 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
New research from Akamai Technologies Inc. shows the increasing level of sophistication that attackers will use on a series of phishing attacks targeting hospitality websites.
The attacks began as early as June 2023 and focused on exploits of the Domain Name System protocols. The attacks involve new efforts to hide their origins and also add new complexity to make them harder to repel. These protocols, as SiliconANGLE wrote about earlier this summer, are the essential glue that support a wide collection of online services, and are a common hacker target.
The hospitality industry as a target means that many attacks are two-pronged in nature: First they aim their phishing lures at hotel staff, such as making a series of online booking requests. The attackers then send followup emails that contain malware-infested links or photos that contain programs to steal data from the hotel site operators.
In this particular case, the attackers had a second stage of victims: The accounts of individual customers who are using the online services were further compromised with additional malware-laced emails. Akamai originally wrote a detailed analysis of the various steps taken by these attackers last month.
One of the lures is to replicate hotel booking pages as part of its phishing campaign, where it would steal credit card data from potential guests. The attackers even used an online chat window to make their phony pages seem more realistic.
The researchers were able to examine the DNS telemetry given its global presence and the willingness of its customers to share anonymized network log data, as SiliconANGLE reported on Akamai’s analysis of DNS patterns back in 2022. Akamai stores domain name statistics with time stamps and other metadata that were useful in finding patterns of IP addresses using certain domain names.
They segregated and grouped these domains into clusters (below) with shared properties such as registration and when they were first seen, a partial table of which is shown here. Many of these domains demonstrate typosquatting techniques, such as combosquatting, which adds the subdomain “reservation” and other common words to the overall domain to make them more believable, or to pass quick inspection by users not paying careful attention.
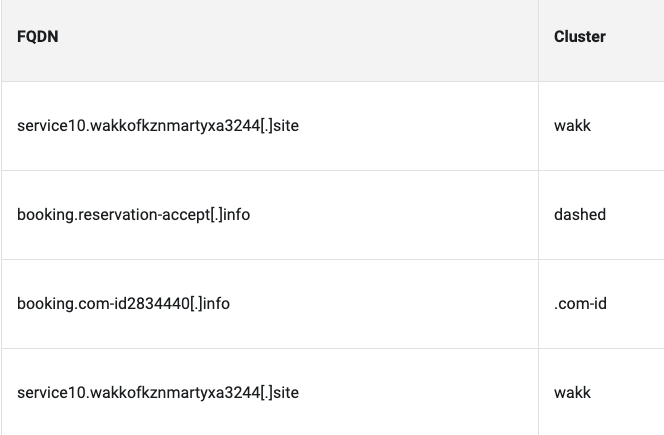 Akamai also mentions the variation called levelsquatting, which impersonates a domain with a very long string of characters. This is typically truncated by browsers, especially mobile browsers, so that the displayed part of the domain name looks more legitimate.
Akamai also mentions the variation called levelsquatting, which impersonates a domain with a very long string of characters. This is typically truncated by browsers, especially mobile browsers, so that the displayed part of the domain name looks more legitimate.
One of the main analysis pointers is the quick use of the domains shortly after they are initially registered, sometimes just a day or so. Another factor is the relationship among the different clusters. For example, one domain saw the largest number of DNS queries, more than twice what the analysts saw with other clusters. “This contrast can indicate that it is being used for redirection or as a hub of some sort,” they wrote on their blog. Most of the clusters are still in active use, which is troubling.
The exploit was linked to a Russian threat actor, given the use of a number of Russain-specific brands such as Sberbank and Yandex. This could be a smokescreen, however: Either it’s a diversionary tactic to gain credibility by using these brand names, or it could be a further targeting technique for Russian speakers. This points out how hard attribution can be when dissecting these attacks.
Akamai tracked the majority of DNS traffic to Swiss, Hong Kong and Canadian origins. Despite this commonality, one stumbling block is that the attacks didn’t focus on any particular geographic target.
Another way to track DNS queries is to examine which internet registrars were used to record the owners of these domain, which in this case was quite clear: NameSilo was the registrar of choice for the majority of the DNS names collected by the analysts. “It seems that the malicious actors registered these domain names through NameSilo and then used the PrivacyGuardian feature to keep their identity hidden,” the analysts posted.
The research shows how complex the world of phishing has become, and how using various DNS protective services, including open DNS resolvers and various DNS security protocols such as DNS over HTTPS or DNSCrypt, can help reduce and potentially avoid these attacks.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.