 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Automation generally, and artificial intelligence specifically, render today’s cybersecurity stacks ineffective.
Previously, stopping 99% of attacks and leaving the 1% for armed human hunters to deal with was, if not ideal, at least feasible. With AI, that all goes away because adversaries can scale up phishing and other attacks at unprecedented rates, which overwhelms the ability of humans. This creates a wider gap between exfiltration times, which are shrinking, and mean time to remediation, giving even greater advantage to attackers. As such, the only way to fight AI is with AI.
Moreover, the ever-expanding number of tools in an organization’s security stack continues to exacerbate the problem. According to Palo Alto Networks Inc., the answer is a complete makeover of the cybersecurity stack where consolidating multiple tools into a single platform and gaining comprehensive access to the right data, simplifies security operations and enables AI to operate in real time.
In this Breaking Analysis, we collaborate with Zeus Kerravala and share insights from this past week’s Palo Alto Networks Ignite conference in New York City. We’ll share what we heard from key executives, including an intimate analyst roundtable with Chief Executive Nikesh Arora. And we’ll test the premise put forth by Palo that platformization is the answer to your security challenges.
Our research indicates that the information technology spending landscape remains in flux, driven by shifting economic conditions, policy uncertainty, and ongoing fallout from government tariffs. Recent data from Enterprise Technology Research underscores these dynamics. In the wake of COVID, annual IT spending expectations exceeded 7%.
However, as interest rates tightened, those forecasts plummeted below 3% before rebounding to 3.4% toward the end of 2023. Expectations for 2024 have fluctuated considerably — initially settling at 3.9% and then rising to 5.3% in January, only to moderate again in April, based on preliminary ETR data, to roughly the mid-3% range, pending final survey results (see below).
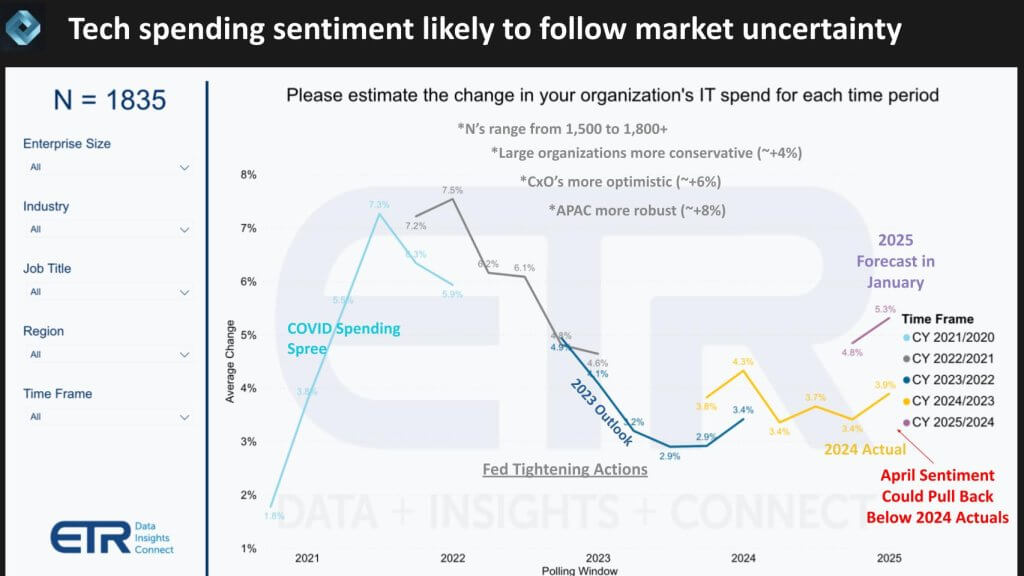
We believe the volatility in global trade policies and supply chains continues to dampen purchasing confidence. Higher tariffs mean organizations must pass added costs down the value chain, creating an inflationary cycle that complicates technology procurement. Certain industry executives have highlighted attempts to mitigate these pressures by diversifying supply sources — yet these diversification strategies sometimes require further diversification of their own, underscoring the complexity of maintaining stable input costs.
The question arises: Is cybersecurity investment insulated from this macro volatility? Historically, cybersecurity has proven more resilient than other IT segments because of its essential role in safeguarding critical data. With trends such as cloud expansion, hybrid work and the rapid rise of AI, companies are proliferating sensitive data across a broader surface area, creating new vulnerabilities that require ongoing protection. While we believe that continued innovation and necessity may spare cyber from the worst effects of tightening budgets, it is not entirely immune. Even security spending can come under scrutiny when macro pressures and policy-induced uncertainties persist.
In our view, the next few quarters will prove pivotal. As organizations navigate tariff complexities, supply chain realignments, and shifting economic signals, we expect cybersecurity to remain a priority — but watch carefully for more selective spending patterns that favor tools delivering clear, quantifiable risk reduction. Ultimately, while the broader market adjusts to evolving economic and policy realities, our data suggests that security’s strategic importance keeps it near the top of IT leaders’ agendas — even if overall budget growth undergoes further revisions.
A review of recent cyber stock performance provides a useful lens into market sentiment around security investments. Over the past six months, leading cybersecurity names have generally outperformed broader market indices, even in the face of tariff tensions and other macro uncertainties. A basket of cybersecurity equities, represented by the BUG ETF, has beaten the Nasdaq Composite in this timeframe. Within this group, however, Palo Alto Networks has underperformed top peers thanks to concerns over competitive pressures, annual recurring revenue momentum and investor confidence in Palo’s “platformization” strategy.
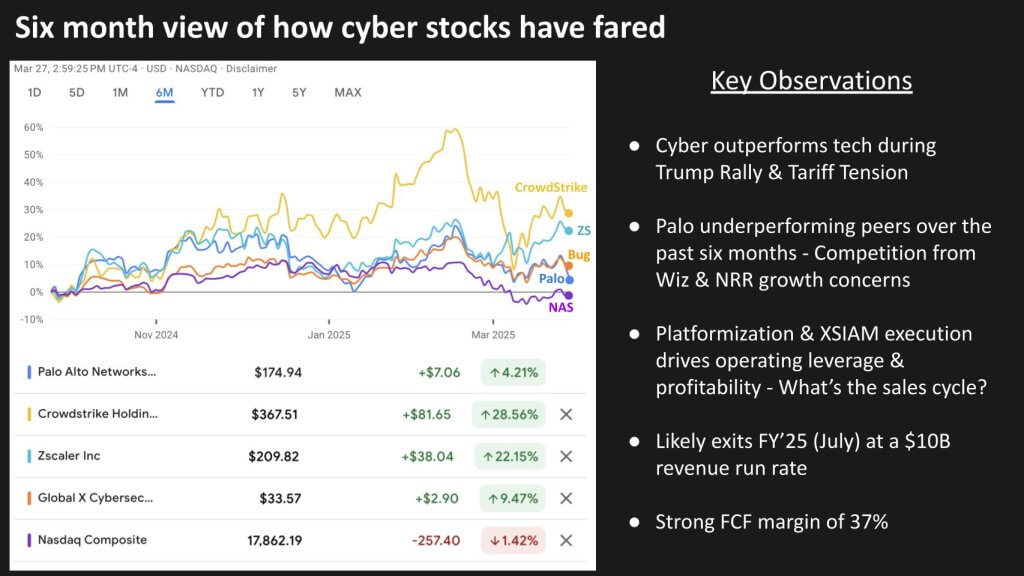
Some organizations are betting on large-scale, integrated security platforms to streamline the management of numerous cybersecurity tools, which often total dozens or more within a single enterprise. We believe platformization holds promise for reducing complexity and improving operational efficiency — particularly for companies seeking to unify threat data across endpoints, networks and cloud workloads. At the same time, this path is not without challenges. The migration from a sprawling multivendor environment to a cohesive platform can lengthen sales cycles and raise questions about how to retire incumbent point products.
Moreover, there is an inherent tension in claiming to be both “best-of-breed everywhere” and a single-platform provider. Our data suggests that no one vendor can excel in every sub-discipline of security — especially when new domains such as zero trust network access or ZTNA, secure access service edge SASE, or application programming interface security emerge rapidly. In our opinion, enterprises are more likely to adopt a hybrid approach, embracing platform consolidation where it makes sense while augmenting with specialized solutions that address evolving threats and plug holes better then broad platforms.
Nevertheless, many executives within top security firms, emphasized by Palo Alto Networks at Ignite NYC, are declaring a new era in which cybersecurity becomes an “AI play” rather than a collection of siloed tools. As security threats evolve, the thinking goes, those vendors with robust AI-driven capabilities to correlate massive data sets will gain a decisive advantage. We believe this shift is underway but may take years to mature fully.
In the near term, we see cybersecurity investments continuing at a steady pace, with leading providers that can demonstrate clear AI-driven outcomes standing out. Though best-of-breed innovation shows no sign of disappearing entirely, platform leaders that deliver meaningful integration and automation are well-positioned to capture share and drive recurring revenue.
As always, macro factors such as tariffs, global policy shifts and overall IT spending sentiment will influence the sector’s trajectory. However, based on our research, cybersecurity remains among the more resilient areas of enterprise tech investment, buoyed by an ongoing wave of emerging threats and a growing appetite for AI-fueled defenses.
Despite vocal vendor marketing around consolidation, the cybersecurity landscape remains exceedingly crowded, with new entrants frequently emerging to address specialized threats. To illustrate this point, we often cite the chart shown below from ETR’s quarterly Technology Spending Intentions Survey (TSIS) survey, which contains preliminary data from more than 1,600 respondents. It highlights how organizations are allocating security budgets across various vendors and underscores just how many options exist for enterprises today.
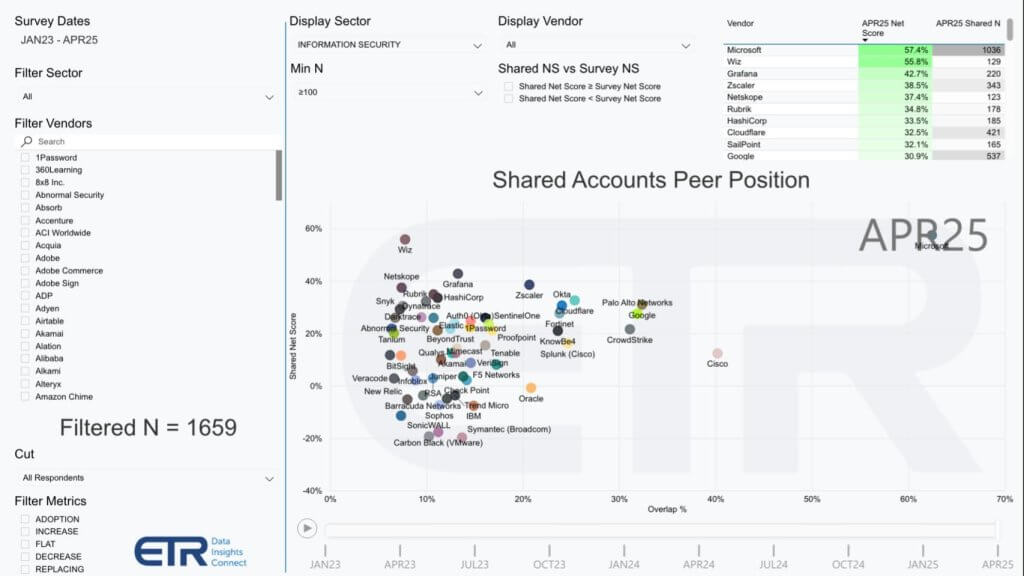
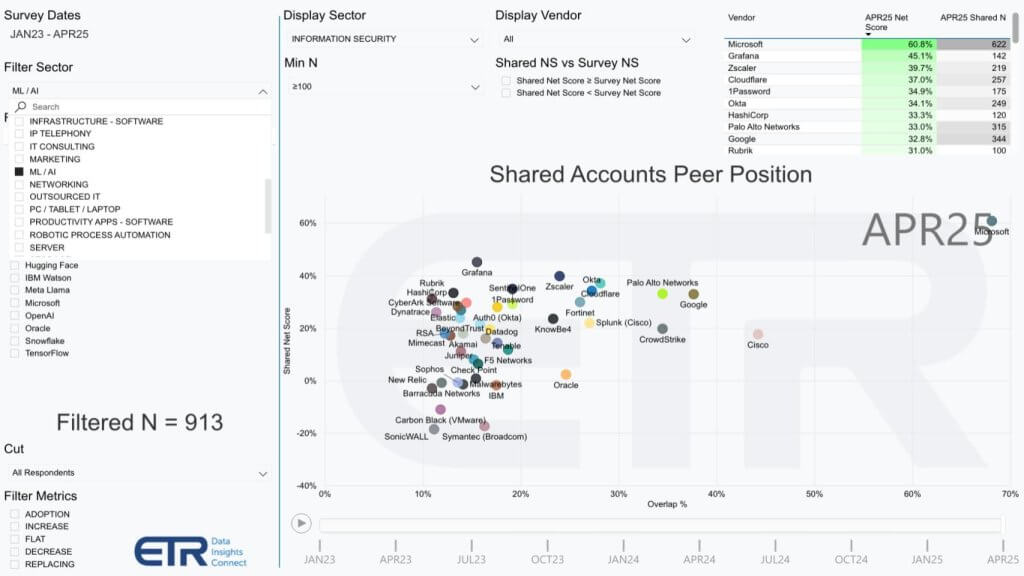
What we show below is the same XY graphic but we filtered the data on those accounts heavily investing in AI. If the premise is AI companies are the ones that will succeed in cyber, we wanted to see how “turning on” ML/AI in the ETR data impacted spending profiles.
AI’s growing influence on cyber: The Google-Palo Alto dynamic
If artificial intelligence is becoming a central focus in the cybersecurity sector, how will it reshape competitive alignments and fuel M&A activity. A fresh view of ETR’s preliminary data from over 900 survey respondents specifically filtered for organizations making sizable investments in machine learning reveals notable shifts as shown below. When isolating on “AI-centric” accounts, both Google and Palo Alto show improved positions relative to the broader enterprise sample, with Palo Alto’s net score rising into the mid-30% range — an increase from its sub-30% placement in the unfiltered data. As well, Google’s penetration increases relative to Palo’s when compared with the previous chart.
We believe the cybersecurity sector is on the cusp of an AI-driven evolution, where success hinges on building robust data pipelines, delivering seamless product integrations, and correlating threats at machine speed. Though these developments open the door for established cloud giants to disrupt the status quo, the final winners will be those who can rapidly demonstrate tangible, AI-based threat detection and response outcomes at scale. Ultimately, the marketplace — already crowded — is poised to get even more competitive as vendors race to embed advanced AI solutions and differentiate on their ability to manage risk in an increasingly complex digital landscape.
We believe the market will remain fluid as organizations weigh one-stop-shop platform strategies against adopting specialized point tools for targeted needs. In our opinion, vendors that demonstrate consistent, high net scores will be those that can not only provide best-of-breed innovations but also integrate seamlessly with existing ecosystems. Ongoing developments in AI and automation are poised to shape these dynamics further.
Our research suggests that the cybersecurity sector is still experiencing robust investment levels. However, continuous market shifts — such as macroeconomic changes, tariff uncertainties, and evolving threat vectors — could alter spending patterns. Despite these challenges, the data indicates that security budgets remain among the most stable in enterprise IT, as organizations race to keep pace with an expanding threat landscape and an accelerating wave of digital transformation.
Below is a list of key topics that came out of Ignite and the an intimate round table with Arora that we’ll review in this next section.

Our research indicates that Palo Alto continues to face formidable competition from various quarters in the cybersecurity market. Vendors spanning legacy network stalwarts, emergent AI-driven security firms, and best-of-breed specialists each pose different challenges. We believe this competitive backdrop sets the stage for a bigger debate: can a single, integrated platform truly replace multiple, standalone security tools?
Taking Microsoft out of the ETR data and isolating on a few key Palo competitors shows a somewhat clearer picture as shown below.
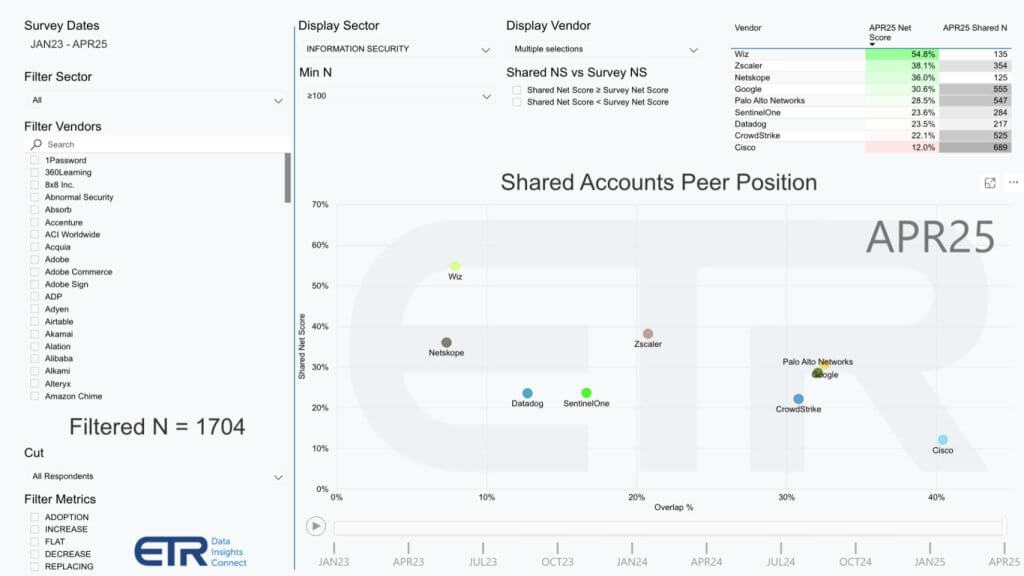
Palo Alto’s strategy hinges on the premise that a unified security platform — covering everything from network firewalls to advanced cloud security tools — will ultimately outcompete a patchwork of point solutions. The argument is that integrating threat intelligence, AI and data ingestion into a single solution can reduce costs, curb complexity and yield better security outcomes.
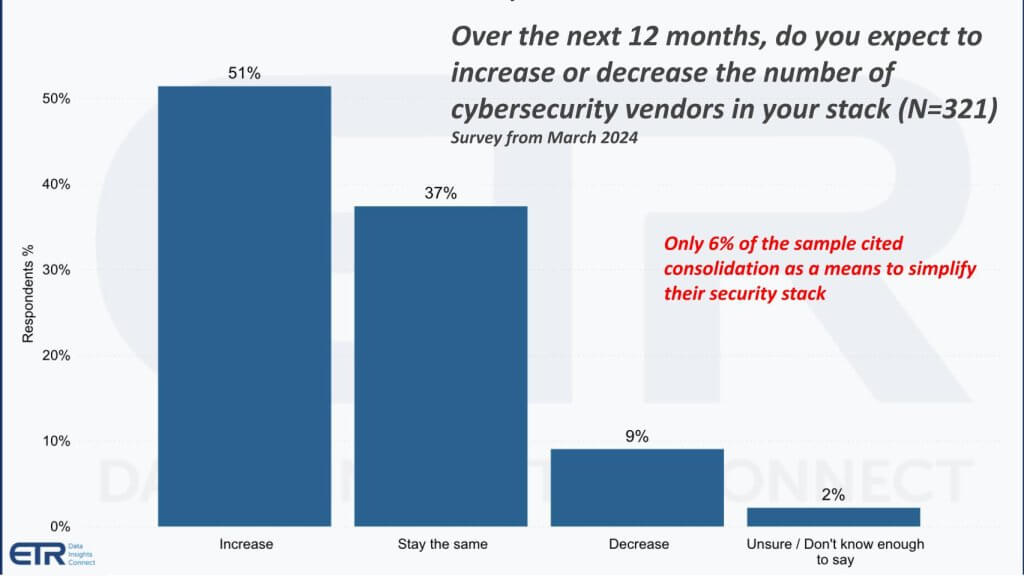
However, as shown below, survey data from ETR shows a majority of organizations plan to add, not reduce, the number of security vendors in their environment. In our opinion, this reflects the unrelenting emergence of new threats and new tools, making many buyers hesitant to put all their eggs in one platform basket. That said, the upside for a fully realized platform approach could be enormous if adoption accelerates, as even a small share shift can translate to billions in incremental spending. Note: ETR will be updating this survey prior to this year’s RSA Conference.
One of Palo Alto’s central claims is that consolidating security data onto a single platform avoids redundant ingestion costs. The organization emphasizes that ingesting data multiple times — across numerous standalone tools — becomes prohibitively expensive. Instead, Palo Alto proposes ingesting data once, applying AI-based analytics, and then making those insights available across all security domains. While this is as strong argument, as shown in the previous slide, the market dynamics create friction to the strategy.
Nonetheless, we see AI as the defining catalyst of future cyber competition and Palo is an engineering-focused company with a commitment to R&D and M&A. Attackers are applying advanced machine learning to breach systems and defenders must do likewise to keep pace. Large, diversified providers stand out here, as they can feed enormous data sets into AI engines to detect advanced threats more quickly. Still, the question remains whether a single vendor can master every aspect of security — endpoint, identity, cloud posture and beyond — at the highest level of precision.
Conversation around secure browsers indicates this may be another wave of innovation to watch. Our research suggests that earlier browser-isolation approaches created poor user experiences. New entrants, however, like Island, are leveraging AI to detect phishing and other threats in real time without disrupting workflow. Meanwhile, posture management has quickly morphed into multiple categories — cloud posture, identity posture, data posture. Many analysts predict that these sub-markets will eventually consolidate, but how quickly remains unclear. Practitioners still see distinct posture tools as necessary for new and evolving threat vectors.
Though quantum computing could one day break today’s encryption standards, executives such as Arora point out that current cyber defenses are already challenged by non-quantum threats. In our opinion, quantum is a long-term concern; many security leaders are instead focusing on near-term issues like supply chain risks, AI-driven hacking and compliance with shifting regulatory landscapes.
The implication is that today anyway, adversaries don’t need quantum to wreak havoc; they can do just fine with existing tools.
Palo Alto is widely credited for expanding its share in a massive security market. Under Arora’s leadership, the company has expanded its share of a $100 billion market from around 1% and is headed toward 10% share. It hopes to continue growing its proportion of the overall pie, citing aspirations for a deep double-digit percentage share (Arora often cites 40%) that would make it a “de facto standard.”
Our view is that achieving even 15% would validate Palo’s consolidation strategy. However this leap will require continued strong execution — particularly around AI innovations, seamless integrations among its product lines, and an efficient go-to-market strategy.
Competitors such as CrowdStrike and Zscaler will rely more on ecosystem approaches and partnerships to affect their own versions of consolidation/platformization.
We believe Palo Alto’s focus on platformization and AI-driven integration is bold and well-suited to the company’s scale. The approach promises simplicity, data efficiency and reduced latency in threat detection, potentially generating material returns for both customers and investors. At the same time, the momentum behind best-of-breed solutions remains strong. Large enterprises often gravitate to specialized tools — especially when those tools demonstrate superior performance in targeted domains.
The next few years will test whether platformization can reach critical mass. Those providers that successfully unify diverse security functions, harness advanced AI, and execute well will be poised to seize market share. Yet high-velocity innovation, continuous vendor arrivals and the entrenched habits of security practitioners mean the market’s evolution remains unpredictable. In our view, it’s this tension between innovation and inertia, between platform advocates and best-of-breed believers, that defines the cybersecurity story today.
The reality is that both scenarios can be true. Palo, for example, could double its market share within the next four to five years, which in our view would validate its platform strategy. At the same time, it’s likely that more point solutions will come to market and do a better job filling certain gaps than will a single platform.
What do you think? Are you able to consolidate your security stack and reduce the number of vendors you’re managing? How do you see AI fitting into the future of cyber? Is it a “do-over” as we and others have posited? Or will it be an iterative evolution? And in your view, is security solvable?
As always, we appreciate the feedback. Let us know what you think and thanks for reading.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.