 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The class of malware called infostealers continues to evolve into a more lethal threat.
These threats are software that can steal sensitive data from a victim’s computer, typically login details, browser cookies, saved credit cards and other financial information. SiliconANGLE has covered their role in the past in various ransomware and other attacks, including Stealc and LockBit in February and EventBot, an Android-based infostealer, back in April 2020.
Unfortunately, criminals continue to enhance this malware genre, and two new reports released this week document their latest efforts.
One trend is the use of automation to spread their impact. “Cybercriminals work hard to develop new commodity stealers and release them into the automated botnet markets at affordable prices to appeal to a wider audience,” said Yael Kishon, who authored the report from the KELA Cybercrime Prevention research group. The group tracks various infostealer versions and their creators.
The infostealer marketplace is a chaotic one, as new versions come and go, and as some criminals are put behind bars. Last year, the Ukrainian developer behind the Raccoon stealer was arrested and faced charges. Yet months later, a new version was being sold.
The typical role for this malware is that it’s used as a foundation by other threat actors to launch targeted campaigns that employ ransomware and data extortion elements using the stolen login credentials. The genre has expanded over the years to include better integration with other malware tools that can parse the stolen data and organize it for specific targeted victims.
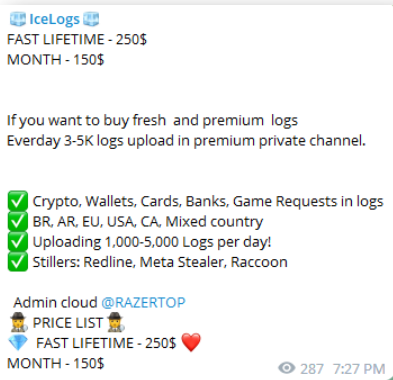
IceLogs is selling logs obtained through Redline, META and Raccoon stealers (Image: KELA)
These malware versions have subscription-based pricing just like any other software as a service, with different pricing tiers for added traffic analysis and obfuscation features. Call it malware as a service.
One stealer called Aurora has more than 6,000 subscribers with a monthly price of $125. Kishon documents the growing trend of using Telegram channels to communicate and sell the stolen data, along with subscriptions for the stealer software itself.
Stealc now targets more than 22 web browsers, 75 plugins and 25 desktop wallets, according to Bleeping Computer. Another stealer called LummaC2 can steal onetime multifactor authentication codes from a variety of authenticator applications, and is being used to steal data from websites masquerading as OpenAI and ChatGPT versions.
The second report is from Secureworks Inc. Counter Threat Unit researchers.
They document the evolving underground economy of the stealer universe, including one of the biggest sites, called Russian Market.
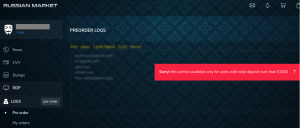
The Russian Market underground site now offers the ability to preorder stolen data (Image: Secureworks)
The site offers 5 million different data collections for sale and is about 10 times the scale of its biggest competitor. Specific data collections can even be pre-ordered, as the adjacent screen capture shows. The report has a detailed comparison of the five most common stealers in terms of pricing, programming language used, targeted crypto wallets and applications, and hosting versions.
Many stealers work quickly. In some cases they can finish their data collection and transmission activities within several seconds once they’re activated. The report documents several other marketplaces for stealers that feature botnets, custom browser plug-ins and other enhancements that make it easier for threat actors to built malware with very little programming or skills.
Secureworks also documents the increased role of Telegram, motivated by a series of high-profile stealer takedowns by law enforcement last year. “Researchers have observed scammers on Telegram mimicking real threat actors by creating fake profiles,” they said. “This lack of reputation status and the prevalence of scammers is likely to undermine trust, preventing threat actors from fully adopting Telegram.”
One disturbing trend is how stealers have been embraced by state-sponsored malware groups for cyber espionage operations. For example, Russian groups have deployed the Graphiron stealer against Ukrainian targets, and Chinese groups have deployed them against various enemies across Asia.
The researchers found that the stealers are getting more sophisticated, making them harder to find and to remove. “Bring your own device policies that were created during COVID which let users access corporate assets from infected personal devices have lead to compromises of corporate systems,” they noted. Apparently COVID wasn’t the only infection to spread during the pandemic.
THANK YOU