 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The rapid pace of cloud adoption has changed the way organizations approach cybersecurity. Specifically, the cloud is increasingly becoming the first line of cybersecurity defense.
As such, along with communicating to the board and creating a security-aware culture, the chief information security officer must ensure that the shared responsibility model is being applied properly. The DevSecOps team has emerged as the critical link between strategy and execution, while audit becomes the “free safety” in the equation – the last line of defense.
In this Breaking Analysis, we share our puts and takes from the recent AWS re:Inforce conference with an update on the latest hyperscale infrastructure-as-a-service market shares and insights from ETR survey data. We’ll also dig deeper into some technical aspects of Amazon Web Services Inc.’s Nitro, a system we believe is one of AWS’ secret weapons, with a focus on confidential computing and what it means for the future of systems architecture.
It’s earnings season and that’s what many people want to talk about. Including us.
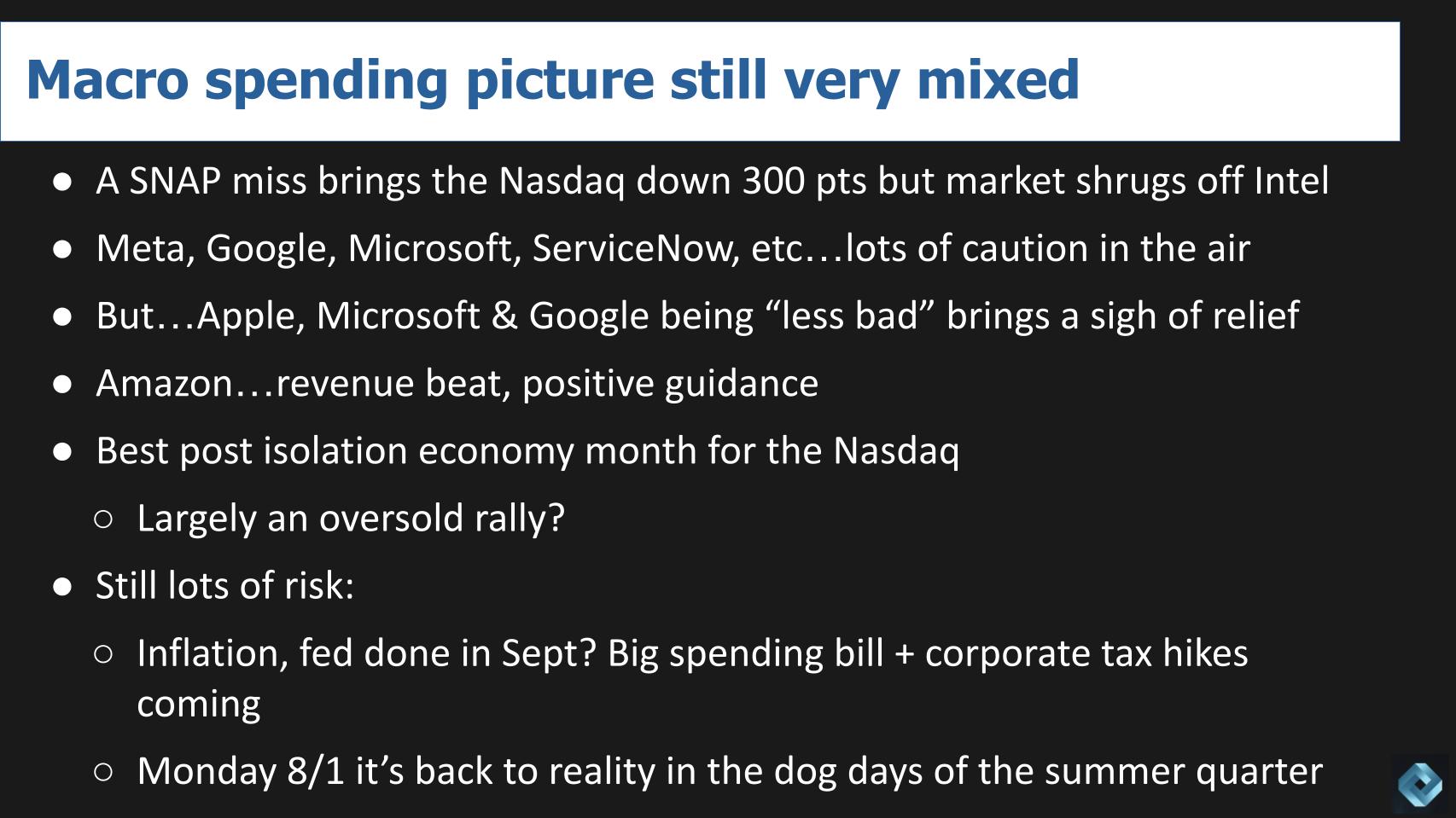
As we reported last week, the macro spending picture is very mixed — and weird. Think back to a week ago when Snap Inc. reported. A player such as Snap misses earnings and the Nasdaq drops 300 points. Meanwhile, Intel Corp., the great semiconductor hope for America, misses by a mile, cuts its revenue outlook by 15% for the year, and the Nasdaq rises nearly 250 points just ahead of the close. Go figure.
Reports from Meta Platforms Inc., Google LLC parent Alphabet Inc., Microsoft Corp., ServiceNow Inc. and some others underscored cautious outlooks, especially from those exposed to the advertising revenue.
At the same time, Apple, Microsoft and Google were, let’s say, “less bad” than expected and that brought a sigh of relief.
Then there’s Amazon.com Inc., which beat on revenue, beat on cloud revenue, gave positive guidance and was up double digits most of the day.
The Nasdaq has seen its best month in the post-isolation economy, which Breaking Analysis contributor Chip Symington attributes to what he calls an “oversold rally.”
But there remain many unknowns. How bad will inflation be? Will the Fed really stop tightening after September? The Senate just approved a big spending bill along with corporate tax hikes. What does that mean for growth and the economy in general? And on Monday, Aug. 1, the market will likely realize that we’re deep into the summer quarter and there’s still lots of risk, volatility ahead and plenty of work to be done. Which is why it’s not surprising that investors sold the Nasdaq at the close on Friday.
Are people ready to call the bottom? Some maybe but still lots of uncertainty.
The cloud continues its relentless march, despite some very slight deceleration in growth rates from the two leaders and a major dip in Google Cloud’s growth.
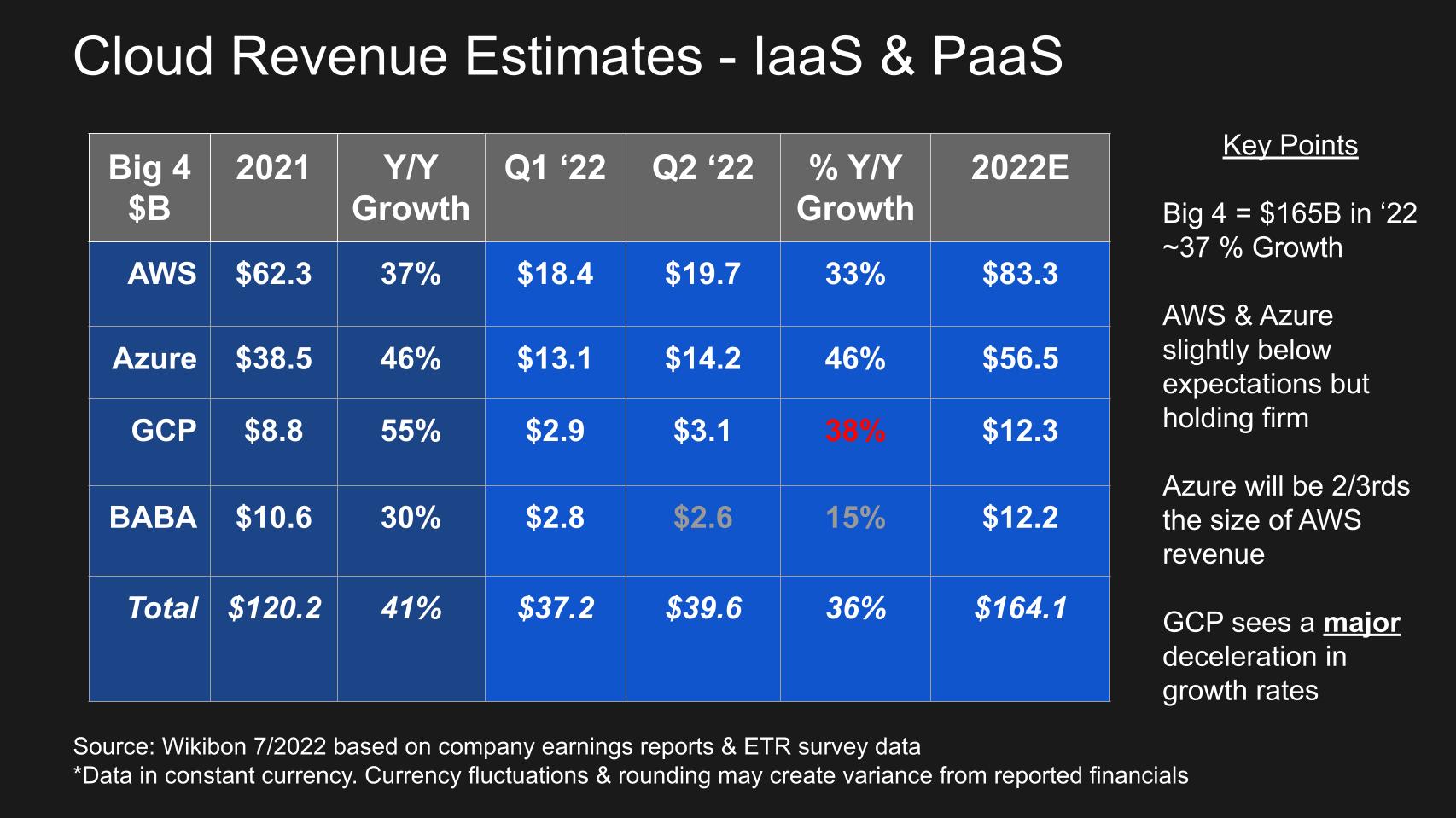
The chart above gives update of our big four IaaS quarterly revenue data. The big four hyperscalers will account for $165 billion in revenue this year, slightly lower than we had forecasted for the year back in the spring. We expect AWS to surpass $83 billion. Azure will be more than two-thirds the size of AWS, a milestone for Microsoft.
Both AWS and Azure came in slightly below our expectations but still very solid growth at 33% and 46%, respectively. Remember, both GCP and Azure play a shell game and hide the ball on their true IaaS numbers, so we have to use survey data and other means of estimating… but this is how we see the market shaping up in 2022.
Google is the big concern. By our estimates, GCP’s growth rate decelerated from 47% in Q1 to 38% this past quarter. That’s well below where it needs to be to catch up with the leaders. Google Cloud in our view should be sustaining 60%-plus growth rates at this stage of maturity in order to keep up with the two giants. By our estimates, it’s nowhere close to that level.
The question we often get is: Why? Our answer is, it’s not the tech. Google has great tech – perhaps the best in the industry. It has awesome engineering, massive scale, a global footprint and strong offerings, especially in data, database and artificial intelligence. It has all the ingredients but one, which we believe is a fundamental go-to-market problem. Google has a culture of strong engineering, with revenue coming from clicks on ads while it sleeps. Thomas Kurian, who came from a strong go-to-market culture at Oracle Corp., must be frustrated that he can’t get Google’s enterprise sales “right.”
Before we leave the overall cloud discussion, below is some Enterprise Technology Research data that shows the Net Score or spending momentum granularity for each of the hyperscalers.
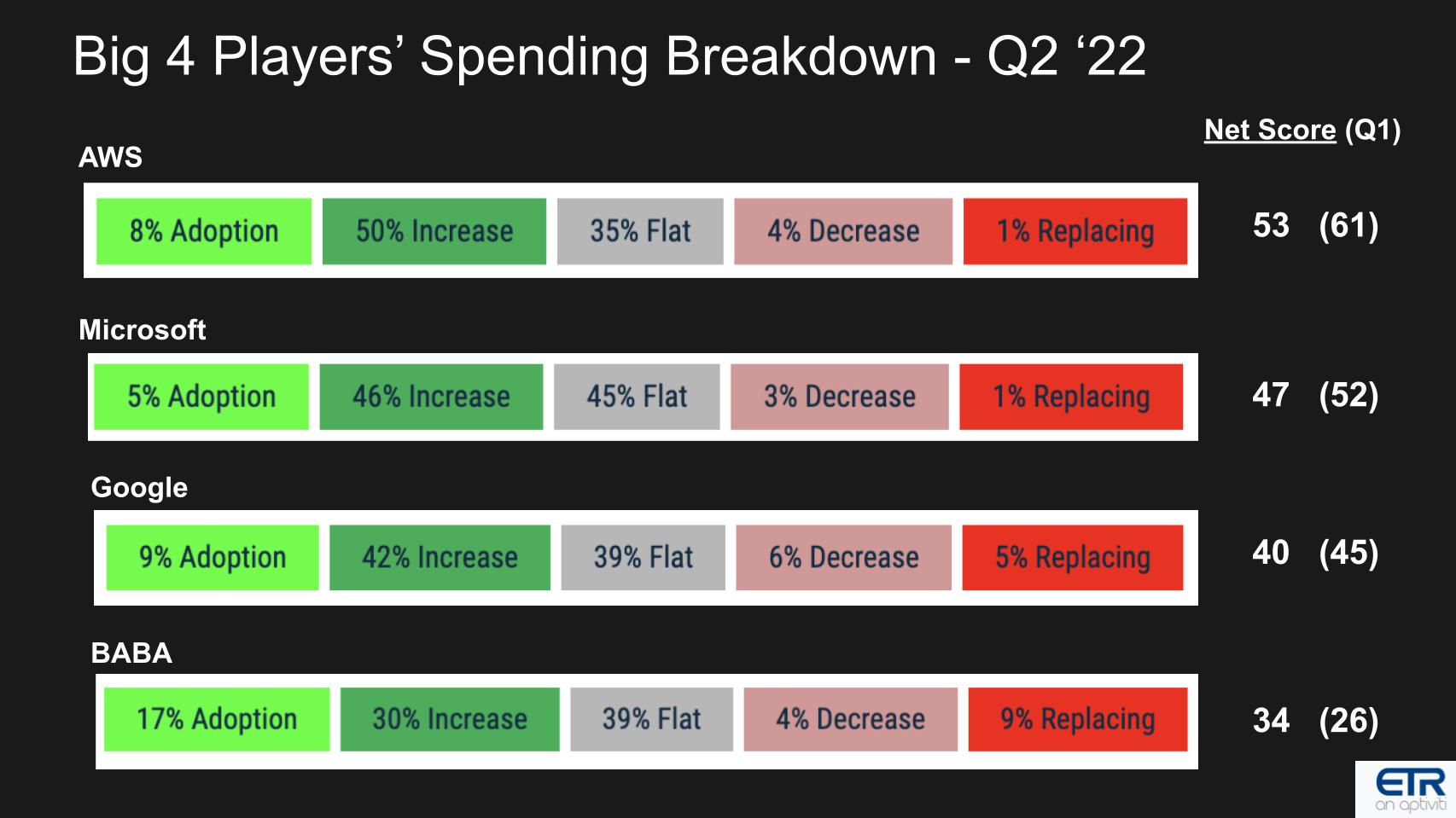
The bars above show the breakdown for each company with the Net Score on the right and, in parenthesis, the Net Score from last quarter. Lime green is new adoptions, forest green is spending up 6% or more, gray is flat, pink is 6% down or worse and the bright red is replacement/defections and represents churn.
Subtract red from green and you get Net Score. One note is this data shows each company’s overall portfolio, not just cloud, so it’s a bit of a mixed bag but there are a couple of points worth noting.
First, anything above 40 is considered elevated. AWS is well above 40, as is Microsoft, and if you isolate Microsoft to just Azure, it jumps even higher than AWS, supporting Azure’s higher growth rate as compared with the AWS cloud. Google is just barely hanging on to the 40 line and Alibaba is well below – with both Google and BABA showing much higher replacements.
But here’s the key point: AWS and Azure have virtually no churn at 1% each. And all four companies are experiencing single-digit numbers in terms of decreased spending within customer accounts. People may be moving some workloads back on-premises … selectively. But repatriation is definitely not a trend to bet the house on in our view.
We generally believe AWS has the “best” cloud for IaaS, roughly defined as the most comprehensive set of services with the most vibrant ecosystem and the best security. Its focus on developers versus solutions gives its ecosystem more room to move, in our view. However, Microsoft’s massive software estate gives it significant captive advantages in terms of market penetration for its IaaS. Essentially its software as a service serves as a sort of “heat shield” for any underlying IaaS disadvantages and powers the company’s Azure momentum.
We believe AWS will hit $100 billion in IaaS revenue in 2023, ahead of Microsoft. But the race to $200 billion could favor Microsoft without some major total addressable market expansion moves by AWS.
Let’s get to the main subject of this Breaking Analysis. TheCUBE was at AWS re:Inforce in Boston this week and we have some observations to share. First, we had keynotes from Stephen Schmidt, the chief security officer of Amazon overall, CJ Moses, the CISO for AWS, and Kurt Kufeld of AWS, and Lena Smart, MongoDB Inc.’s CISO, also keynoted and came on theCUBE.

A striking point Schmidt made was Amazon sees more data points in a day than most organizations see in a lifetime — billions each day and quadrillions over a fairly short period of time. Quadrillion is a number with 15 zeros, by the way.
The conference content was organized into five areas: data protection and privacy, governance risk and compliance or GRC, identity, network security and threat detection.
Re:Inforce brings a lot of best practice guidance to practitioners. In 2019, the first re:Inforce, there was a real focus on understanding and applying the shared responsibility model. This year there was less of a need to educate the crowd on that front and more focus on best practice advice, how to get the most out of AWS tooling and how to think conceptually about security. Schmidt, for example, had a strong statement saying he can assure you with a 100% certainty that “single controls and binary states will absolutely fail…,” hence the importance of layered security.
Single controls and binary states are guaranteed to fail. — Stephen Schmidt, CSO of Amazon
We heard some chat about getting ready for the future where quantum computing threatens to hack all the cryptographic algorithms and how AWS is evidently getting out in front of that.
And by its prominent presence, the ecosystem was there in force to talk about their role in filling gaps and picking up where AWS leaves off.
We also heard a bit about ransomware defense, but surprisingly, at least in the keynote, no discussion about air gaps.
There was a lot of discussion about AWS services to help with threat detection and container security and DevOps, etc. But there wasn’t a lot of specific talk about how AWS is simplifying the life of the CISO. Maybe it’s inherently assumed as AWS did a good job of stressing that security is job one. But you had to wonder if the world is getting simpler or more complex with cloud.
And you might say, “Well, c’mon, of course it’s better with cloud.” But the fact is attacks are up, the threat surface is expanding and new exfiltration records are being set every day. The hard truth is the cloud is driving businesses forward and accelerating digital… and those businesses are now more exposed than ever. The adversary is well-funded, motivated and highly sophisticated, and organizations are constantly playing a game of Whac-A-Mole.
And that’s why security has become such an important topic to boards and the entire organization.
The other epiphany we had at re:Inforce is that there are new layers taking shape and a cloud-first trust framework emerging in cyber. Roles are shifting as a direct result of the cloud. And this first hit us in a conversation with a longtime cyber practitioner and Wikibon colleague from our early days, Mike Versace. We spent the better part of two days testing the premise. The graphic below is an attempt to describe those conversations visually.
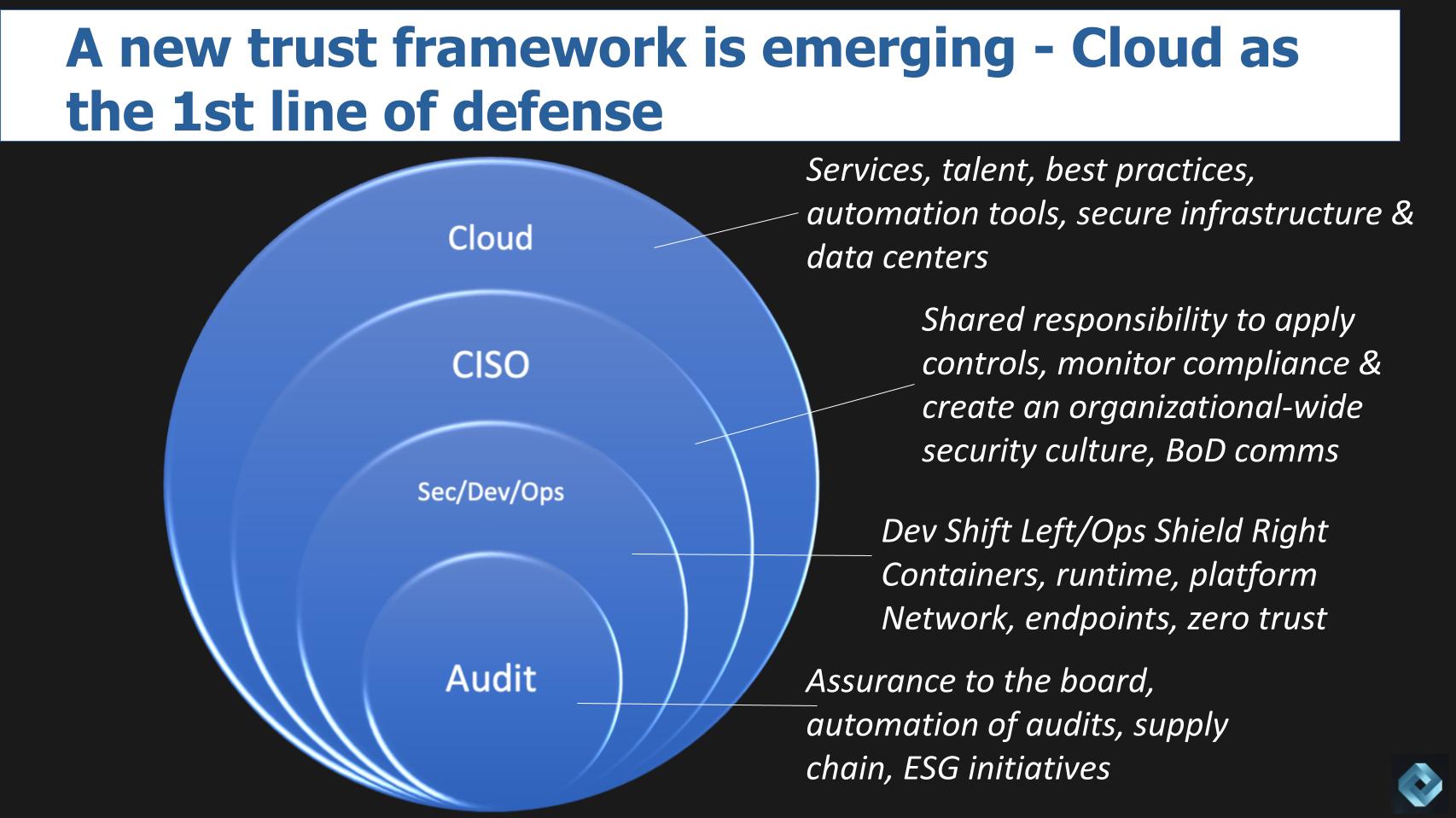
The cloud is now the first line of defense. AWS specifically but hyperscalers generally provide the services, the talent, best practices and automation tools to secure infrastructure and their physical data centers. And they’re really good at it. The security inside of hyperscale clouds generally but especially AWS is best of breed — world-class.
That first line of defense does take some of the responsibility off CISOs but they have to understand and apply the shared-responsibility model properly. Where the cloud provider leaves it to the customer, of course, to make sure that the infrastructure services they’re using are properly configured. So in addition to creating a cyber-aware culture and communicating up to the board, the CISO has to ensure compliance with and adherence to the model. That includes attracting and retaining the talent necessary to succeed.
Now, on the subject of building a security culture, we hosted Lena Smart, MongoDB’s CISO on theCUBE. She shared one of the approaches she uses to build a security culture, called the Security Champions Program.
The security champions program is purely voluntary. We have over a hundred members. There’s no bar to join. You don’t have to be technical. If you’re an executive assistant who wants to learn more about security, like my assistant does, you’re more than welcome. People grade themselves, when they join us, we give them a little tick box. Like five is, I walk in security water. One is, I can spell security but I’d like to learn more. Mixing those groups together has been game changing for us.
The next layer is really where it gets interesting: DevSecOps. We hear about shifting left – it implies designing security into the code at the dev level. Shift left and shield right is the buzz phrase, meaning developers designing security into code and ops making sure that you’re still putting up proper defenses. But it’s getting more and more complicated because there are more layers within the development cycle. For example, securing the container so the app code can’t be threatened by back door breaches or vulnerabilities in the container. Then worrying about securing the runtime to make sure the code is maintained and compliant… and the DevOps platform so that change management doesn’t create gaps and exposures.
This just speaks to application security. What about the network and implementing zero-trust principles and securing endpoints and machine to machine and human to app interactions? So that’s a lot of burden being placed on the DevOps teams. They’re not traditionally trained as security experts, so they have to partner with SecOps to succeed.
And finally there’s audit, which is the last line of defense — or the free safety for you football fans. They have to do more than just tick a box for the board… that doesn’t cut it anymore. They really have to know their stuff and bring security expertise to the audit function to make sure that what they’re signing off on is real. And an emerging trend is ESG – environmental, social and governance — which is becoming more important each week. Auditing this capability in the partner supply chain and ensuring the ecosystem is green, inclusive and also secure.
So you can see, while much of this stuff has been around forever, the cloud is accelerating innovation and the pace of delivery is changing rapidly.
Next we want to share a graphic that we shared last week but with a different twist.
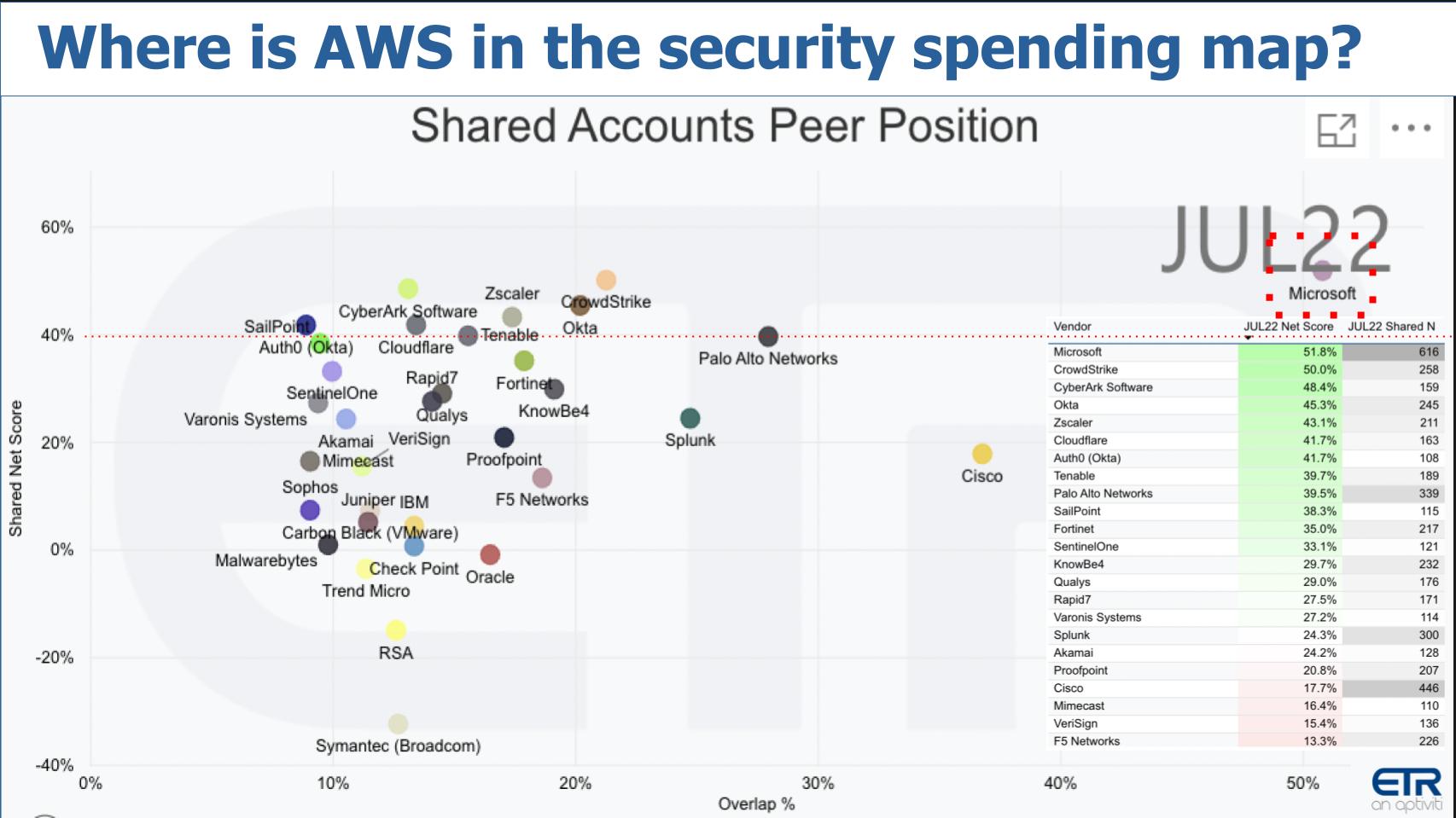
Above is an XY graphic with Net Score or spending velocity on the vertical axis and Overlap or presence in the data set on the horizontal axis, with that magic 40% red line shown. We won’t dig into the data because we did that last week. But we’ll make two points.
First, look at Microsoft in the upper right corner. It’s big in security and attracting a lot of dollars in the space. And every time we’ve run this chart, it’s hard not to wonder: ‘Where the heck is AWS – why isn’t it on there?’ If security is so important to AWS and its customers, why aren’t they spending with Amazon?
On theCUBE, we asked this very question to Merritt Baer, who resides in the office of the CISO at AWS:
Listen to Merritt Baer explain why Amazon may not show up in the ETR security Taxonomy.
This doesn’t mean don’t spend on security. There is a lot of goodness that we have to offer in ESS, external security services. But I think one of the unique parts of AWS is that we don’t believe that security is something you should buy. It’s something that you get from us. It’s something that we do for you a lot of the time. I mean, this is the definition of the shared responsibility model, right?
Now, maybe that’s good messaging to the market. In other words, while Merritt didn’t say it, essentially Microsoft charges for security and is making good revenue from the space. At AWS, it comes with the package.
While you might be thinking in the back of your head that AWS can make up this “security comes for free” with egress charges, we want to turn to a powerful example of where security is designed in, and that leads us to the notion of confidential computing. This is something that we’ve explored in detail with our colleague David Floyer in previous Breaking Analysis episodes.
At re:Inforce, through the analyst relations program, we had an opportunity to sit down with Arvind Raghu and J.D. Bean, two security experts from AWS, to talk about this subject. Here we share what we learned and why we think it matters.
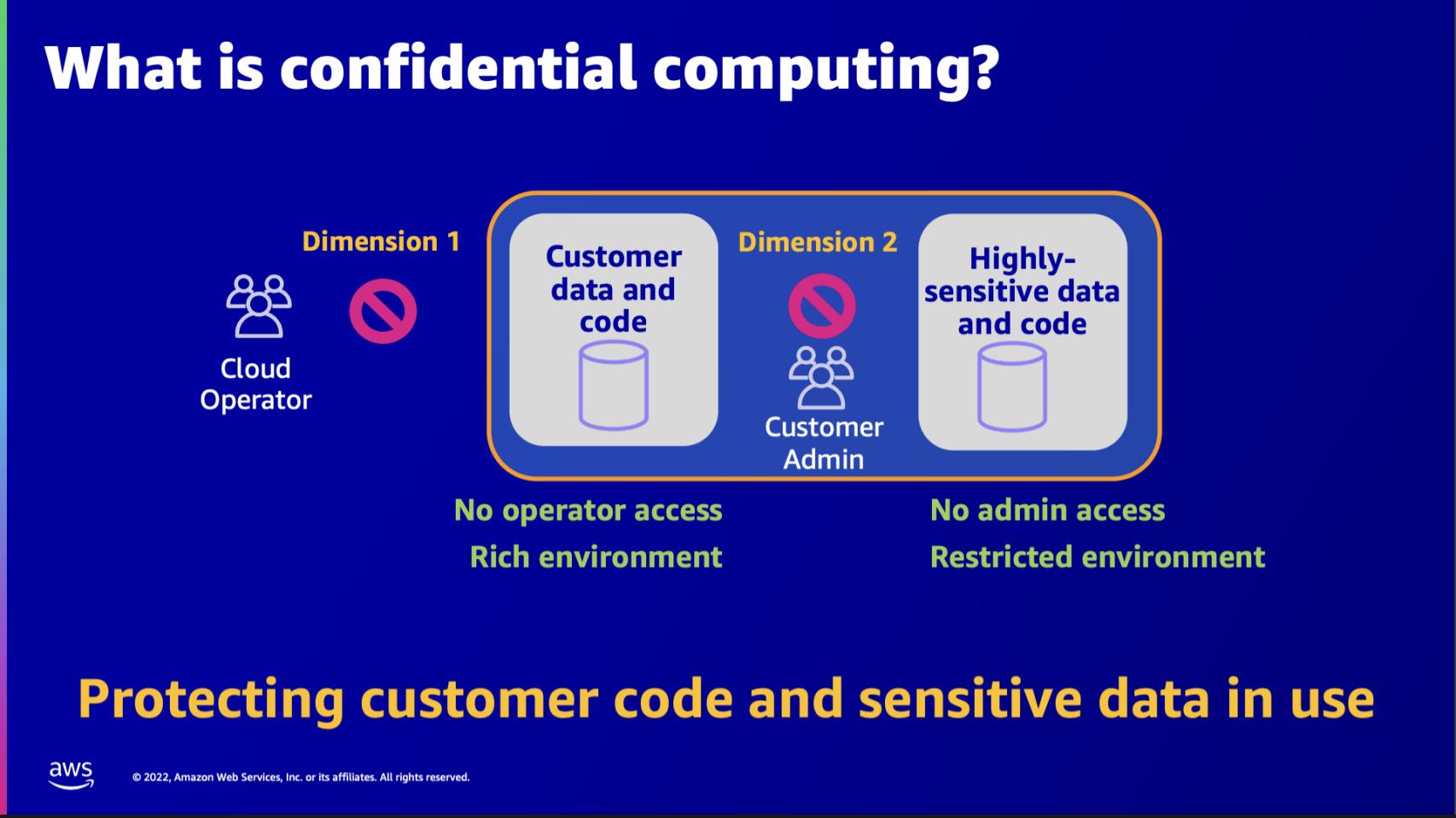
To AWS, confidential computing is the use of special hardware and firmware that protects customer code and data from any unauthorized access while the data is in use – i.e., while it’s being processed. And there are two dimensions here: 1) protecting the data and code from operators on the cloud provider side – in this case AWS; and 2) protecting the data and code from the customers themselves. In other words, from admin-level users or possible malicious actors on the customer side where the code and data is being processed.
And there are three capabilities that enable this: the AWS Nitro system, which is the foundation for virtualization; Nitro Enclaves, which isolate environments; and the Nitro Trusted Platform Module or TPM, which enables cryptographic assurance of the integrity of the nitro instances.
We’ve talked about Nitro in the past and we think it’s a revolutionary innovation. So let’s dig into that a bit. The slide below describes how AWS architected a new virtualization capability for the cloud and its alternative Arm processors, such as Graviton.
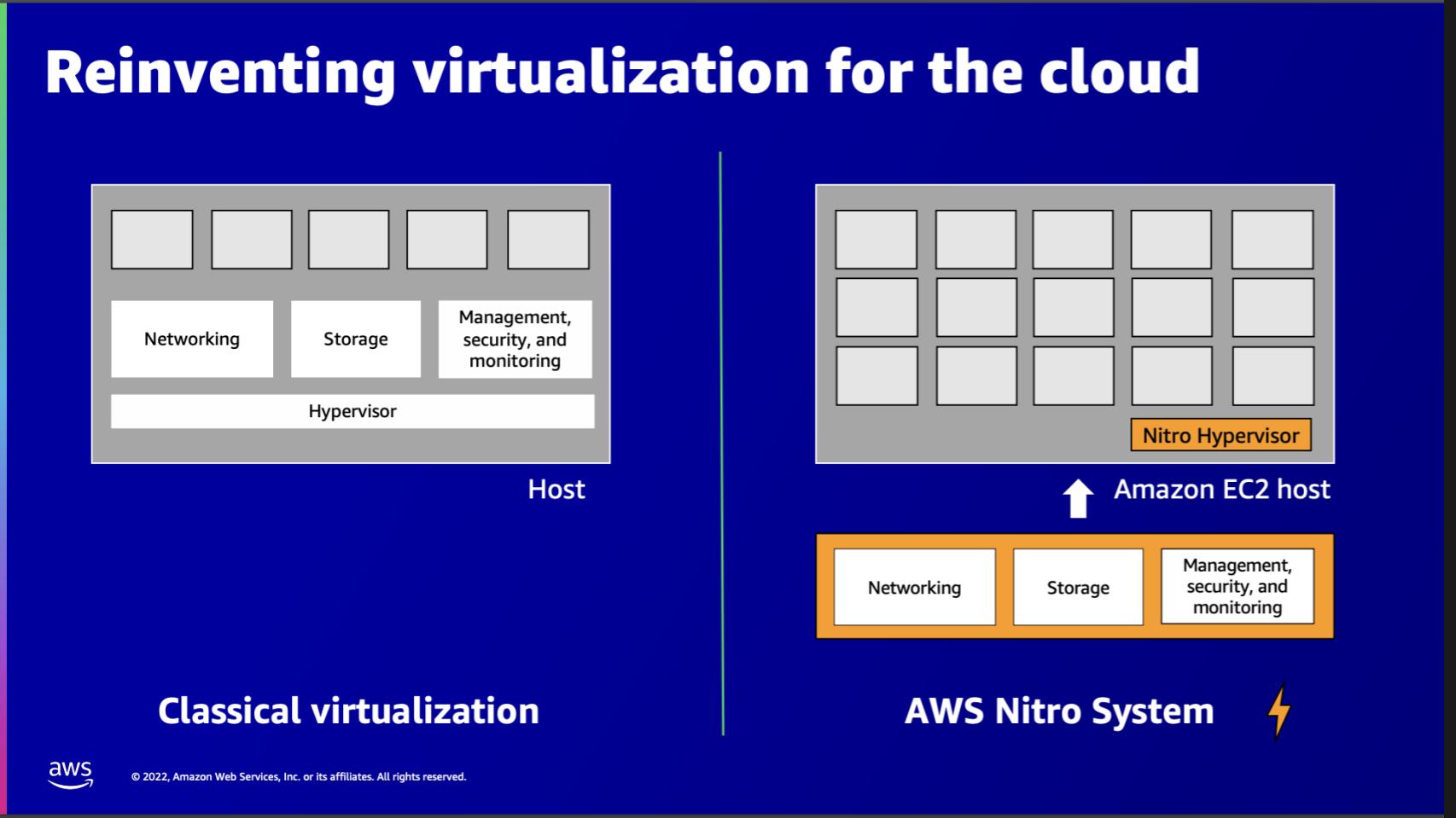
On the left hand side is a classical view of a virtualized architecture. You have a single host or server and the white boxes represent processors on a main board, e.g. x86 – could be Intel or Advanced Micro Devices, or alternative architectures.
And you have the hypervisor at the bottom, which translates instructions to the central processing unit, allowing direct execution from a virtual machine into the CPU. But notice you also have blocks for networking, storage and security. And the hypervisor emulates or translates I/Os between the physical resources and the virtual machines.
And though it’s not shown in the graphic, there’s an operating systems, which is privileged and provides the services to the VMs.
On the righthand side, you have the Nitro System. And you can see immediately the difference because the networking, storage and security/management and the like have been separated from the hypervisor and the main board, which has the Intel, AMD, Graviton, Trainium, whatever XPUs are in use.
And you see the orange Nitro Hypervisor? That’s a purpose-built, very lightweight component for this system. And all the other functions are separated in isolated domains. So AWS has architected very strong isolation between the cloud software and the physical hardware running workloads — i.e. those white boxes on the main board.
This will run at practically bare-metal speeds. And there are other benefits, but one of the biggest is security.
An as we’ve previously reported, this came out of AWS’ acquisition of Annapurna Labs, which we’ve estimated was picked up for a measly $350 million, a drop in the bucket for AWS to get such a strategic asset.
And there are three enablers here: the Nitro Cards, which are accelerators to offload wasted work done in traditional architectures, typically done by x86; the Nitro Security Chip, which is embedded into and extends the root of trust to the main board hardware; and finally the Nitro Hypervisor, which allocates memory and CPU resources.
The Nitro cards communicate directly with the VMs without the hypervisors getting in the path. And all the data is encrypted while it’s in motion.
We presumed but wanted to confirm with AWS that this an Arm-based architecture and not some type of hybrid using x86 and Arm? Here’s AWS’ response:
The SOCs for these hardware components are purpose-built and custom-designed in-house by Amazon Annapurna Labs – the same group responsible for other silicon innovations such as Graviton, Inferentia, Tranium and Aqua. The Nitro Cards are Arm-based and do not use x86 or x86_64 CPUs.
You may be asking, why should we care about all this technical mumbo-jumbo? Well, first, this is an example of the earlier point that AWS designs in a lot of security innovations. It’s not the only one, but Nitro has been a decade of R&D in the making. Second is this is not just a security bolt-on. It’s an entirely new architecture, which we’ve reported on extensively.
A year ago, with David Floyer, we published the piece above explaining why this matters. Nitro, Graviton and AWS’ leverage of Arm-based architectures are secret weapons of Amazon that we believe are well ahead of the industry. These innovations are enabled by the Annapurna acquisition and AWS has the volume economics to make its own custom silicon. It is leveraging the Arm standard software, ecosystem and fabrication volume to revolutionize enterprise computing.
Nitro, with the alternative processor architectures such as Graviton and others, enables AWS to be on a performance, cost and power consumption curve that blows away anything we’ve ever seen from Intel.
Intel’s disastrous earnings results that we saw this past week are a symptom of this silicon megatrend. In the same way Intel and x86 destroyed the market for RISC chips, thanks to PC volumes, Arm is blowing away x86 with volume economics that can’t be matched by Intel. Our predictions is that these innovations will migrate to enterprise computing, which is Intel’s stronghold. That stronghold is getting eaten away by AMD, Nvidia Corp. and Arm Ltd., in the form of Graviton and other Arm-based alternatives.
Apple Inc., Tesla Inc., Amazon, Google, Microsoft, Alibaba and others are designing custom silicon and doing so much faster than Intel can go from design to tap- out, roughly cutting that time in half. And the premise of the piece above is that every company needs a Nitro to enable alternatives to the x86 in order to support emergent workloads that are data-rich and AI-based… and to compete economically.
So while at re:Inforce we heard that the impetus for Nitro was security, the Arm ecosystem and its ascendency has enabled, in our view, AWS to create a platform that will set the enterprise computing standard for this decade and beyond.
Thanks to Alex Myerson, who does the production, podcasts and media workflows for Breaking Analysis. Special thanks to Kristen Martin and Cheryl Knight, who help us keep our community informed and get the word out, and to Rob Hof, our editor in chief at SiliconANGLE.
Remember we publish each week on Wikibon and SiliconANGLE. These episodes are all available as podcasts wherever you listen.
Email david.vellante@siliconangle.com, DM @dvellante on Twitter and comment on our LinkedIn posts.
Also, check out this ETR Tutorial we created, which explains the spending methodology in more detail. Note: ETR is a separate company from Wikibon and SiliconANGLE. If you would like to cite or republish any of the company’s data, or inquire about its services, please contact ETR at legal@etr.ai.
Here’s the full video analysis:
All statements made regarding companies or securities are strictly beliefs, points of view and opinions held by SiliconANGLE media, Enterprise Technology Research, other guests on theCUBE and guest writers. Such statements are not recommendations by these individuals to buy, sell or hold any security. The content presented does not constitute investment advice and should not be used as the basis for any investment decision. You and only you are responsible for your investment decisions.
Disclosure: Many of the companies cited in Breaking Analysis are sponsors of theCUBE and/or clients of Wikibon. None of these firms or other companies have any editorial control over or advanced viewing of what’s published in Breaking Analysis.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.