 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The malware group behind the LockBit ransomware attacks has gotten even more sophisticated.
Australian cybersecurity officials, the FBI and the Cybersecurity and Infrastructure Security Agency on Tuesday jointly released a security advisory on how the group is exploiting the CitrixBleed vulnerability.
The group isn’t the only one using this issue, which compromises various Citrix load balancing and networking equipment. And though various warnings were issued about a month ago when the exploit first came to light, many enterprises have been slow to patch their gear. The below chart from The ShadowServer Foundation shows more than 3,000 affected devices, mostly in North America and Europe.
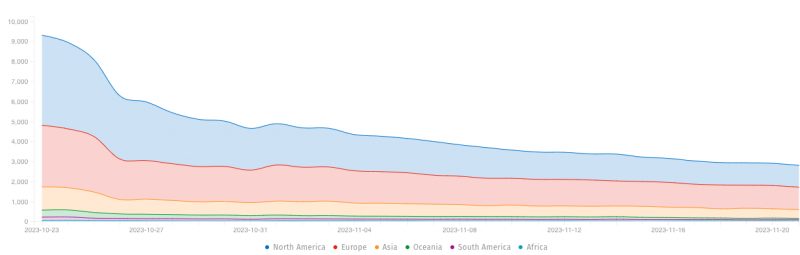
CISA ordered all federal civilian agencies on Oct. 18 to patch the bug and gave a deadline of Nov. 8 to complete the task. Obviously, as the graph shows, that hasn’t completely happened.
The agency mentioned one victim, Boeing’s parts and distribution business, which was attacked earlier this month with this exploit. The company confirmed it was hit with the latest LockBit ransomware, which leveraged Citrix Bleed to “hijack legitimate user sessions on Citrix NetScaler web application delivery controllers and Gateway appliances,” according to the agencies’ news release. Once inside a target’s network, the hackers employ various remote and networking monitoring tools to gain further access and locate the ultimate server that will be encrypted with the ransomware.
“If compromise is suspected or detected, organizations should assume that threat actors hold full administrative access and can perform all tasks associated with the web management software as well as installing malicious code,” the agencies warned.
The LockBit group has been busy on other fronts as well, setting up new negotiation rules for its criminal affiliates last month. Perhaps the group wanted bigger payouts across its ransomware-as-a-service or RaaS network, and so it’s trying to stop discounted ransoms. Another reason could be to try to bring a more uniform workflow with what a group representative claimed is hundreds of active affiliates infecting victims.
“Because LockBit operates under a RaaS model, there isn’t a standard intrusion playbook used by affiliates,” Ben Forster, a senior product director of AttackIQ Inc., told SiliconANGLE. “Threat actors leverage a wide variety of tactics, techniques, and procedures in the initial stage of the attack.”
According to researchers at Analyst1, affiliates will now be forced to use a tiered percentage-based system for ransom fees, depending on the victim’s annual revenue, that can range up to 10% of total annual revenues for smaller organizations. Discounts greater that 50% are prohibited under the new rules.
The researchers posted the screenshot below showing the victim portal that offers a chat-based dialog along with a trial decrypt button to test the presence of LockBit.
That post also describes other details about the group, including the evolution of negotiation tools and techniques and its latest efforts at rebranding. Yes, even ransomware groups have to keep their brands front and center.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.