 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A group of British cybersecurity researchers has figured out a novel new attack method: recording the sound a computer keyboard makes.
The researcher took recordings using a nearby smartphone of typists and used it to train a sound classification model, achieving accuracies of 95% to suss out the actual keys pressed.
They call this an acoustic side channel attack, and it possibly could be used to steal passwords and other critical data from a target’s computer. The accuracy rate drops slightly if the sound is recorded remotely via a Zoom conference via a bad actor participating on the conference call. The combination of better microphones, frequent smartphone usage and machine learning advances have made this possible.
Waveforms and sound spectrograms were used to visualize and then train the differences among typing keys, as shown in the diagram below from the research paper, which was published Aug. 3 on arXiv, an open archive for scholarly articles:
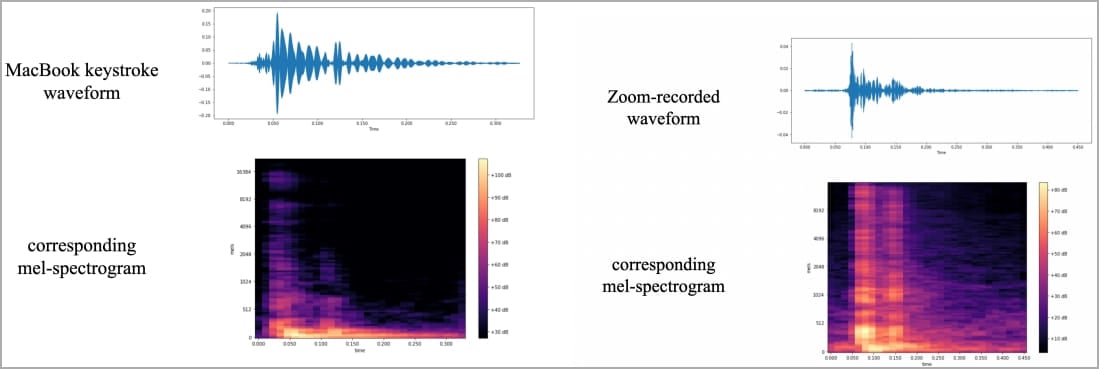
This isn’t the first time that various clever methods have been used to spy and extract information. Perhaps the world’s leading research outfit in these side channel attacks can be found at Ben-Gurion University in Beersheva, Israel, which has figured out more than a dozen different ways to extract information, even if the PC isn’t connected to anything obvious, using so-called “air-gaps.”
This term is used to point out an isolated computer that isn’t obviously connected to the internet — say, via a Wifi network — or other physical means. It’s typical of highly sensitive situations, such as those involving security agencies or in cases where parties are concerned about eavesdropping on their work.
The BGU team has discovered attacks based on tracking flickering LED lights on the computer, frequency variations in WiFi signals, the sounds of a graphics processing unit internal fan, fluctuations in electrical power and using USB connections. All of these were used to collect data that was previously considered private and unavailable to snooping.
Criminals have always used various parts of the electromagnetic spectrum – in the case of the British team, sound – to snoop around. Think of highly sensitive boom microphones that can listen in on conversations in another building across the street, to use a plot line in many spy thrillers. Although some of the tricks of the Israeli researchers are probably beyond normal effort or what one would expect possible, with the right tools and stealth, it can be done.
This story reminds me about a sophisticated attack from the Cold War era where Soviet Union spies placed special electronics inside IBM Selectric typewriters to monitor them. Times have certainly changed!
The British researchers make a few suggestions to thwart the attackers from stealing a user’s keystrokes. One is to vary one’s typing style. Another is that it helps being a touch typist. Also, users should use random combinations of letters and symbols for their passwords, because they are harder to guess using current machine learning techniques. Finally, playing background sounds could help disguise the sounds made by the keys, but it could also be a distraction.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.