 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Any chief information officer who assembled a portfolio of 130 discrete products to address a single problem would probably be accused of mismanagement. But when the problem is cybersecurity, they’re more likely to be seen as prudent.
That’s the number of products the average enterprise has assembled to protect its infrastructure, applications and data, according to Palo Alto Networks Inc. Other estimates place the number at between 70 and 90. Either way, the cybersecurity product sprawl is out of control, and research indicates that the situation will only worsen.
A survey by Aptiviti Inc.’s Enterprise Technology Research arm reported that 51% of respondents expect to increase the number of providers in their security stack over the next 12 months, while only 9% expect a decrease. The numbers fly in the face of the conventional wisdom that enterprises are reining in the scope of their security stack in the name of simplification.
“The prevailing sentiment that vendor consolidation is the dominant trend in security is not substantiated by this data,” wrote Dave Vellante, chief analyst at theCUBE Research, a SiliconANGLE sister company. “Rather, the opposite appears to be true, and the data indicates a tendency toward adopting new entrants in the market rather than consolidation.”
May’s RSA Conference dramatized the industry’s proclivity to hype standalone solutions at the expense of explaining to buyers how they fit into existing controls, said Olivia Rose, a former chief information security officer and founder of Rose CISO Group LLC and faculty member at the Institute for Applied Network Security. “We’ve moved into the bright, shiny object phase where security is based not on fundamentals but on what’s new,” she said.
How did we get into this mess? Experts cite several reasons.
One is the relative immaturity of the cybersecurity industry, a field that barely existed before the commercial internet emerged in the late 1990s. Even then, it wasn’t until the mid-2000s that businesses began conducting significant commerce and connecting with business partners over public internet connections, inviting the attention of cybercriminals.
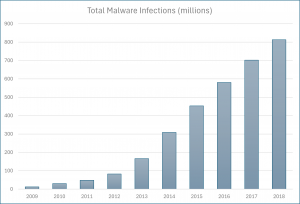
Source: PurpleSec LLC
Another factor is the rapidly changing cyberattack landscape. New threats emerge constantly, leaving CISOs little time to craft overarching strategies. Cloud, mobile and artificial intelligence-fueled attacks are all relatively recent, each demanding different defense strategies. The chaotic nature of the threat surface forces security teams to play constant defense with little chance to come up for air.
“Security teams keep buying new technologies, looking for the silver bullet, almost praying that this will solve their problems,” Rose said. “Many products just sit on the shelf because they don’t integrate well, they overlap, or they’re too labor-intensive to implement.”
That’s a problem Richard Watson, global and Asia-Pacific cybersecurity consulting leader at Ernst & Young Global Ltd., has often seen. “Our statistics say only 10% to 20% of cybersecurity technology is actually used,” he said. “We see CISOs wanting to buy more when not using what they’ve already got.”

CISO Rose: “Security teams keep buying new technologies, looking for the silver bullet.” Photo: Rose CISO Group
Anand Oswal, senior vice president and general manager of network security at Palo Alto Networks, said plugging holes in the dike without adhering to an overarching strategy creates duplication and overlap.
“Technology, communications and the workforce have evolved a lot over the past 20-plus years, from on-campus data centers to cloud-based software and now artificial intelligence,” he said. “To inspect and protect all network traffic, organizations have ended up cobbling together network security tools layered on top of one another.”
That’s precisely the kind of overlap Jack Klecha is trying to avoid. As senior director of enterprise information security at Cisco Systems Inc., Klecha oversees data governance across a sprawling landscape spanning six continents and nearly 100,000 people.
“One of the bigger fallacies of introducing a new tool is that you write a check, and the problem goes away,” he said. “You’re actually bringing in a lot of new issues you have to address. It’s easy to turn something on but not so easy to get the value you need.”
Fragmentation and point solutions lead to underuse. Each new product also requires training and staff to operate, a tall order in a field wrestling with chronic skills shortages.
Piecemeal approaches ultimately create more vulnerabilities, said Taimur Aslam, chief technology officer at Cytex Inc., maker of a unified resilience platform. “The lack of integration often results in siloed data, a higher risk of misconfiguration, inconsistent security policies and increased administrative overhead,” he said. “Adding more tools has exacerbated vulnerabilities rather than alleviated them.”

Cisco’s Klecha: “It’s easy to turn something on but not so easy to get the value you need.” Photo: LinkedIn
Then, there’s the fragmented nature of the cybersecurity market. The IT-Harvest Cybersecurity Dashboard counts more than 3,700 vendors selling more than 8,000 products. Business database Crunchbase lists more than 25,000 firms that include “cybersecurity” in their business descriptions.
Most sell point products that address specific vulnerabilities. Many eye a quick market exit. SecurityWeek counted nearly 1,300 cybersecurity mergers and acquisitions between 2021 and 2023.
“Every year, there is almost a wholesale change in the vendor environment, with a lot of small companies addressing one use case and hoping to be acquired,” Watson said. “I don’t know how any one person can keep up with all that’s happening.”
Many startups focus more on solving point problems than fitting into a broader framework. Data formats and database schemas may be proprietary and incompatible with other tools, leaving integration up to frazzled security teams.

Advanced Cyber Defence’s Wilkes: “Software providers, need to establish some clear standards for interoperability.” Photo: ACDS
“We, as cybersecurity software providers, need to establish some clear standards for interoperability and integration and have some sort of [application program interface] or similar integration as a default offering for customers,” said Elliott Wilkes, chief technology officer at Advanced Cyber Defence Systems Ltd.
He recommends that security teams conduct a portfolio review that includes asking vendors about their integration capabilities and intentions. “This will compel them to provide you with a clearer understanding of which tools are compatible with the rest of your stack,” he said.
It all adds up to a nearly impossible mess for CISOs to manage, which is itself a problem. Chronic turnover in the profession contributes to the lack of long-term planning.
A Proofpoint Inc. survey of 1,600 cyber leaders in 16 countries found that 73% had experienced burnout in the past 12 months. Gartner Inc. last year predicted that nearly half of cybersecurity leaders would change jobs within two years, with about one-quarter leaving the field entirely. “Cybersecurity professionals are facing unsustainable levels of stress,” Deepti Gopal, a Gartner director analyst, said in a press release.
Is there a solution in sight? For CISOs who can find the time to assess their product portfolios and consider a long-term strategy, experts say there are tried-and-true approaches to bringing order from chaos.
It’s best to start with a disciplined portfolio analysis, they say. “Understand what products do, who the internal owners are and what processes the tools rely on,” said Kurt Manske, information assurance and cybersecurity leader at Cherry Bekaert LLP, an advisory and accounting firm.
Maintaining an inventory of information technology assets is a basic requirement of regulations like the Payment Card Industry Data Security Standard, the American Institute of Certified Public Accountants’ System and Organization Controls and the International Organization for Standardization’s ISO 27001 standard, “but many don’t have a full inventory of their assets,” Manske said.
A portfolio analysis should be conducted in the context of risk management, a disciplined process of identifying, assessing and prioritizing risks that guides coordinated efforts to limit the impact of adverse events. This is different from many organizations’ approach, which is to battle classes of threats.
“A risk-based approach looks at where you are most vulnerable across the complete threat surface rather than the risk of a network breach or data loss,” said Cytex’s Aslam.

Ernst & Young’s Watson: “Only 10% to 20% of cybersecurity technology is actually used,” Photo: EY
Cisco prioritizes security investments based on risk and uses guides like ISO 27001, the National Institute of Standards and Technology’s Cybersecurity Framework and the open-source Common Controls framework to stay current with industry-accepted best practices, standards, regulations and certifications.
Cisco’s Klecha advised taking a hard look at in-house capabilities and maximize their use. That reduces the need for new tooling and the accompanying complexity.
“Part of what I’m pushing is to maximize the features we already own,” he said. “When we encounter a new issue, we look to see if what we already have on the back of the truck can address it.”
Where product overlap exists, it’s important to evaluate whether the value of each technology merits the investment in licenses and skills. “Is the vendor bringing high-quality data to the equation or just spraying more data that your team has to handle?” Klecha said. “Most enterprises don’t lack data on identity, data flows and access, but it’s typically a lot of manual work and coding.”
Tighten up approvals on purchases to force buyers to make decisions in the context of the broader security framework, advised EY’s Watson. “There is too much reactive, emergency purchasing, often from people in security operations middle management roles who are buying technology without understanding the full landscape,” he said.
At Datatribe Foundry LLC, an incubator for cybersecurity startups, Chief Innovation Officer Leo Scott advises building an operational security stack based on four pillars he calls posture, collection, analysis and response.

Datatribe’s Scott recommends building a security stack security stack around posture, collection, analysis and response. Photo: LinkedIn
“Posture is identifying what you have that needs protection and understanding how it’s configured,” he said in written comments. “Collection relates to the things you need to protect. The analysis is detecting and flagging anomalies and patterns in the aggregated data that may indicate security issues and prioritizing the issues. Response takes action to fix problems, ideally before they become major incidents.”
Scott said a comprehensive enterprise cybersecurity stack should include a wide array of services: asset management, network segmentation, identity and access management, mobile device management, endpoint or extended detection and response, cloud security, threat intelligence, incident response, security information and event management, email security, data loss protection, and backup and recovery.
Zero trust, secure access service edge and security service edge, which have emerged in the cloud era to regulate access based on identity rather than devices, “have the potential to reduce reliance on traditional security tools by emphasizing identity-centric security and cloud-native architectures,” said Palo Alto Networks’ Oswal. “These approaches can provide continuous verification and access controls, reducing the need for perimeter-based defenses and enabling more streamlined and adaptive security postures.”
Companies such as CrowdStrike Holdings Inc., Palo Alto Networks and Zscaler Inc. are advocating a more radical approach: scrapping point tools altogether in favor of a unified platform.

WatchGuard’s Collins: “It’s much simpler to train on a single, unified system than many disparate systems.” Photo: LinkedIn
The argument is that consolidation “allows for unified management and operations, so you can write policy from one place and enforce it everywhere, consistently, through quick cloud-based deployment,” Oswal said. “It may result in cost savings from a reduction in tools, but its true value is delivering better and consistent security outcomes.”
WatchGuard Technologies Inc. Network Security Engineer Trevor Collins noted that unified platforms can help alleviate the skills crisis. “It’s much simpler to train on a single, unified system than many disparate systems,” he said.
However, as appealing as those arguments may be, Enterprise Technology Research found little enthusiasm for the concept among security buyers.
“The emerging view seems to suggest that although ‘good enough’ might work in certain areas, in the domain of security, the stakes are too high to settle for anything less than best-of-breed, underscoring the enduring importance of a layered defense strategy,” Vellante wrote.
Sensing an opportunity, some startups are offering to help enterprise security executives rationalize their spending. Two-year-old Balance Theory Inc. tracks over 3,500 security vendors and 10,000 security products to help its customers build their security stacks. It also helps with negotiations and procurement. The company says it’s so confident it can help customers optimize their cybersecurity stack that it guarantees they will save more than the cost of its platform.

1Password’s Won: “The industry continues to build security solutions for systems rather than people.” Photo: LinkedIn
Security vendors can help by making tools more accessible to people outside IT. “We’ll never eliminate this problem as long as the industry continues to build security solutions for systems rather than people,” said Steve Won, chief product officer at 1Password, which is the business name of AgileBits Inc.
His company’s recent research found that 17% of employees admitted to never using work-provided devices, opting instead for personal or public computers. “Work happens everywhere now,” he said.
Multifactor authentication is a basic protection that has finally taken hold with large organizations, 83% of which use it internally, according to JumpCloud Inc. However, small and midsized businesses are far behind, with adoption rates below 35%.
As is often the case in cybersecurity, focusing on the basics yields the best results. “Identify what you have, decide how to protect it, apply protections according to sensitivity, track and monitor for suspicious behavior and have appropriate responses in place,” Rose said. “These are foundational controls that we’re still not doing well after 25 years.”
Humans remain the weakest link in most organizations. Gartner Inc. predicts that “lack of talent or human failure will be responsible for over half of significant cyber incidents” by next year.
AI may be a game-changer, although widespread disagreement exists on whether the technology will be of greater value to the attackers than the defenders. Experts interviewed by SiliconANGLE were mostly hopeful.

Cherry Bekaert’s Manske: “You can expect complexity to increase, not decrease” Photo: Cherry Bekaert
EY’s Watson said that client companies adopting AI for cyber defense had seen more than a 90% improvement in malware detection and 40% better overall productivity in their security operation centers. “Condensing many feeds down into something that can be seen and shared is highly automatable now,” he said.
Cisco’s Klecha sees the potential for AI to make sense of the gusher of data generated by various defense and observability tools. “Being able to build a view of your environment quickly is where AI will shine,” he said.
Cherry Bekaert’s Manske agreed. “When properly deployed, AI allows cyber teams to move from traditionally resource-intensive tasks like correlation to focus on business outcomes,” he said.
“Generative AI has massive promise to help with automated remediation,” asserted DataTribe’s Scott. “It can be significantly more flexible than playbooks in remediating a wide variety of issues.”
But there is little likelihood that AI or anything else will simplify the cybersecurity landscape. With technology innovation accelerating in the ChatGPT age, it seems likely that threats will surge along with it.
As a rule of thumb, Manske said, “You can expect complexity to increase, not decrease.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.