 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The foundational Domain Name System, essentially the phone book for the internet, used to be something nobody using the net much noticed, but lately it has become more of a target, and the cost of attacks against it are huge and growing.
Recent events have once again brought issues involving the DNS, as it’s called for short, to the forefront. A new kind of denial-of-service attack called Water Torture is the most recent, but earlier this year has seen other DNS-based attacks on Telsa’s network in January and a new malware toolkit called Decoy Dog that targeted business networks.
One reason has to do with the expansion of the internet. There are more targets, more bandwidth and more automated tools to launch attacks, making it easier for the bad guys to cast a wider net with more destructive power.
The DNS protocol is essential to almost every internet service and is used to translate alphabetic domain names, such as SiliconANGLE.com, and a set of numerical internet protocol addresses, such as like 35.91.118.127, back and forth so that they have meaning both for humans and for machines and software.
Remember printed phone books? If you know the alphabetic name, you can look up the numbers. DNS has been around for decades, dating back to when Paul Mockapetris, now chief scientist at ThreatSTOP Inc., wrote numerous internet protocol standards back in the 1980s.
Back then, IP networks had very different roles for people and machines, which made DNS the intermediary. That worked for a time when a device was mapped to an IP address. That time also had mostly on-premises computers, so keeping track of things was much simpler. Typically, the keeper of each corporate DNS was a single person, who didn’t have a lot of demands or changes to make.
Those days are so over now, especially as the internet has “shifted to a client/server network model, where clients initiate connections and servers respond, and clients don’t require a permanent assigned address,” as Geoff Huston wrote in a 2020 post on the evolution of DNS. Huston is chief data scientist for Australia’s internet agency Asia Pacific Network Information Center and has written extensively on DNS issues.
This shift, especially as superclouds, containers and multiple application collections create and destroy virtual instances millions of times a day, puts tremendous stress on the DNS infrastructure. Without a fully functioning DNS, the workloads and workflows can easily get in trouble: packets disappearing or dropped, malicious software supply chains taking control, and web servers brought down, requiring restarting or, worse, rebuilding before they can return to production.
All that means organizations depend on DNS more than ever to connect the various computing bits and pieces across the internet, which makes it very noticeable when DNS gets in trouble — and for many businesses, this does happen sometimes. DNS has become the great hacking playscape where network infrastructure can be compromised with just a few packets, and exploits are regularly found. And with millions of malicious domains being created each month, as was recently reported from Akamai Technologies Inc., there is a lot of potential network traffic from victims that could be directed by an attacker’s DNS.
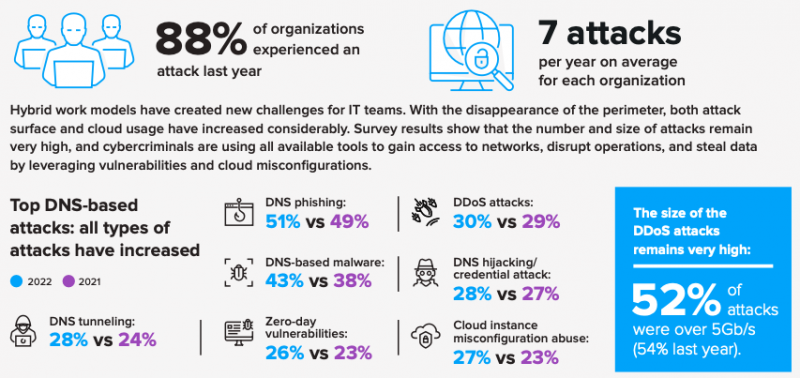 The cost of a DNS attack is huge. In a study from last year by IDC (summarized in the adjacent graphic), 88% of organizations have experienced one or more DNS attacks on their business, with an average of seven per year. Each successful attack costs the business, on average, $942,000.
The cost of a DNS attack is huge. In a study from last year by IDC (summarized in the adjacent graphic), 88% of organizations have experienced one or more DNS attacks on their business, with an average of seven per year. Each successful attack costs the business, on average, $942,000.
And “no DNS means no business is conducted,” the report concludes. The Facebook seven-hour network outage experienced in October 2021 cost the company at least $60 million in lost ad revenue, and its stock price dropped 5% as a result.
Perhaps one of the more complex and compound exploits was seen in 2021. Called NameWreck, it involved a series of nine vulnerabilities affecting four different TCP/IP protocol stacks, including flaws uncovered in two critical remote code execution issues in Nucleus NET and FreeBSD and a denial-of-service flaw in NetX. These flaws would enable attackers to take control of millions of different devices running these operating systems.
Huston’s 2020 blog post covers several factors that have changed with DNS, and one of the most important is trusting what it says when it performs its address lookups. He catalogs the ways that DNS is used to lie about these lookups for various reasons, and some of these lies take the form of several different kinds of DNS-based attacks. Each one has a slightly different set of circumstances:
To prevent these attacks from happening, network engineers have implemented a variety of DNS-based security methods. Sadly, all of them have their issues and have not met with anything near universal acceptance. IDC’s report says that almost every company has some form of DNS security, but almost half of them don’t use them, and a quarter of the respondents don’t collect or analyze their DNS traffic logs. So what are the options?
DNS Security Extensions or DNSSEC, which was first proposed in 2010, added cryptographic signatures to help verify DNS responses were coming from the intended servers. Although the authentication was useful, it didn’t protect the privacy of the DNS conversation. And to make matters more troubling, attackers figured out back in 2016 how to leverage DNSSEC as a way to amplify DDoS traffic.
DNS over HTTPS, or DoH, and DNS over TLS send these requests over the UDP transport layer, again using encryption. This prevents man-in-the-middle tampering that could be done with unprotected DNS conversations. The TLS version skips the application-layer protocols, which helps hide this traffic even further and offers a slight performance boost as a result.
The DoH protocol came about a decade ago, largely in response to Edward Snowden’s disclosures. “They were a way to prevent interference or eavesdropping by internet providers and by government security agencies,” Vixie told SiliconANGLE. “But it also had the unintended consequence of trading off privacy of some users against the safety of users,” he said. He predicted that DoH protocol will have broad impact “because it disintermediates parental controls and company DNS policies.”
DNSCrypt was designed to prevent DNS spoofing attacks and has several open-source implementations.
What all of these newfangled methods have in common is that they don’t completely solve the problem. They just reveal more precisely what piece of an organization’s DNS infrastructure has been or could be compromised by a hacker, so they can be better prepared to resolve any issues from a potential DNS compromise.
One improvement is for organizations to outsource their DNS to what is called an open DNS resolver. These are for the most part free services, although some of them also have paid plans.
They bundle in different security protocols and have different analysis methods that can prevent malicious traffic from entering the network, such as by setting up geofencing to prohibit traffic from questionable places or networks. They use catchy IP addresses to make them easier to remember, such as 1.1.1.1 from Cloudflare Inc., Google LLC’s 8.8.8.8 and Quad9’s 9.9.9.9. Some of these services also offer load balancing and content proxying services along with the DNS security and some have extensive worldwide networks to reduce network latencies, which is a side benefit of using them.
Open resolvers are a good first step at protecting network infrastructure, but even the more complete paid plans from these vendors still require additional tools and methods to truly protect it.
Vixie has often argued that information technology managers could be more proactive at defending their networks if they would monitor what’s happening across their DNS infrastructure. One way to do this is to make better use of cloud-managed DNS providers, something covered in this article in CSOonline.
All three of the major cloud platforms — Microsoft, Google and Amazon Web Services — have their versions of managed DNS services, along with many other providers. The CSO post goes into details about why the cloud is better for DNS protection, and where it falls short. Because these providers watch over a larger network traffic volume, they can spot trends and potential exploits sooner and stop them faster – at least in theory.
Switching DNS providers isn’t just done for security reasons, but also to deliver real performance gains in terms of reducing network latency and web content load times. This becomes more difficult to anticipate, especially if an organization is running a global server network or delivering content to a global audience. Fortunately, there are a number of tools that can test these parameters from various geolocations, as compared by Geekflare in this review.
DNS can also help in other areas. “Everyone knows that DNS protection is effective against malware,” DNS inventor Mockapetris told SiliconANGLE. “But it is also effective in protecting you from being liable for U.S. government fines for violating export controls and trade sanctions,” such as what happened to Microsoft this past spring when it was fined $3.3 million. “And they voluntarily turned themselves in too!” He pointed out that Amazon has web application firewalls that can help automatically block noncompliant DNS traffic, since the government makes regular changes to its sanctions list.
What’s next? Huston envisions a two-tiered DNS. He says in his 2020 blog that “DNS as we know it may end up as a small set of high-end luxury boutique activities that make a feature of the luxury of custom procedures to manage persistent names.”
That would mean the rest of DNS would be more of a commodity utility. “It may be,” he notes, “that the DNS has nothing to do with human names any more and more to do with its property of one of the few universally supported protocols and services left in the internet.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.