 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
French multinational digital automation and energy firm Schneider Electric SE has been breached and had data stolen, but the ransom payment those behind the theft are demanding is not money. It’s baguettes. Lots of baguettes.
Exactly when the breach took place is unclear, but claims that the company had been breached first appeared on X over the weekend, according to Bleeping Computer. Schneider Electric confirmed the breach on Monday, saying that it was investigating a “cybersecurity incident involving unauthorized access to one of our internal project execution tracking platforms, which is hosted within an isolated environment.”
A ransomware gang called Hellcat has claimed responsibility, claiming that it gained access to Schneider Electric’s infrastructure through the company’s Atlassian Corp. Jira install. “This breach has compromised critical data, including projects, issues, and plugins, along with over 400,000 rows of user data, totaling more than 40GB compressed data,” the hacking group wrote on its dark web leak site.
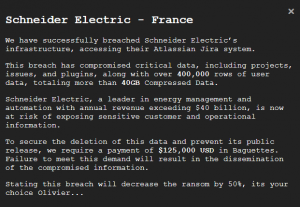 Then it gets interesting. “To secure the deletion of this data and prevent its public release, we require a payment of $125,000 USD in Baguettes,” the group said, adding, “Failure to meet this demand will result in the dissemination of the compromised information.”
Then it gets interesting. “To secure the deletion of this data and prevent its public release, we require a payment of $125,000 USD in Baguettes,” the group said, adding, “Failure to meet this demand will result in the dissemination of the compromised information.”
Notably, though, the amount of baguettes Schneider Electric might be up for has now been reduced, with the group also writing that “stating this breach will decrease the ransom by 50%, it’s your choice, Olivier.” Olivier refers to Chief Executive Officer Olivier Blum and, with Schneider admitting to the breach, presumably the ransom due is now $62,500 in baguettes.
Given it’s unlikely Schneider Electric will cough up the dough, the deadline for the baguette payment is Nov. 7, after which time Hellcat promises to release the stolen data.
The Hellcat ransomware group first gained attention in October when they targeted high-profile entities like Israel’s Knesset and Jordan’s Ministry of Education, exfiltrating sensitive data and demanding substantial ransoms. The group, until now, has established a reputation for targeting government institutions and educational organizations, leveraging their access to critical data to coerce victims into paying.
Hellcat operates by infiltrating systems, extracting vast amounts of sensitive information and threatening to release it unless their ransom demands are met. Like many similar groups, they often publicize their breaches on the dark web to pressure victims and enhance their visibility.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.