 CLOUD
CLOUD
 CLOUD
CLOUD
 CLOUD
CLOUD
Microsoft Corp. today announced a preview of its new Azure Bastion service, which allows companies to connect to Azure virtual machines via a private internet connection.
The company said the managed service is an additional safeguard for security-conscious organizations that don’t want to connect to their Azure VMs via public internet connections, which can sometimes pose more “security and connectivity” problems. Virtual machines are computers emulated in software to provide more flexibility and efficiency in data centers.
With Azure Bastion, companies can start a Remote Desktop Service or Secure Shell remote connection session from the Azure Portal using a HTML5-based internet browser. They then connect to Azure Bastion via a Secure Sockets Layer connection, which enables them to access their Azure VMs using a private internet protocol address.
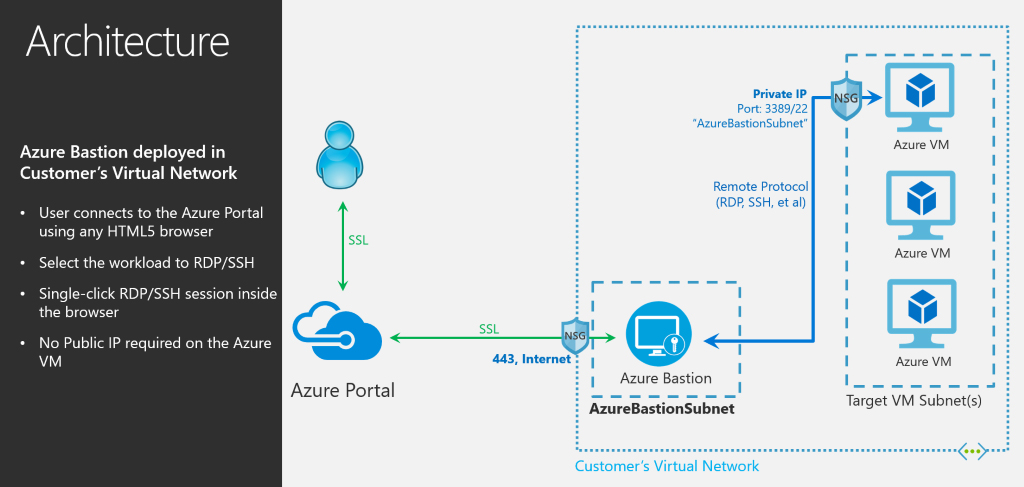
Microsoft said Azure Bastion is “agentless,” which means there are no service, daemon or process monitoring tools running in the background. Microsoft will also take care of all the patching and maintenance work.
Azure Bastion Service for secure access to your off-Internet VMs is now in public preview: https://t.co/vXJbDjfGVC
— Mark Russinovich (@markrussinovich) June 18, 2019
In the future, Microsoft is planning to integrate its identity access management service Azure Active Directory with Bastion. This will enable additional security features such as single sign-on access and multifactor authentication. Microsoft said it’s also considering expanding auditing and client support for Bastion.
“We are also looking to add support for native RDP/SSH clients so that you can use your favorite client applications to securely connect to your Azure Virtual Machines using Azure Bastion, while at the same time enhance the auditing experience for RDP sessions with full session video recording,” Yousef Khalidi, vice president of Azure Networking, said in a blog post announcing the service.
Analyst Holger Mueller of Constellation Research Inc. told SiliconANGLE that Azure Bastion should be useful to organizations that are worried about exposing machines and the critical data they host on the public internet. He said companies typically use “gateway machines,” which are devices that act as a connection between two networks, to get around this risk. But the problem is that their manual overheads is a big hassle and a source of errors, so they often pose a risk themselves.
“Microsoft is basically taking over this responsibility with Azure Bastion, and it’s a good approach as integration is easy,” Mueller said. “And because it’s a managed service, the platform and connectivity challenges are all handled by Microsoft. We expect a positive uptake by enterprises to run their next-generation applications.”
The Azure Bastion preview is currently available in the Azure West US, East US, West Europe, South Central US, Australia East and Japan East regions.
Azure Bastion will be charged on a per-hour basis for the amount of outbound data transferred.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.