 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Cloud security continues to vex corporate information technology managers, and new research indicates that the problems are both widespread and not easily fixable, thanks to a number of weak areas.
In many cases, the procedures to secure cloud workloads has been well-known for years but aren’t always applied consistently or reliably. Some old chestnuts, such as cross-site scripting and SQL injection attacks on web servers, still account for almost half of today’s cloud vulnerabilities, for example.
The problems cover the waterfront and aren’t just structural issues. Secondary issues such as security alerts take too much time to resolve, and risky behaviors fester without any real accountability to prevent or change.
SiliconANGLE examined four cloud security reports that address these issues:
The reports show that despite reams of details on best security practices, organizations don’t do well with their implementation, follow-through or consistent application. For example, consider well-known practices such as the usage of complex and unique passwords, collection of access logs and avoidance of hard-coded credentials.
Unit 42 states what should be obvious by now, that “hard-coded credentials pose significant security risks because adversaries can use them to bypass most of the defense mechanisms.” Yet it found that more than 80% of organizations still used them.
A similar majority of accounts analyzed in its report doesn’t turn on the logging and auditing features across Amazon Web Services’ CloudTrail, the Microsoft Azure key vault audit logging and Google Cloud Platform Storage Bucket logging services.
The situation is slightly better when it comes to enforcing another best-practice safeguard: multifactor authentication. Even for cloud-oriented businesses, MFA has been slowly adopted within organizations. Datadog’s research found that 45% of AWS organizations had one or more users authenticate their main command consoles without using MFA.
Worse, only 20% of Azure organizations had all of their Azure Active Directory users authenticate with MFA. Unit 42’s research concurs, with these findings: “At least three-quarters of organizations don’t enforce MFA for console users, and more than half of organizations don’t enforce MFA for root/admin users.” All of these numbers are pretty dismal, given the widespread dictums for MFA that have appeared – along with the numerous breach statistics of accounts that relied on less secure methods.
Speaking of security credentials, Datadog’s report found that static, long-lived credentials still cast a long shadow, and eliminating them has proven difficult. It found that across the three major cloud providers, roughly half of access keys are more than a year old, and more than one in 10 are more than three years old. “This demonstrates that access keys tend to live for longer than they should, and many access keys aren’t being used and still haven’t been deprovisioned,” the authors wrote.
IBM’s X-Force team agreed with these statistics: It discovered plain-text credentials located on user endpoints in 33% of engagements involving cloud environments.
Datadog’s report identified two other major issues:
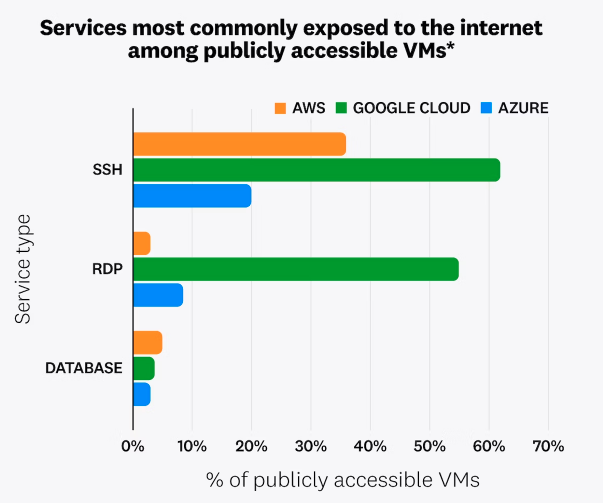 On top of this, 7% of AWS EC2 instances, 3% of Azure instances and 13% of Google Cloud instances were found to be publicly exposed to the internet. The range of different service types across the three platforms are summarized in the above graph. Although these numbers were low, they still represent risks. Unit 42’s report found much higher percentages of publicly exposed services in their telemetry from 2022 and it cited from this data that these services are typically scanned and attacked within minutes of their discovery.
On top of this, 7% of AWS EC2 instances, 3% of Azure instances and 13% of Google Cloud instances were found to be publicly exposed to the internet. The range of different service types across the three platforms are summarized in the above graph. Although these numbers were low, they still represent risks. Unit 42’s report found much higher percentages of publicly exposed services in their telemetry from 2022 and it cited from this data that these services are typically scanned and attacked within minutes of their discovery.When these technical challenges are combined with bad behaviors, cloud security becomes more difficult to enforce. As Illumio’s report said, “The vast majority of organizations that use cloud-based services need more efficiency, visibility and capabilities to reduce risks in their environment and the survey found that nearly half the data breaches suffered over the past year originated in the cloud.”
Part of the problem, according to Unit 42’s research, is the difference between cloud and on-premises security: “Traditional digital forensics and incident response techniques are not designed to handle these types of events because the tooling, processes, and data sources necessary for investigating security incidents are very different between on-premises and cloud environments.”
Illumio’s report contains some dire language: “Today’s cloud security solutions are continuing to fail when it comes to safeguarding companies against cybercriminals who regularly cause massive disruption by exfiltrating data and demanding exorbitant ransoms.”
Two solid recommendations come from the IBM report: “Engage in adversary simulation exercises using cloud-based scenarios to train and practice effective cloud-based incident response. And use AI capabilities to help scrutinize digital identities and behaviors, verify their legitimacy and deliver smarter authentication.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.