John Casaretto
Latest from John Casaretto
Good Technology makes it easy to say goodbye to BlackBerry with a free offer
Good Technology announced today that it could be picking up your tab. No, not the tab some people may be hoping for – this is about those companies that have BlackBerry users that want to move over to Good Technology. The program is called “Migrate Now” and it offers customers the opportunity to avoid additional ...
HP NGIPS delivers infrastructure security to Switzerland National Railway
HP announced yesterday that Swiss Federal Railways has selected HP TippingPoint technology to secure the national railway’s network. The Swiss Federal Railway network is a critical component of Switzerland’s national infrastructure. For an organization like this, protecting the network can be a matter of physical safety because it controls both the signaling system and energy ...
Zscaler predicts big security challenges ahead for 2014
As we are set on the path that 2014 has ahead for us, many of the cybersecurity predictions that have been put out are already manifesting in actual events. Zscaler is a cloud security company that focuses on a number of elements in building a complete cloud security portfolio. With abilities to put controls like ...
Shape Security emerges from stealth, looking to change website security forever
Shape Security emerged from its state of secrecy this morning in a security stealth launch that has famously raised and impressive $26 million dollars through two rounds of funding, without publicly telling anyone what they actually do. It’s been a bit of a mystery and that changes today. The company is introducing an entirely new kind ...
Ten security predictions for 2014 from NeoHapsis
NeoHapsis is next in our cybersecurity prediction series. NeoHapsis is a security and risk management consulting company that specializes in mobile and cloud security services. Among the most interesting predictions, the experts at NeoHapsis predict that next year, there will be a cyberwar resurgence, the cloud will begin to show its hidden costs, and privacy ...
Center for Internet Security – 2014 Cybersecurity predictions
We’re wrapping up our January cybersecurity prediction series for 2014 over the next few days, and we’ve saved some of the best stuff for last. Center for Internet Security’s CEO, Will Pelgrin gave some outstanding prediction points for our series. The Center for Internet Security (CIS) is an expert group in the field of cybersecurity ...
Obama’s NSA surveillance reforms fall short
After the better part of a year of criticism in the face of non-stop information releases about the NSA and its extensive surveillance operations, President Obama emerged to announce some major changes to the NSA’s phone record surveillance program today. The controversial phone records program is but one of many surveillance programs that operate under ...
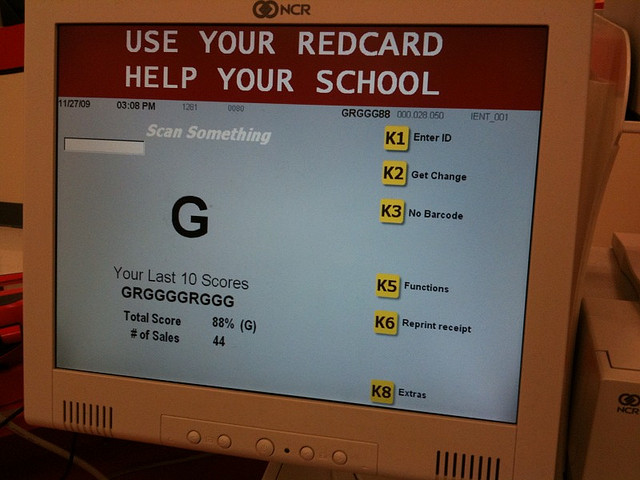
Exclusive report: Inside Job? Target/retail hack investigation turns to POS systems
Sources close to the Target retail hack investigation have information that seemingly contradicts the public stance on what Target knew and when they knew it, in addition to a host of other details. The Target compromise alone has affected up to 110 million consumers and over the weekend, the numbers of affected consumers in the ...
Three more major U.S. retailers hacked, link to Target holiday hackers?
Hardly a day went by since we heard that the big Target hack of December 2013 actually affected as many as 110 million people and that upscale retailer Neiman Marcus was also hacked that the cybercrime news has gotten even more interesting. According to a report from Reuters, three additional major retailers have also been ...
Big and rich: Target retail breach now up to 110 million, Neiman Marcus also hacked
The scope of Target’s retail breach has crept up. Actually it has nearly tripled in the number of people affected. Initial reports stated that data for 40 million consumers was compromised – nothing to sneeze at. The next big development revealed that PIN information was also lost, though Target assures that the information was encrypted. ...