 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Two new reports on phishing trends show a rise in attacks, and they’re taking more complex paths through the internet to connect victims with malware-laced websites.
The trends are highlighted in Cloudflare Inc.’s annual phishing trends report released today, as well as the latest compendium of phishing trends by the Interisle Consulting Group.
What distinguishes both of these reports from the numerous others SiliconANGLE has reported on recently, such as Inky’s and Cofense’s, is the sheer message volume and regular reports to compare their results. Cloudflare evaluated a sample of more than 279 million email threat indicators, 250 million malicious messages and more than a billion instances of brand impersonation from emails processed between May 2022 and May 2023. Cloudflare acquired Area 1 Security last year and has continued its reports.
Interisle analyzed 6 million phishing reports processed between May 2022 and May 2023, consolidating separate databases compiled by the Anti-Phishing Working Group, OpenPhish, PhishTank and Spamhaus. It found 1.8 million unique attacks in this combined database.
Cloudflare found the method used in about a third of the threats was deceptive links. That was on track from the previous year’s analysis.
Some of these links led potential victims on a series of redirections, such as one email that used the Silicon Valley Bank’s logo to prey on users. It went through a series of four different websites until landing on a phony DocuSign site. It illustrates the effort that attackers will go to hide their criminality. Another sophisticated attack was targeted at Cloudflare employees, which wasn’t successful thanks to its using FIDO-2 hardware keys.
Cloudflare found that phishing is a growth business. Sadly, 71% of organizations experienced an attempted or actual business email compromise attack in 2022.
“Phishing attacks of all types have grown in sophistication, so much so that traditional approaches against them are not sufficient to prevent the most dangerous attacks,” the report said. This happened across a number of different metrics — one of them timing, what Cloudflare calls a deferred attack whereby a phishing link initially goes to a benign website that days later is weaponized (below).
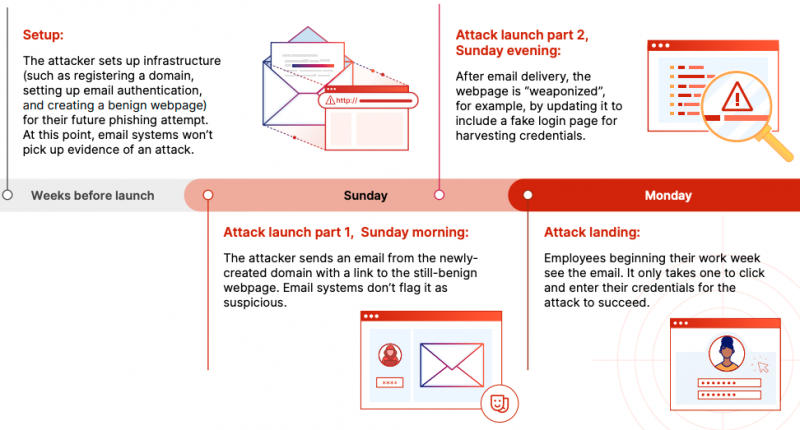
Another issue is that almost every unwanted message was crafted to pass the various email authentication protocols. “A phisher’s No. 1 goal is to achieve authenticity and appear legitimate in the eyes of their victims,” Oren Falkowitz, field chief security officer of Cloudflare, told SiliconANGLE. “With email authentication failing to stop threats, relying solely on these tools is a downfall. It is futile to solely rely on standards that track sender information in order to detect and stop campaigns.”
A continuing problem is that phishers are successful at impersonating the world’s largest organizations, the top target being Microsoft Corp. The company’s name was seen in nearly 10% of the phishing messages. One result was interesting: It found more messages impersonating the United Nations, thanks to COVID and the World Health Organization, than the New York Stock Exchange.
The report concludes by making a series of security recommendations, starting with the need to secure email with a zero-trust security approach. “Despite email’s pervasiveness, many organizations still follow a ‘castle-and-moat’ security model that trusts messages from certain individuals and systems by default,” the report notes.
Organizations are recommended to augment cloud email with multiple anti-phishing controls as a multilayered defense can preemptively address high-risk areas for email exposure. Organizations are also advised to adopt phishing-resistant multifactor authentication and to make it hard for humans to make mistakes, such as with email link isolation.
Finally, the report recommends that organizations establish what Cloudflare calls a “paranoid, blame-free culture.” Such a culture should encourage an open, transparent “see something, say something approach” to collaborating with information technology and security incident response teams to get everyone on “team cyber.”
Interisle also found an increase in brand impersonation, also pointing out Microsoft was one of the top targets but eclipsed by Mitsubishi and Facebook (below).

“Far from improving, the phishing landscape is worsening each year,” Interisle wrote. “Reviewing the data we have collected since 2020, we conclude that the prevailing uncoordinated and ineffective attempts to curb phishing are simply not working, and that a new strategy is required.” It saw the number of attacks tripling since May 2020, and more than a million unique domain names were used to produce these attacks in the past year.
 One bright spot is that the hosting provider Freenom stopped offering free domain registrations in January 2023 (above). Prior to that event, the provider was one of the leading sources of domains used in phishing attacks.
One bright spot is that the hosting provider Freenom stopped offering free domain registrations in January 2023 (above). Prior to that event, the provider was one of the leading sources of domains used in phishing attacks.
Its report also found that more than 165 of all attacks used subdomain resources at internet providers, a growing attack vector. These domains are owned by the provider and rented out to their customers often with little to no identity verification, and typically for free. Because they are subdomains, they can leverage the provider’s reputation and are harder to spot and to mitigate.
With reporting from Duncan Riley
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.