 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
The revelations last week that Chinese hackers had breached a number of U.S. government email accounts indicate the problem is a lot worse than was initially thought, according to new research today by Wiz Inc.
Indeed, this hack could turn out to be as damaging and as far-reaching as the SolarWinds supply chain compromises of last year. Earlier this week, Microsoft also blogged further details about what is being called the Storm-0558 attack, explaining further some of the causes and tracking the movements of the attackers through its Azure cloud network and services.
Well, almost. The original reports of the breach centered on a set of compromised encryption keys for Microsoft’s Exchange online email services. But Microsoft’s latest blog post still doesn’t completely connect all the dots of what happened. That has led some reporters, such as Andy Greenberg of Wired magazine, to speculate on several scenarios on how the keys were stolen or mishandled.
“The threat actor was able to obtain new access tokens by presenting one previously issued from this API due to a design flaw,” the new report from Wiz says, though it has since been fixed. These tokens were used to access emails from Outlook Web Access and Outlook.com services.
However, the report from Wiz goes further. “The compromised signing key was more powerful than it may have seemed and was not limited to just those two services,” Wiz reports. It found this key could be used to obtain access to a variety of services that use Azure Active Directory or AAD for authentication using the “login with Microsoft” sequence.
“Identity provider’s signing keys are probably the most powerful secrets in the modern world,” Wiz notes. The researchers found that all Azure v.2.0 personal accounts make use of either seven or eight public keys, and that the compromised key was able to pollute OpenID tokens used to login to these AAD applications. It published this chart showing who is at risk:
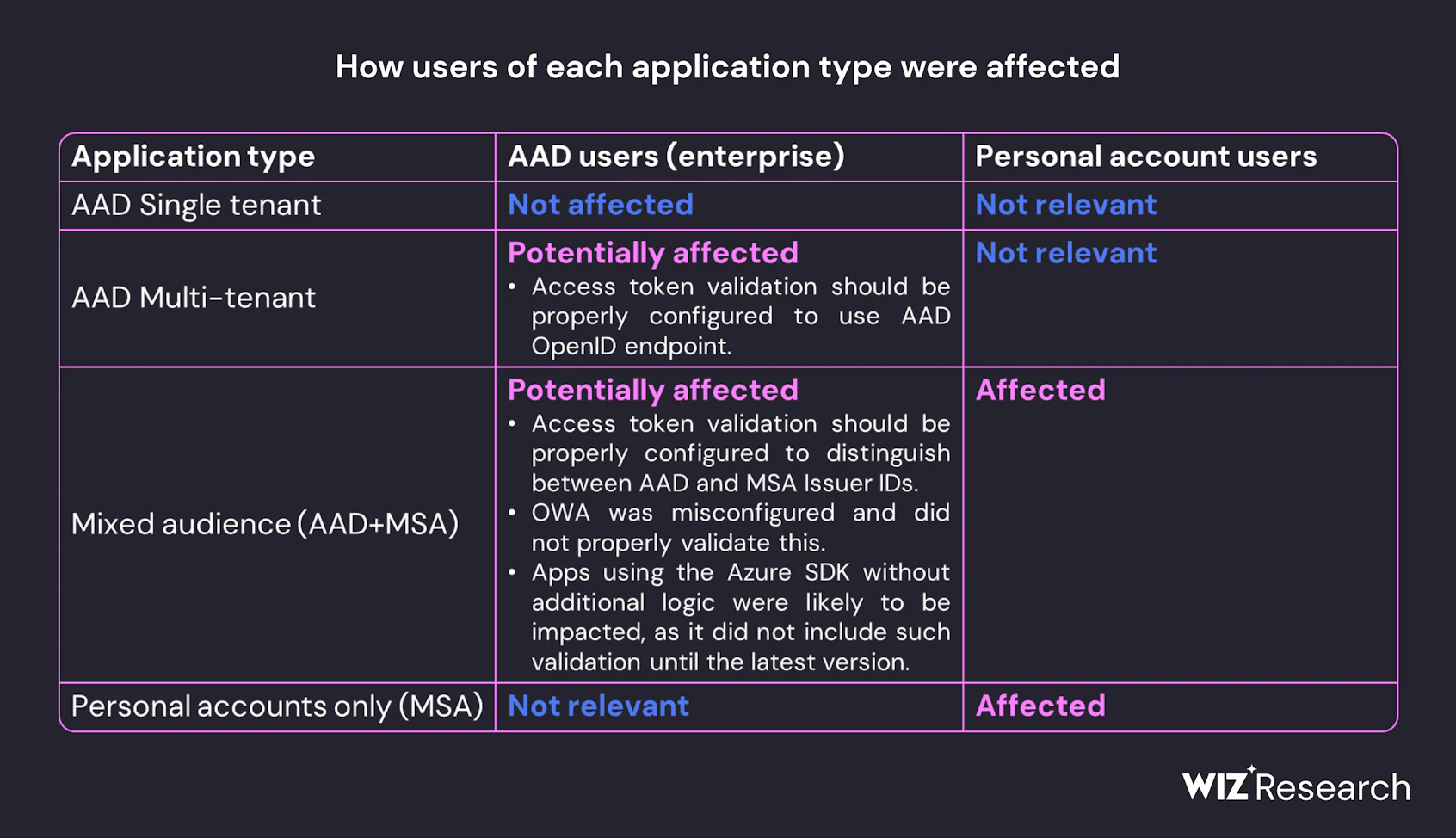
Wiz recommends customers identify all potentially affected applications by searching for forged keys, updating any Azure SDK instances and checking to ensure that they don’t use a cached version of any Microsoft OpenID certificates. If the latter circumstances are found, customers should refresh their caches.
Wiz has other specific operational recommendations as well, and says organizations shouldn’t pull any punches: It says the task ahead to root out any potential compromises will be a long slog.
Microsoft pushed back on the report, emailing Cybersecurity Dive to say that the Wiz claims aren’t based on any evidence. That’s curious given the amount of telemetry data contained in the Wiz report.
There is some good news this week potentially to counterbalance this breach. Microsoft announced a change in its Azure logging pricing scheme and will include access to a wider collection of log data in its free tiers. This collection is a visualization tool called Microsoft Purview Audit. The premium level will be free beginning in September and includes more than 30 different data types and available over longer historical time horizons.
This change could have been a coincidence – Microsoft claimed it was working on it for some time – but it also shows how it’s becoming more competitive with other cloud services that offer log analysis tools. For example, Google Cloud Platform offers its tools mostly for free. Amazon Web Services Inc. has a free tier for basic analysis, and it does meter heavier usage like its other services.
However, though the enticement of better analysis is welcome, the Storm-0558 breach is tremendously bad news for potentially millions of users who have used the “log in with Microsoft” and Microsoft OpenID identity shortcuts with their account logins. Just like users who have chosen to “log in with Facebook” to authenticate themselves, users place an inordinate level of trust in a third party to maintain an entire secure cryptographic infrastructure.
That trust may be misplaced, especially in light of the latest Storm-0558 details. Wiz believes “this event will have long-lasting implications on our trust of the cloud and the core components that support it, above all, the identity layer which is the basic fabric of everything we do in cloud.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.