Michelle Davidson
Latest from Michelle Davidson
IBM and Indosat Ooredoo partner to bring cloud services to Indonesia
IBM and Indosat Ooredo have teamed up to bring cloud-based services to Indonesian businesses. The companies will jointly develop and deliver solutions on the IBM Cloud to help businesses streamline processes and improve productivity. This collaboration will enable Indosat Ooredo, one of Indonesia’s largest telecommunications and services providers, to innovate their mobile services offerings and ...
Microsoft gives away SONiC networking kit as part of the Open Compute Project
Microsoft took a big step into the world of free, open-source software yesterday when it announced it is giving away its Software for Open Networking in the Cloud (SONiC) as part of its work with the Facebook-founded Open Compute Project (OCP). SONiC, a collection of software networking components required to build network devices like switches, ...
Cloud security becomes a boardroom issue
Business decisions are driving the adoption of cloud computing. Often, however, decisions to move to the cloud are made without considering the security risks associated with it, and information security teams are bypassed. As a result, businesses put themselves at risk, according to the Cloud Security Alliance (CSA). Twelve cloud security concerns, in particular, threaten ...
RackWare enhances its cloud computing management software
Building on its cloud computing management offering for enterprises, RackWare Inc. released version 5.0 of its flagship RackWare Management Module (RMM). The new features make it easier for companies to scale across private, public or hybrid cloud environments and more cost-efficiently, said Todd Matters, the chief architect for RackWare. Key to that is the merging ...
Hybrid cloud introduces security challenges
Data security is always a concern for enterprises. When they move to a hybrid cloud environment, however, new challenges emerge. Top on their list: how to apply existing security principles to a new architecture. According to a report published by 451 Research, 59 percent of the senior IT security executives surveyed said maintaining consistent access ...
Slow Office 365 performance? Aryaka has a solution
Cloud-hosted services give employees real-time access to applications wherever they are. Sometimes, however, performance issues strike and cause employee productivity to slow to a crawl. Microsoft’s Office 365 is not immune to the problem. Demands on the network, synchronization with Outlook, software updates, template downloads and more can affect performance. The problem is the Internet ...
Hyperglance adds clarity to the chaos of multi-cloud environments
Ironically, the adoption of cloud computing—public and private—has clouded the visibility into resources running in those environments. Organizations have trouble seeing, monitoring and managing cloud resources. And that lack of visibility means security problems can go undetected and cloud services costs can unknowingly run up. To help shine a light on those issues, Hyperglance Ltd. ...
Cisco buys CliQr, expands hybrid cloud management solutions
Cisco Systems gave its cloud platform a boost with the acquisition of hybrid cloud management provider CliQr Technologies Inc. The company’s 195th acquisition, Cisco will pay $260 million in cash and equity awards for the Santa Clara, CA-based company. The purchase is expected to close in the third quarter of fiscal year 2016. CliQr’s CloudCenter ...
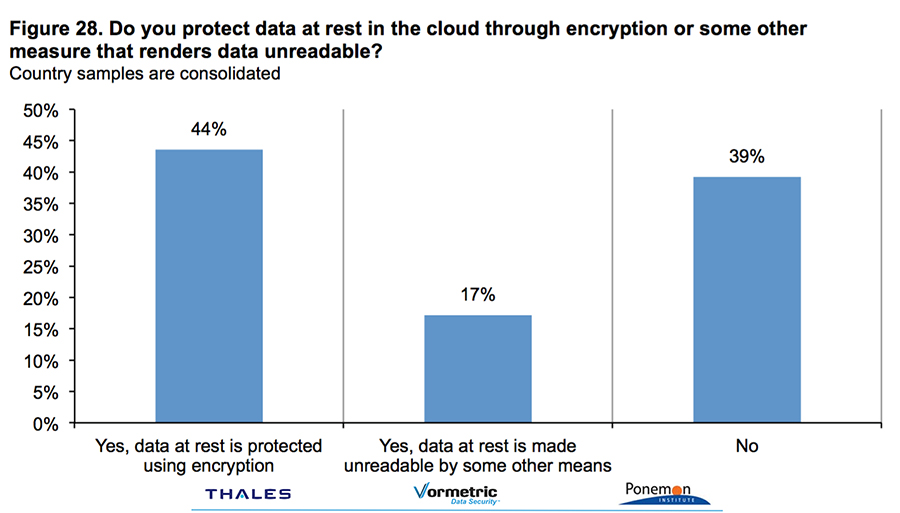
Encryption adoption low for cloud users, but it’s growing
Encryption is the first line of defense when securing data in the cloud, but many companies don’t make use of it. A new study on encryption trends found 56 percent of organizations transfer sensitive or confidential data to the cloud whether or not it is encrypted or made unreadable via some other mechanism. And another ...
Netskope tool protects against threats from cloud-based apps
The increased use of cloud-based apps in the enterprise has created a new frontier for hackers. Unsanctioned, non-enterprise-ready apps provide entries for malware. Unprotected data (while in transit or at rest) can cause data leakage. And the inability to detect unusual behavior means threats fly under the radar. To protect against those things, IT organizations ...