 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Top security pros say the SolarWinds hack and the COVID-19 pandemic have accelerated a change in their cybersecurity spending patterns.
Not only must chief information security officers secure an increasingly distributed workforce, but they now must also be wary of software code coming from reputable vendors, including the very patches designed to protect them against cyberattacks. Organizations are increasingly prioritizing zero-trust approaches, including simplified identity access management, better endpoint protection and cloud security. And while leading solutions in these sectors are gaining momentum, traditional legacy offerings are being managed down from a spending perspective.
In this Breaking Analysis, we’ll summarize CISO sentiments from a recent Enterprise Technology Research VENN session and provide our quarterly update of the cybersecurity market. In an upcoming episode we’ll be inviting Erik Bradley of ETR to provide deeper analysis on these trends. Here we’ll give you a first look and initial reading of what’s happening in the information security sector as we kick off 2021.
It’s been covered in the press but in case you don’t know the details, SolarWinds is a company that provides software to monitor many aspects of on-premises infrastructure, including network performance, log files, configuration data, storage, servers and the like. Like all software companies, SolarWinds sends out regular updates and patches. Hackers were able to infiltrate the update and “trojanize” the software — meaning when customers installed the updates, the malware just went along for the ride.

The reason this is so insidious is that often hackers will target installations that haven’t installed patches or updates and identify vulnerabilities in the infrastructure that exist as a result. In this case, the very code designed to protect organizations actually facilitated a breach. According to experts, this was quite a sophisticated attack with multiple variants that most believe was perpetrated by the Russian hacker group Cozy Bear, an advanced persistent threat or APT as classified by the U.S. government.
It is suspected that somehow they phished their way into a GitHub repo and stole username and password access to allow them to penetrate the supply chain of software that is delivered over the Internet. But public information on this attack is still spotty. What is known is that the attackers had been lurking since March of last year and had nine months to exfiltrate troves of data from the U.S. government and numerous other companies, including Microsoft Corp. and Cisco Systems Inc.
Last year, right after the attack, friend of theCUBE Val Bercovici of Chainkit said to us on Twitter that he thinks the government hack will have permanent implications on how organizations approach cybersecurity. CISOs seem to agree. Here are some verbatim comments from the CISO roundtable moderated by ETR in late January:
The impact of the breach is profound. It really turned on its head a lot of conventions about cybersecurity.… I don’t think the threat has been exaggerated in the media.
We’re now in a situation where we have to monitor the monitors.
This attack didn’t have any signatures of a previous attack… so you got down to the code level.
80-90% of that code is being downloaded from the internet…. It’s bringing DevOps security processes and making us rethink how to reinvent security.
That’s the question every CISO is wrestling with right now. Security pros will tell you they’re rethinking their practices, tools and approaches, but there’s no one answer.
Below is a tag cloud summarizing some of what we hear in theCUBE community and in the VENN roundtable from security practitioners:

You hear CISOs talk a lot about zero trust and many are leaning into identity access management and PAM, privileged access management. We’re hearing mandates around two factor authentication. We’ve written extensively about identity and firms such as Okta Inc., Sailpoint Technologies Inc. and CyberArk Software Inc. And Microsoft is coming up more and more in this conversation, especially as Okta is seen as setting a price umbrella – there’s definitely some frustration there among CISOs. Auth0, which does authentication as a service, is hitting our radar as well.
Endpoint security, of course, gets attention as the work-from-home trend has become much more important. You can see it in the growth of CrowdStrike Holdings Inc. and as you’ll see in a moment we’re seeing some traction with VMware Inc. and Carbon Black in the ETR survey data as well as momentum with Tanium Inc.
CISOs aren’t going to just rip out what they have so Cisco, especially with Umbrella and Duo, come up in the conversation. As does Palo Alto Networks Inc. We’ve said many times that they’re seen as a thought leader and CISOs like Palo Alto as well as Fortinet Inc. Fortinet buyers tend to be more cost conscious and often midmarket customers.
And so it goes with analytics and micro segmentation and cloud security with Zscaler Inc. and even robotics process automation to automate certain tasks; UiPath Inc. has come up in the conversation more and more in a security context.
So you look at this tag cloud above and there’s no one answer – as is the case with cyber – lots of tools, lots of disciplines and a very capable adversary who has learned to, as the saying goes, “live off the land,” using your own infrastructure and tooling against you.
The common narrative is that security is a top priority with CIOs and CISOs and budgets will be up. Boards of directors are aware and willing to spend. So let’s look at that.
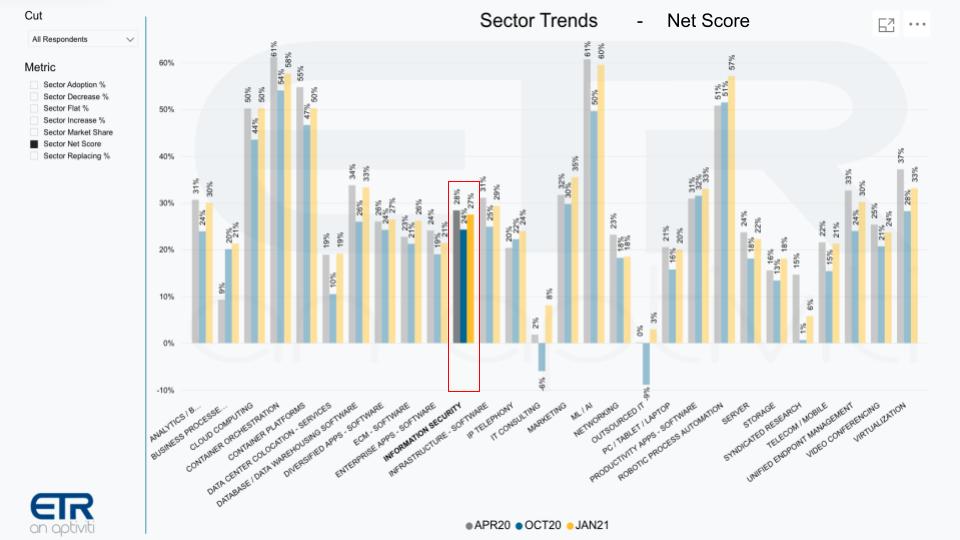
The fact is this is only somewhat true. The chart above shows Net Scores or spending momentum for various sectors across the ETR taxonomy and we’ve highlighted the Information Security segment. Yes, it’s up relative to the October survey, but it doesn’t stand out.
Everything’s up, as we’ve reported, coming off a down year in tech spending – minus 4% – and we’re forecasting a plus 6% to 7% increase this year depending on the pace of the recovery. But the point is cyber is one of many budget items and organizations aren’t simply writing a blank check to the CISO.
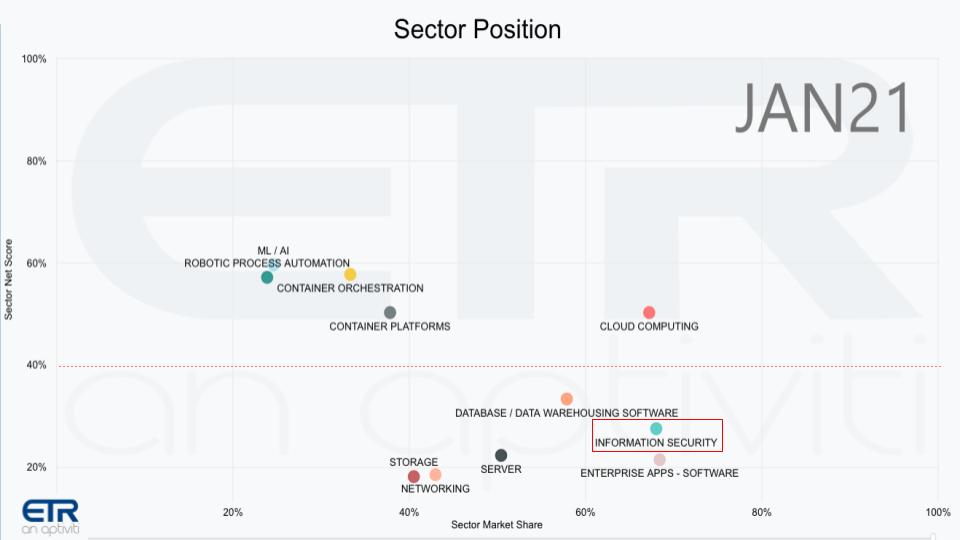
The graphic above shows several sectors in context and we’ve highlighted security in the red box. The vertical axis shows Net Score or spending velocity and the horizontal axis is Market Share or presence in the data set. And you can see that security has a big presence – it’s pervasive, of course.
But it lags some of the top sectors in terms of spending velocity because organizations have lots of priorities. And of course as you’ll see below, like most mature markets, security has some companies with off the charts spending patterns and others that lag.
Below you see that same XY graphic and we’ve plotted a number of selected security players:
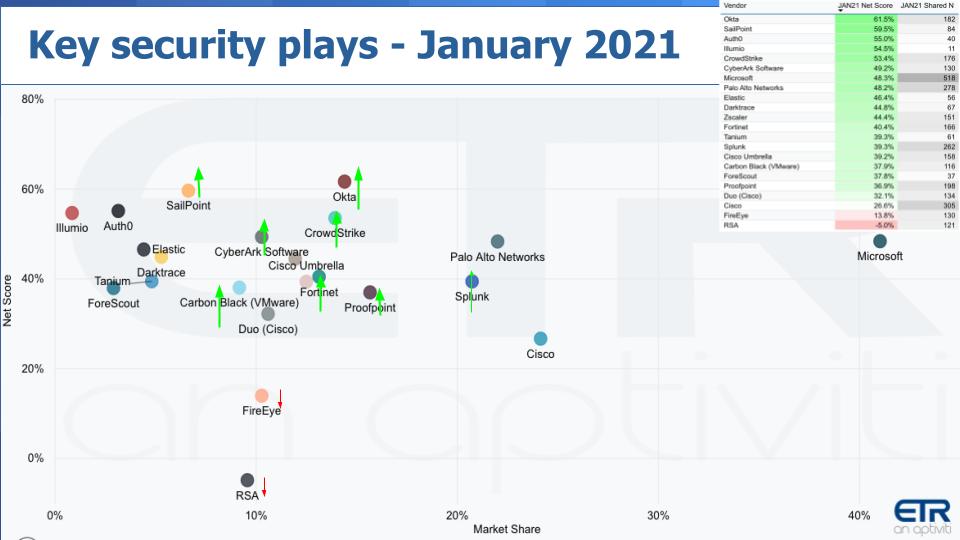
Several points stand out from the above data:
So we see a number of companies with momentum, which stems from a rebound in tech spending generally but also the shift in security spend that we’ve highlighted. And you can see a couple of legacy security firms losing spending momentum – FireEye Inc. and RSA in particular, but there are many others in the ETR data set that are in the red zone.
Let’s dig deeper into the data and the vendor performance.
Below is a view of the data we first showed you in 2019. The tables depict the Net Score (spending velocity) and the Shared N which identifies the number of mentions within the sector and is an indicator of presence in the market. The leftmost chart is sorted by Net Score and the right hand chart is sorted by Shared N. To make the cut and get into this chart, we required a vendor to have had at least an N of 50 mentions in the sector within the survey.
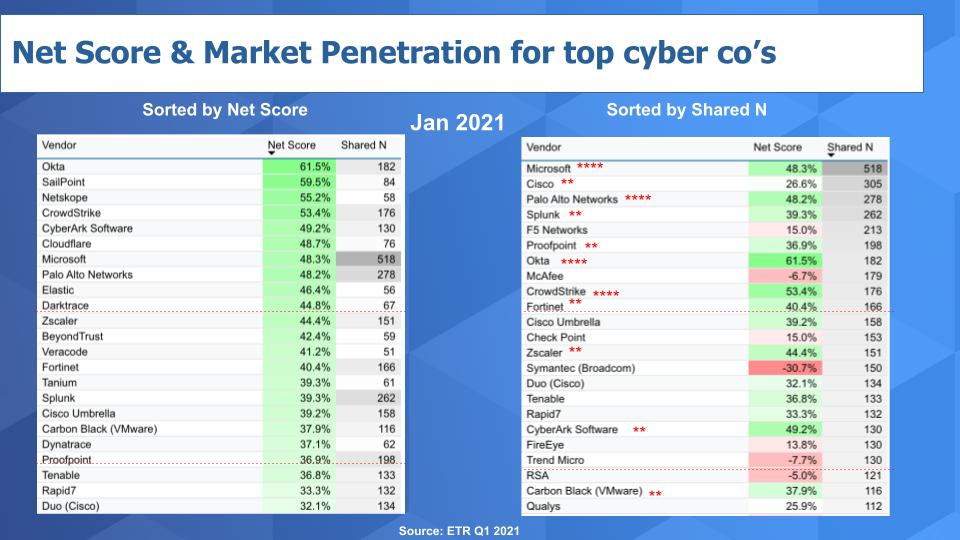
You can see on the leftmost chart that Okta (61.5%) and Sailpoint (59.5%) lead in Net Score and Microsoft has the largest presence in the sector (518 Shared N) along with Cisco (305) and Palo Alto (278).
Something we started two years ago was if a vendor shows up in the top 10 for both Net Score and Shared N, we anoint them with four stars. So Microsoft, Palo Alto, Okta and CrowdStrike are the four cybersecurity vendors that fall into the four-star group.
And we give two stars to those companies that make the top 20 in both categories. So Cisco because of Umbrella and Duo, Splunk, Proofpoint, Fortinet, Zscaler, CyberArk and Carbon Black (now owned by VMware). Carbon Black is new to the two-star list thanks to its rapid rise in Net Score.
At VMworld 2019, Pat Gelsinger told theCUBE that he felt like he got a great deal picking up Carbon Black for $2.1 billion.
His logic was in part based on the valuation of CrowdStrike, a Carbon Black competitor. At the time CrowdStrike, as you can see on the chart below, had a valuation that was nine times higher than that of Carbon Black. And you can see from the trailing-12-month revenue that CrowdStrike was a bigger company by more than $100 million, but the real story was the company’s growth at more than 100%. CrowdStrike at the time was growing much faster than Carbon Black’s 22%, justifying a significantly higher relative value.
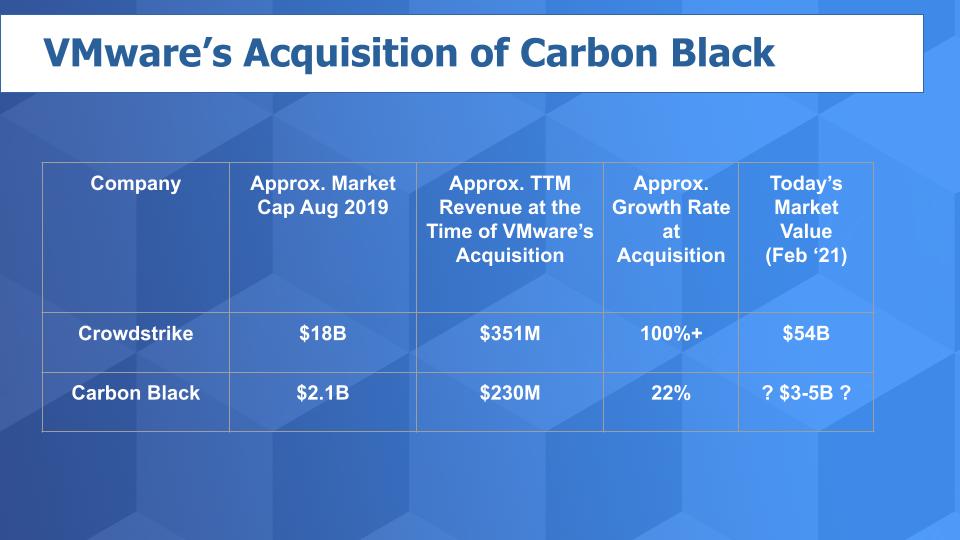
Of course, the thinking from VMware was that it could pick up Carbon Black at a discount to the market leader and inject growth and profitability into the asset by bundling into VMware’s increasingly capable security offerings. VMware created a cloud security group headed by Carbon Black Chief Executive Patrick Morley, which underscores a commitment to the sector.
Now in VMware’s recent earnings call, it said Carbon Black had “good” bookings performance. Who knows exactly what that means, but if it were significantly more than 22% (Carbon Black’s growth rate at acquisition time), our guess is that VMware would have been more effusive. So let’s assume that since the acquisition Carbon Black growth has been flattish relative to its growth at acquisition as VMware figures out how to integrate the company.
Nonetheless, we would still peg its valuation as having increased substantially since the time of acquisition – perhaps in the $3 billion-to-$5 billion range. So it’s a nice pickup for VMware in our view, which has a good track record of acquiring companies and monetizing the assets. And we think the value of Carbon Black inside of VMware will likely grow from here. Further, the ETR data on Carbon Black is encouraging.
Let’s look at how the valuations in this sector have changed since before COVID.
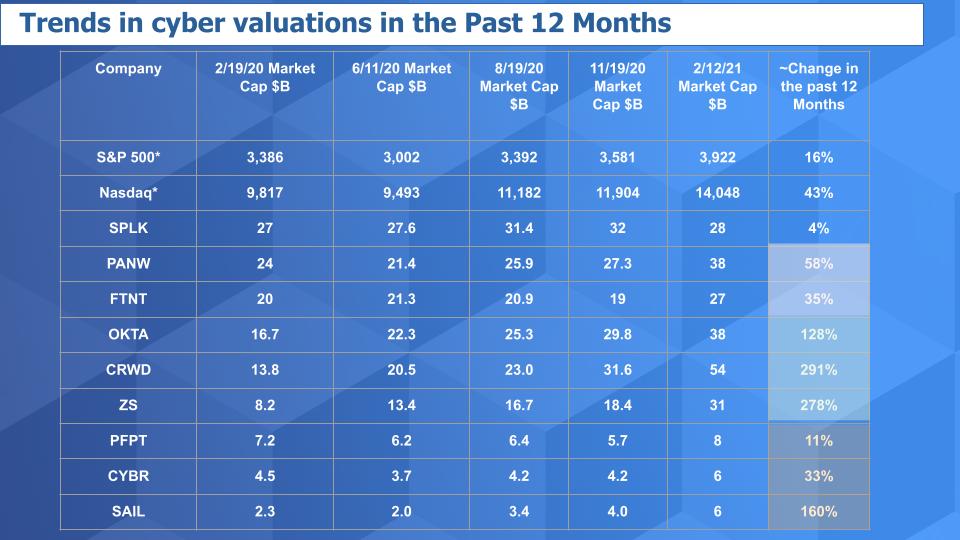
Above is an updated view of our valuation matrix since just before the pandemic hit the U.S. in earnest. You can see the S&P is up 16% from that timeframe and the Nasdaq composite up 43%. Now look at the others. Only Splunk really hasn’t seen a big uptick in valuation. And Proofpoint’s valuation hasn’t kept pace. But the others have either risen noticeably, such as CyberArk and SailPoint, bounced up such as Palo Alto, held nicely such as Fortinet or exploded as with Crowdstrike, Okta and Zscaler.
So one would think Carbon Black as a VMware asset has done pretty well along with these names and will make long-term contributions to VMware.
In addition, we would expect that the tech spending rebound this year combined with the heightened concerns over the SolarWinds hack and the tectonic shifts from the accelerated work-from-home and digital business transformation will continue to bode well for many of these names… for some time.
As we exit the pandemic and are experiencing a new digital reality, cyberthreats have never been greater. Each January if you looked back on the prior year you’d be able to say the same thing for the past several decades. And the reality is that the budget allocations and subsequent spending on cyber are asymmetric to the economic risks. In other words, the $125 billion or so spent on cybersecurity doesn’t square with the trillions of dollars in value lost each year to cybercrime. We don’t spend enough as it is and probably can’t spend our way out of this problem.

CISOs have to balance their legacy installed base security infrastructure with the shift to zero-trust, accelerated endpoint, new access management challenges and an ever-expanding cloud. And much more. Very few have the benefit of a blank sheet of paper.
Lack of talent remains the single biggest challenge for organizations, which are stretched thin — making investments in automation a trend that is not going to abate any time soon.
In cyber, all the cliches apply: There is no silver bullet. There is no rest for the weary. The adversaries are well-funded and extremely capable and they have to succeed only once to create a business disaster for an organization, whereas an organization must succeed every minute of every day. So expect more of the same with no end in sight in terms of complexity, fragmentation and Whac-A-Mole approaches to fighting cyber crime.
It hurts to say this, but it just means the fundamentals for this sector just keep getting better. That’s bad news, but it’s the reality for organizations trying to protect their data — and it’s good news with lots of opportunities for investors.
Remember these episodes are all available as podcasts wherever you listen. Ways to get in touch: Email david.vellante@siliconangle.com, DM @dvellante on Twitter and comment on our LinkedIn posts. Check out ETR for the survey data.
Here’s the full video analysis, with a slightly new experimental format to our production – let us know what you think:
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.