 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
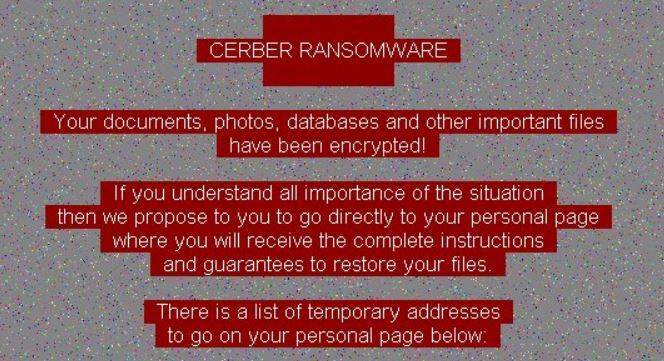
Researchers at cloud forensics and incident response platform startup Cado Security Ltd. today detailed and warned of a new Cerber ransomware campaign being deployed onto services running Atlassian Corp.’s Confluence application.
Cerber ransomware has been around since 2016. The last time SiliconANGLE wrote about it was in 2017, but through the years Cerber has always been around, if sporadically and not always gaining attention.
The new Cerber campaign is targeting CVE-2023-22518, a severe vulnerability in Confluence revealed last year that allows an unauthenticated attacker to reset Confluence and create a Confluence instance administrator account. Using a compromised account, an attacker can perform all administrative actions available to a Confluence instance administration, including total loss of confidentiality, integrity and availability.
The campaign targeting Confluence consists of three highly obfuscated C++ payloads, compiled as a 64-bit Executable and Linkable Format and packed with UPX. UPX is a common packer used by threat actors that allows the program code to be encoded and stored in the binary to prevent software from scanning the payload and detecting the malware, before eventually being unpacked, extracted into memory and executed.
The infection process starts with the exploitation of the Confluence vulnerability that permits an attacker to reset the application and forge a new administrator account. Once administrative access is secured, the attackers deploy an Effluence web shell plugin via the admin panel, facilitating the download and execution of the Cerber ransomware.
The ransomware’s primary purpose is to encrypt files on the compromised system. The current version of Cerber initially downloads a secondary payload — a log checker possibly designed to verify the malware’s permissions or detect sandbox environments that might restrict its operations. Following this, Cerber then downloads and executes the main encryptor payload, which encrypts files and appends a “.L0CK3D” extension, leaving a ransom note in each affected directory.
Despite using sophisticated encryption methods, the researchers note, Cerber’s impact can be subdued in well-configured systems where regular backups mitigate the damage. Interestingly, the analysis reveals no evidence of data exfiltration, meaning that Cerber is still old-fashioned ransomware: It simply encrypts data but doesn’t steal it like many newer and more prevalent forms of ransomware do today.
“While the use of the Confluence vulnerability allows it to compromise a large amount of likely high-value systems, often the data it is able to encrypt will be limited to just the Confluence data and in well-configured systems, this will be backed up,” the researchers conclude. “This greatly limits the efficacy of the ransomware in extracting money from victims, as there is much less incentive to pay up.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.