 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Greatness isn’t always a good thing. This past year has seen a lot of it — that is, in the form of an innovative phishing-as-a-service malware construction kit of the same name now in active usage.
The Greatness malware attempts to put everything an attacker needs into one tidy package, so that anyone can fill out a few web forms to create a targeted exploit. This is just one of numerous phishing ploys that has led to an increase in these attacks over the past year. It’s a more advanced version of other phishing kits on the market, such as the phishing kit EvilProxy, which has been actively used this year.
Tiago Pereira, a researcher for Cisco Systems Inc.’s Talos Labs, wrote about Greatness back in May. Talos found evidence of its use going back a year, with spikes in its use in December 2022 and March 2023. The malware is designed to phish Microsoft 365 applications and creates “highly convincing decoy and login pages,” such as realistic-looking logos and backgrounds that are automatically extracted from the victim’s own 365 portal.
The research uncovered the logic flow of its three main components: a phishing kit, the service API and a reply bot. A more granular step-by-step analysis can be found in a recent blog post from Adrian Del Prado, an analyst with Swedish security firm Outpost24.
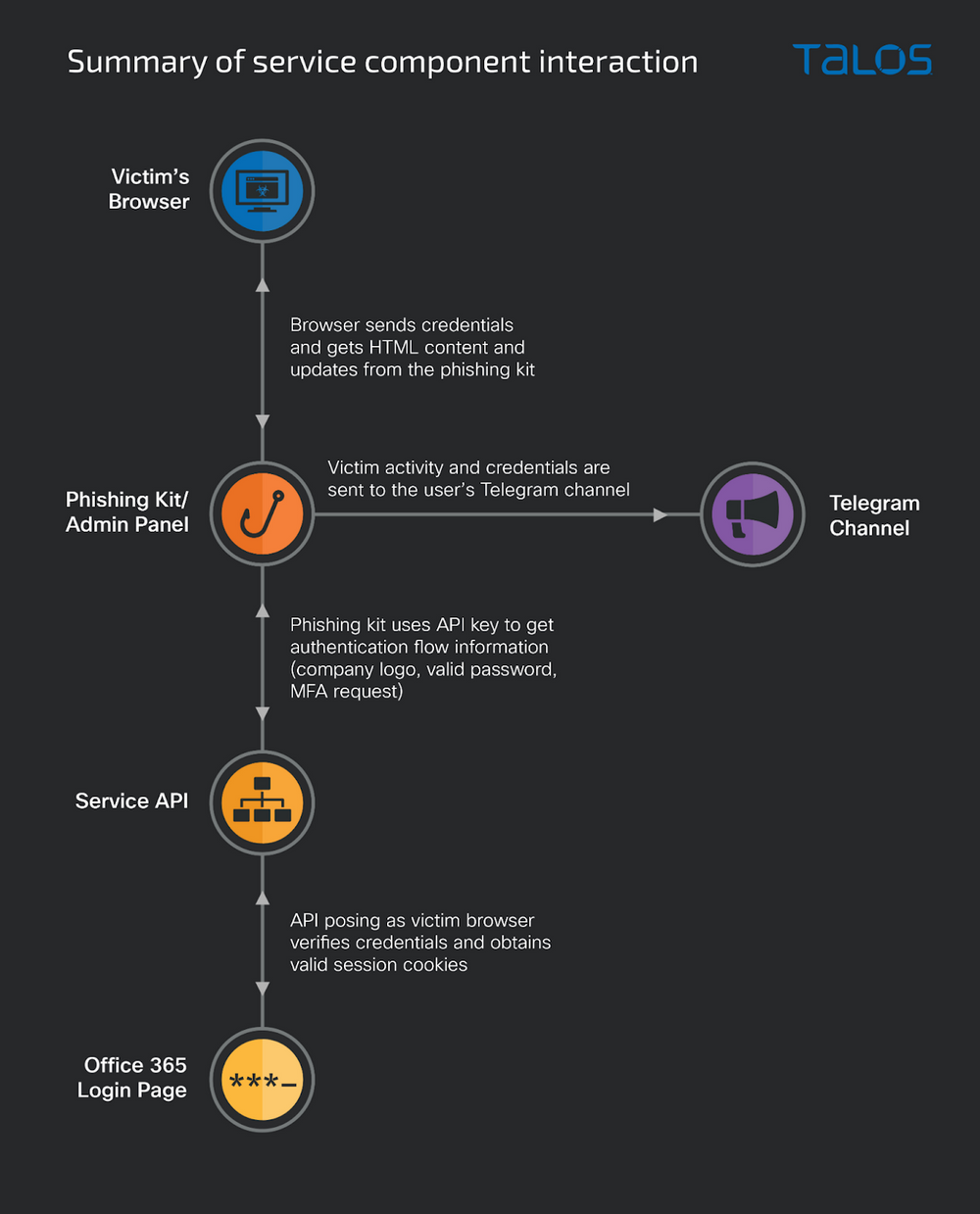
Image: Talos Labs
The first stage of the attack is sending the victim a malicious email that has an attached web page with the lure of a reply to an existing thread. This takes the victim to the phony 365 login page, which is where the malware impersonates the victim’s login to steal the multifactor authentication code and browser session cookie to gain access to the account. Microsoft’s Threat Intelligence tweeted this diagram that shows how this impersonation, called synchronous relay servers, works:

Image: Microsoft
To get started with the tool, an attacker needs a valid API key, just like any other legitimate software-as-a-service product. It’s used to gain access to the phishing kit’s administration page, which is where the attacker customizes the message and keeps track of the stolen credentials and progress of the attack.
Greatness and EvilProxy aren’t the only phishing-as-a-service tools that are in use. A few weeks ago, Interpol took down the group behind 16shop platform, which sold many of these kits.
Security firm Group-IB assisted law enforcement with the technical details to locate the U.S.-based hosting provider for the kits, which were used to launch more than 150,000 phishing-related domains and targeted more than 70,000 users around the world. These kits were tracked back to 2017 and had sold for modest fees of $150 or less. Interpol worked with national police in Indonesia, where their servers were located, and Japan to arrest the criminals behind 16shop.
Earlier this year, Zahi Ohana from CyberArk Software Ltd. wrote about another phishing malware group targeting Israeli credit cards. The blog also documents how the researchers could easily create their own phishing construction kit in a matter of minutes. They found kit sellers in various places online, including on Telegram channels and at Shopify merchants. “No tech knowledge is needed to operate them,” he noted.
And phishing kits have been around a very long time. Fortinet Inc.’s researchers wrote about a Russian website called Fake Game which was selling them as early as 2015.
Given the ease of creation, these kits will continue to plague business users for some time. They require a massive coordinated law enforcement effort because, as the case of 16shop shows, the hosting provider, servers and personnel can be scattered across the planet.
Their use could be a way to motivate defenders to do a better job at tracking user location patterns and flagging odd or unusual circumstances.
What is new is the way that kits such as Greatness have been crafted specifically to defeat multifactor authentication techniques. Some MFA approaches, such as hardware keys and using Fast Identity Online protocols, are more protected from this kind of compromise. That’s great, but many businesses still rely on older and less secure methods, such as sending the additional factor via SMS texts.
“As time passes, increasingly powerful tools designed to bypass the protections offered by MFA appear in the wild, and business models such as phishing-as-a-service puts them in the hands of anyone willing to pay the price, regardless of their knowledge and skills,” Del Prado noted. “However, this development has introduced new restrictions on the developers, such as the need to be able to control licenses, opening new doors for threat intelligence analysts when researching threat actor activity and detection.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.