 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
One of the challenges for phishing attacks is that innovation is rife, especially when it comes to convincing targets that they are responding to a legitimate email.
New reports from Microsoft and eSentire highlight some of them in the area called attackers-in-the-middle, or AITM. It’s a variation on the general man-in-the-middle types of attacks and packs a potent punch when combined with automated phishing-as-a-service kits.
This type of attack uses a reverse proxy that is setup between the target and a legitimate login page. This interferes with the login connection by tricking users into revealing their login credentials, including any MFA codes and browser session cookies, to an attacker.
“One of the most alarming features of AITM attacks is their ability to effectively bypass multi-factor authentication by capturing session cookies,” eSentire wrote in its blog post. “Attackers can seize session cookies during these attacks, allowing them to maintain unauthorized access without re-authentication.”
A diagram from HYPR illustrates the flow:
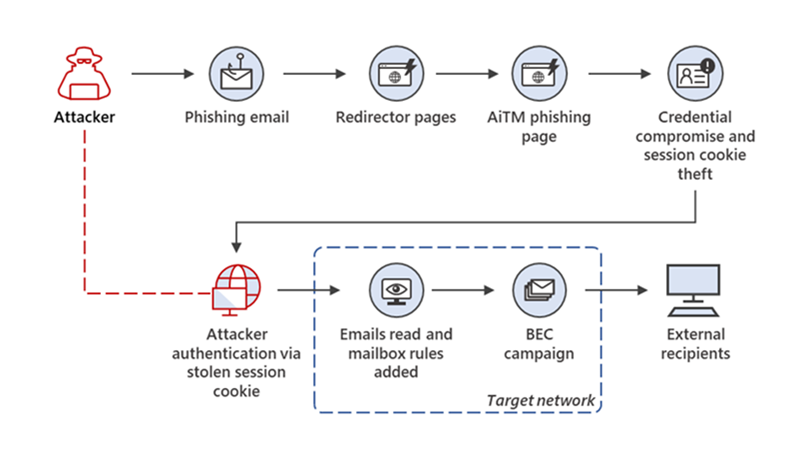
The attack is typically paired with phishing kits such as EvilProxy and SW3LL. What is new about the AITM discovered by eSentire is pairing the attack with sending a malicious QR code. This attack is taking it to the next level of complexity.
It adds to the perceived authenticity of the phishing lure, and because the code is usually scanned by a mobile device, it can take a victim out of any corporate network monitoring or protection. The case examined by eSentire also included a second step, making use of Cloudflare’s Turnstile Captcha replacement as a way to hide the actual redirected URLs. That brings more perceived credibility and also makes it harder to track the underlying attack code by security analysts.
The complete attack is managed with a phishing service called DadSec, which can customize the overall themes and content of the emails, and direct the actual attack progress, all managed with a web control panel that costs $500 per operator. The eSentire analysts found more than a thousand different domains that were using this particular phishing service.
Microsoft also tracked another AITM attack back in June that was behind several business email compromises and was attributed to the Storm-1167 malware group. Just like the previous AITM attack, it makes use of multiple and complex operations to hide the nature of the attack and lure in victims. In this particular case, the address book of each victim was used to create a separate campaign of thousands of phishing emails sent to each addressee, including some high-volume AITM phishing campaigns, some of which involve sending millions of emails in a single day.
Unlike the first attack, this AITM didn’t employ reverse proxies but used an indirect proxy and webpages that mimic the login pages of the target app. This gives the attacker more control to customize content of these mimicked pages, and also is harder to track with traditional network monitoring tools.
Mitigating these attacks will require multiple defensive tactics. “In AITM attacks, since the sign-in session is compromised, password reset is not an effective solution,” wrote Microsoft. Instead, logins should be protected with Fast Identity Alliance technologies such as Yubico hardware keys and passkeys. Continuous network monitoring and role-based authentication access are other tools that can stop these attacks.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.