 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Cisco Systems Inc.’s Talos Intelligence unit posted today new findings about the North Korean hacking group called Lazarus that outline new ways it’s targeting attacks.
“We have observed Lazarus target companies in the manufacturing, agricultural and physical security sectors,” their analysts wrote in the post. The group has been around since 2010 and was responsible most recently for compromising the CyberLink multimedia software to distribute its malware last month.
More notably, it took advantage of Log4j vulnerabilities in 2022 and was behind the 2017 WannaCry ransomware attacks that paralyzed many around the world. Talos and other security researchers have concluded that Lazarus is more of a consortium of different subgroups that independently develop their own malware campaigns.
Lazarus certainly has been busy this past year, with several different remote access Trojans using oddball development frameworks, most recently using the DLang programming language. It’s constantly improving its craft, if one could call it that, by developing more nimble and smaller footprint code and figuring out new ways to hide its intrusions to avoid quick detection.
It has also been busy refining its social engineering ploys. This blog on GitHub from the summer describes various attempts to infiltrate cryptocurrency application developers.
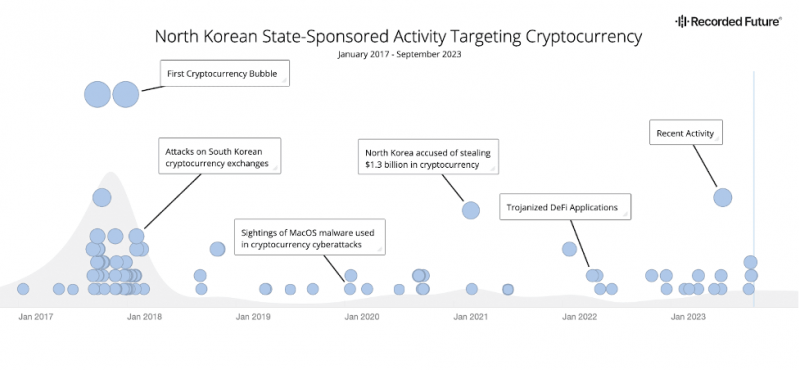
Researchers at Recorded Future’s Insikt Group tracked the group’s history of stealing various cryptocurrencies in a recent report. They concluded the group collected $3 billion in equivalent funds over the past six years, with more than half of it stolen in the past year.
That’s a significant portion of North Korea’s defense budget as well as half of the total amount of stolen funds that can be tracked, to put it in perspective. The pattern of activities is shown in the timeline below.
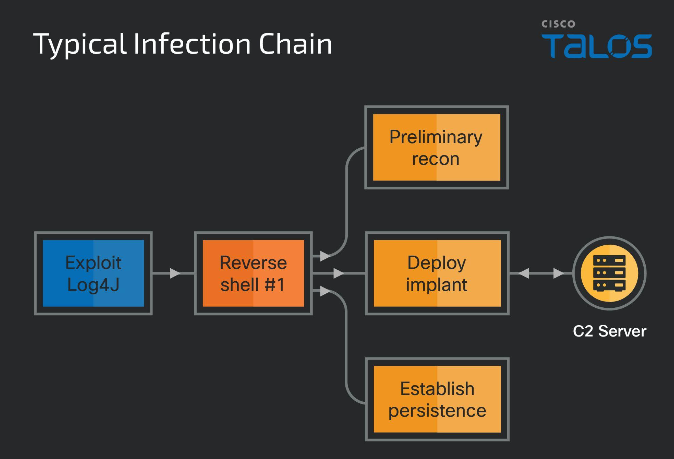
This latest effort, what Talos calls Operation Blacksmith, makes use of the Log4Shell vulnerabilities in VMWare Horizon servers for initially accessing victims’ computers. These exploits began two years ago. Veracode last week posted an analysis showing that more than a third of the servers are running applications that are still vulnerable, which is why Lazarus and others continue to take advantage of them.
This time around, Lazarus is responsible for a new campaign, whose infection chain is shown at top, that uses Telegram bots and other channels as its command-and-communications mechanism. Telegram is also used for file transfers. This makes it harder to track, given that these tasks appear as ordinary users’ traffic.
Once this malware has entered a network, the hackers deploy a reverse proxy to access their targets directly and deploy other tools that the Talos researchers analyze in detail. What this shows is that Lazarus is very much a work in progress, and using innovative mechanisms to find their way into its targets.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.