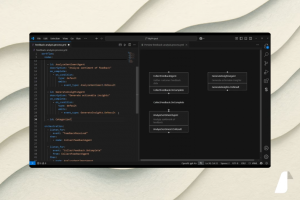
Firesheep will permanently scare you from hotspots
Do you know what the above screenshot is? It’s the picture of your Google accounts, Facebook accounts, Twitter accounts, Flickr accounts being hijacked by anyone running a simple point-n-click Firefox plug-in called “Firesheep“. A complete novice in computer hacking would be able to go into your Facebook page as you and do anything they want as you. I wouldn’t be surprised if a bunch of juveniles started posting nasty comments on other people’s accounts.![]()
Why would anyone write such a destructive plugin in such a high grade weaponized form? Because very little media coverage and very few people listened years ago when this technology first became readily available 3 years ago. So because it didn’t get much media coverage, most people didn’t care and most of the popular websites (besides Gmail and Google search but not other Google properties) have failed to enable start-to-finish SSL which would have prevented this type of attack. Making this type of attack more visible puts pressure on the application providers to fix their websites.
The typical tired excuse from application providers is that SSL from start to finish is too computationally expensive for the server infrastructure which hasn’t been true for a decade with the speed of modern computers. Furthermore, the most compute intensive part of SSL is getting the session started and keeping it going requires minimal effort. To be more precise, it costs thousands of times more compute power to start an SSL session than to maintain it. The most silly use of SSL is WordPress.com which hosts millions of blogs. They turn on SSL every time you go to the administration page but turn it off when you leave it thinking they’re saving server resources. But then starts a new session when you return to the admin page and WordPress servers get hit with even more work than if they had just left SSL running.
Protecting yourself
Unfortunately, it’s not easy for the typical consumer to protect themselves because action must be taken by infrastructure providers and application providers. Consumers can use secure tunneling services like VPN but those generally cost money, add complexity, and reduce performance. The easiest thing consumers can do is to send loud complaints to their application and hotspot providers to fix it on their end. Consumers should certainly enable permanent SSL on their Gmail accounts if they haven’t already done so, but sites like Facebook and Twitter don’t have this option and they won’t have it until enough people complain.
What should application providers do?
Facebook, Twitter, and Google really need to get their act together and make all of their sites SSL by default from start to finish. Enough with the excuses, it’s time they fixed their sites. And before someone asks: where’s your SSL Mr. Digital Society smarty pants? Well we had that covered since inception with https://www.digitalsociety.org, but that’s not really important since our readers aren’t logging in to our site and we don’t know or store your identity here like Facebook or Twitter or Google sites.![]()
What should hotspot providers do?
Some like Tris Hussey suggested that they should just turn on WEP/WPA. Well that’s really not good enough since WEP is absolutely worthless, and “WPA” has two modes one of which wouldn’t protect you in the context of a hotspot. If WPA is used in Pre-Shared Key (PSK) mode for a hotspot, it’s effectively a party line since everyone knows the PSK which allows session keys to be derived which means you’re not protected.
WPA has to be operated in “enterprise” mode which is something that Google tries to do with their free hotspot service in parts of their home town in Mountain View but fails miserably at. For one thing, they don’t even let you use your existing Google account credentials and you’re forced to set up a new account with them just for the hotspot service. Then they assign you an account password which doesn’t even work. If a network geek like me can’t make it work, I can’t imagine how it would be for normal people.
But the reality is that people don’t want to deal with usernames and passwords at all, and I’ve proposed a really simple solution 3 years ago with anonymous secure hotspots. The user could just use a blank username and blank password and then be given a secure WPA Enterprise connection. It still amazes me that whenever I go to RSA security conferences, they still go to the trouble of setting up a help desk to hand out unique usernames and passwords just to accomplish the same thing. Security people have got to figure out that if security is too hard to implement and use, then the security scheme is essentially broken since no one will use it.
You just can’t get any easier than a blank username and blank password with point-n-click secure connectivity. Once a hotspot provider enables secure encryption, this will essentially offer wire equivalent security for hotspot users and it will give a level of protection to all the websites and all the applications people use. Note that I didn’t say that this was full proof, just that it’s equivalent to wired security which is a huge step up. The wireless network infrastructure still has to block malicious behavior such as ARP spoofing.
[Cross-posted at Digital Society]
A message from John Furrier, co-founder of SiliconANGLE:
Your vote of support is important to us and it helps us keep the content FREE.
One click below supports our mission to provide free, deep, and relevant content.
Join our community on YouTube
Join the community that includes more than 15,000 #CubeAlumni experts, including Amazon.com CEO Andy Jassy, Dell Technologies founder and CEO Michael Dell, Intel CEO Pat Gelsinger, and many more luminaries and experts.
THANK YOU