 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
We’re finally inching closer to curing our addiction to passwords.
This week the FIDO Alliance put together an online event and posted a series of white papers to try to help businesses that want to move forward with passkeys — digital credentials that don’t require usernames and passwords — to host their first 12-step programs for ridding themselves of the scourge that results in huge holes in cloud cybersecurity protection.
“Passkeys are a superior password replacement,” said Tom Sheffield, senior director of cybersecurity for Target Corp. “And you shouldn’t wait to implement them in your business.”
Target is one of the early passkey implementers. If more reminders of the perils of passwords are needed at this point, consider this statistic from HYPR’s “State of Passwordless Report: ”Push-bombing MFA attacks are more than double what was reported last year, hitting 28% of those surveyed.” Last year, SiliconANGLE wrote about this attack method, which involves sending multiple SMS text push alerts to a phone requesting the owner’s multifactor authentication code.
So what has changed since May, when SiliconANGLE wrote about the latest passkey developments?
First, there is more clarity about the two different types of passkeys that are available. Second, there are some concrete suggestions on how enterprises can successfully deploy them. And finally, we have actual experience now with using them to secure Google Workspace customers.
Passkeys come in two different flavors: “synced” and “device-bound.” These accounts for a variety of usage modalities, security parameters and the way enterprises will ultimately manage their passkey collections.
The former can be backed up and used across different devices, such as having a digital passkey on an iPhone, which can be used to log in to a Chrome browser session on a Windows desktop. The synchronization occurs thanks to a cloud service, for example Apple’s iCloud or 1Password’s cloud. The latter type includes those passkeys that are attached to a particular piece of hardware, such as Yubico USB keys or storing passkeys on a phone’s trusted hardware chipset.
The FIDO white papers go into lots of details about the two types, and they were also described by many of the event’s speakers. This is both the challenge and the promise of FIDO: It always seems to have multiple standards and processes. Although passkeys represent progress, understanding the fine print will take some study. FIDO may stand for Fast Identity Online, but implementing all this will be anything but fast.
“Not all passkeys are created equal or have the same security parameters,” said Dean Saxe, a senior security engineer for Amazon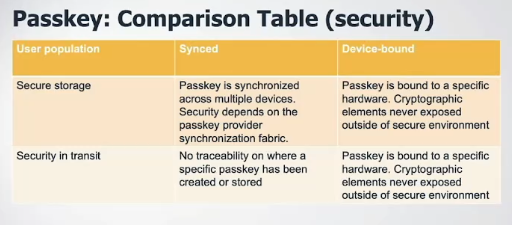 Web Services Inc. The adjacent diagram summarizes the major security differences with respect to securely storing the passkeys and how they are used. And, as Sheffield mentioned during his talk, “the threat landscape changes with synced passkeys, because these open up a dependence on passkey providers’ internal security and how they implement end-to-end encryption.”
Web Services Inc. The adjacent diagram summarizes the major security differences with respect to securely storing the passkeys and how they are used. And, as Sheffield mentioned during his talk, “the threat landscape changes with synced passkeys, because these open up a dependence on passkey providers’ internal security and how they implement end-to-end encryption.”
Most businesses will probably need both types of passkeys, depending on their ultimate usage and application. For example, the more secure on-device keys are appropriate for financial staffers who handle funds, while the sync keys are useful for users that are running multiple apps on multiple devices.
That brings us to the actual customer case studies mentioned during the FIDO event by Jay Roxe, the chief marketing officer of HYPR, a passkey and identity provider. They illustrate how difficult the path to passkeys is but also shed light on how to traverse that path.
He cited one customer that’s a 1,500-employee organization spanning 100 countries. It was using a single-sign-on solution supporting 250 different apps. “This is a sales and marketing job to get passkeys deployed across this business,” Roxe said. “You have to juggle budget, training and marketing internally at the same time.”
It held numerous internal marketing campaigns and offered cheap swag as prizes for early adopters. The company also made the decision to roll them out first to its information technology and finance departments.
Another HYPR customer had 70,000 employees spread across every country in the world. It would take up to three weeks to onboard a new staff member and wanted to reduce this time and enhance its security. “But we had to help create the marketing campaign for each geography based on a different rationale – the ‘why’ behind passkeys – to be effective,” Roxe said.
It was a long slog to get front-line managers engaged, but as he quoted one of them, “I’m so embarrassed that I waited so long to register for my passkey, it was quicker than brushing my teeth.” Roxe was quick to sing FIDO’s benefits, saying that FIDO can provide a choice of authenticators. The trick is figuring out how those choices are presented to each user and understanding each particular circumstance.
One of the bigger challenges has to do with replacing older and less secure MFA methods, such as sending SMS codes, with passkeys. It might seem that businesses with a lot of existing MFA would be low-hanging fruit for FIDO passkeys, but no. The problem has to do with installing the authentication infrastructure that can handle all the various use cases, and that means in some situations making modifications to various applications and identity managers that are already in place.
“Replacing MFA has to be done carefully and perhaps slowly app by app,” said Target’s Sheffield. Added Jerome Becquart, the chief information security officer for passwordless identity management firm Axiad IDS Inc.: “Don’t try to remove all passwords all at once. In other words, don’t boil the ocean.”
One alternative is to step away from MFA entirely, which is what Thi Nguyen-Huu, chief executive of data security firm WinMagic Inc., told SiliconANGLE. “If you are talking MFA replacement, you are moving in the wrong direction. As long as you can assess your endpoint properly, you don’t have to think about MFA or anything else.”
He demonstrated the company’s solution at the FIDO event. Of course, that means using WinMagic for all passkey-related authentication, something that might not be possible in more complex legacy environments.
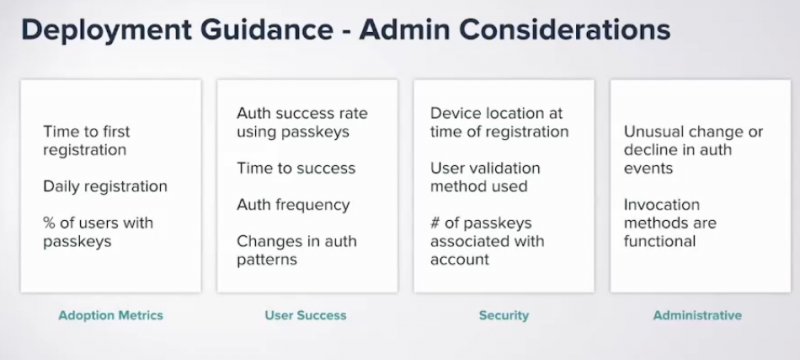
Jing Gu, a senior product marketing manager at Beyond Identity Inc., had very specific recommendations for passkey deployment. They include carefully documenting all the various operating system and browser combinations before any rollout.
She also suggested a variety of actions to integrate passkey registration into the overall employee onboarding workflow, including using self-serve registration, preprovisioning new devices if at all possible, and providing tons of support and troubleshooting. The FIDO Alliance has put together its passkey journey page to help organizations keep everything straight.
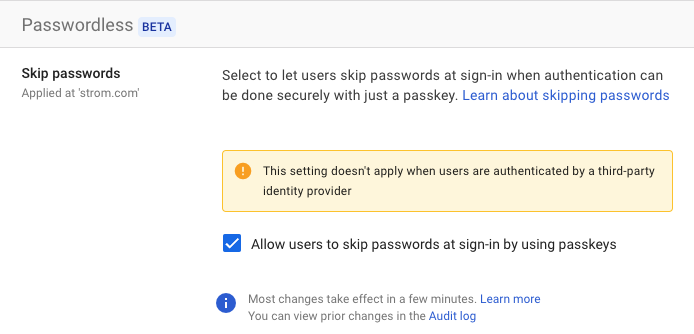
Finally, I can describe my own passkey experience with my Google Workspace account. My biggest frustration was waiting for Google to enable the feature on my workspace, which can be found in the Admin Security control panel (below). It’s a simple check box surrounded by lots of informational warnings.
 Once enabled, you are asked when you sign into your account if you want to choose a passkey saved on your particular device. I first put a passkey on my mobile phone. There was one hiccup, in that I didn’t have Bluetooth enabled when I was doing this. Sheffield mentioned this issue during his talk.
Once enabled, you are asked when you sign into your account if you want to choose a passkey saved on your particular device. I first put a passkey on my mobile phone. There was one hiccup, in that I didn’t have Bluetooth enabled when I was doing this. Sheffield mentioned this issue during his talk.
When I wanted to login to my account from my desktop, I was shown a QR code that I would scan with the phone to read the key. Once I stored another passkey on my desktop, the login happened seamlessly.
Notice the role of the QR code to sync the passkeys across devices. That could be an issue, and one of the reasons why sync passkeys aren’t as secure as the ones stored on a Yubico USB key. Although no one has yet exploited a passkey QR code, there have been previous attempts by hackers compromising other codes, as this 2022 alert from the FBI mentioned.
If organizations don’t want to plow through the multiple FIDO papers linked at the top of this post, or if all this makes their executives’ heads spin, here is one suggestion: Start with a good introduction to passkeys, such as this explanation by WinMagic.
Next, consider a software development kit or FIDO server from any of the providers listed here. These kits can help move along your passkey project without you having to reinvent the authentication wheel from scratch.
Passkey implementation clearly won’t be easy. Every business situation has its own set of limitations, identity configurations and authentication oddities, and application and user collection that makes any general deployment recommendations nearly impossible.
But the promise of kicking the password habit and moving into the modern era where access to applications and data can be better secured is worth the pain involved during the journey to get there.
“There is a path forward for every business to adopt passkeys,” said Sheffield. You just have to create and then navigate your own particular one.
(Disclosure: The author has consulted with the FIDO Alliance in the past.)
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.