-based attacks seems to be on the wane — Avast Software s.r.o. reports a slow decline in the first quarter from a year ago, for example — the criminals aren’t giving up such a lucrative effort. IBM found that ransom amounts have skyrocketed to the hundreds of thousands of dollars.
That reflects a switch in tactics to more targeted attacks such as the Vice Society group, which is focusing on manufacturing businesses. This group is also using novel automation techniques to steal data, something that also appears to be increasing. It’s what IBM calls a blended attack because it combines the ransom, which may or may not be paid, with an extortion demand for payment to stop the data leak, plus a third threat of a potential denial-of-service attack. Black Fog Inc. in its latest report found that almost all ransomware attacks now involve extortion and data theft.
The IBM “X-Force Definitive Guide to Ransomware 2023” touches on tactics and is based on examining their customers’ anecdotal incidence response data as part of the company’s X-Force security practice. It found that in the past year, “the average time to complete a ransomware attack diminished from two months to fewer than four days — giving organizations very little time to detect and thwart potential attacks.”
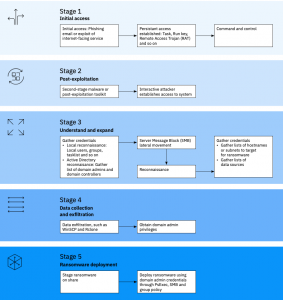
Image: IBM
IBM has developed a useful five-stage outline (pictured, adjacent) of a typical ransomware attack two years ago and it’s now included in its report this year. These stages include the initial access, typically a phishing lure, followed by a probe using some remote access software, then exploration of the larger network to harvest access credentials.
Then there are the last two steps: collecting private data and then deploying the actual malware. Having this model “can help analysts identify logical control and detection opportunities to better recognize ransomware attacks,” the report stated.
John Dwyer, who is the head of research for IBM Security X-Force and one of the report’s co-authors, told SiliconANGLE that zero-day or unpatched attacks, such as the MOVEit exploit that was recently discovered, allow attackers to skip directly to stage four, which is one reason why it’s important for defenders to pay attention to these exploits. “We all need better situational awareness, even when we are reading our personal email boxes, because that could be the next enterprise access vector,” he said.
One of the new attack methods is what IBM calls email thread hijacking, which saw double the number of attempts in the past year. It involves “attackers posing as the original participant use compromised email accounts to reply within ongoing conversations.” The idea is that the threaded view can hide a potential bad actor among the legitimate replies.
IBM’s report has plenty of concrete suggestions on how to reduce the potential damages, One is to use what it calls a domain sinkhole. “This allows an organization to redirect domains to a specific internal server that can provide advisories to users who attempt to go to blocked sites,” the report explains. “The sinkhole can also provide real-time notifications when computers attempt to reach risky domains.”
Another suggestion is to ensure that all default passwords are changed, and that regular checks across the entire infrastructure ensure that this is done. IBM also recommends disabling Windows Script Host on all endpoint Windows computers,to prevent the chances of a malicious script starting the ransomware cycle.
Finally, planning is critical. “Having plans in place and a staff trained on the response plan can help reduce the time to recover and save an average of $1M of the total cost of attacks,” the report states.
The “AWS Blueprint for Ransomware Defense,” not surprisingly, is AWS-specific, highlighting the relevant specifics of dozens of AWS security-related services to help repel an attack.
For example, there are instructions on how to setup AWS Shield, which is used to stop denial-of-service attacks. There’s also Guardduty, which is used to detect malware. And there’s Macie, which is used to discover sensitive data and enable automated protection.
Part of the challenge of using cloud services — and especially AWS — is that there are so many different services to track and deploy properly. For example, there is Control Tower, which is used to set up CloudTrail for logging data events that are recorded in CloudWatch, among other logging services. The services are mapped against 40 recommended security controls from the Center for Internet Security Critical Security Controls document.
Although one might think having this mapping is helpful, it also makes the AWS report less readable and actionable. The authors say that the report can help organizations find gaps in their security knowledge, but instead it illustrates how far organizations have to go to educate their staff with the various AWS security arcana.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.