 NEWS
NEWS
 NEWS
NEWS
 NEWS
NEWS
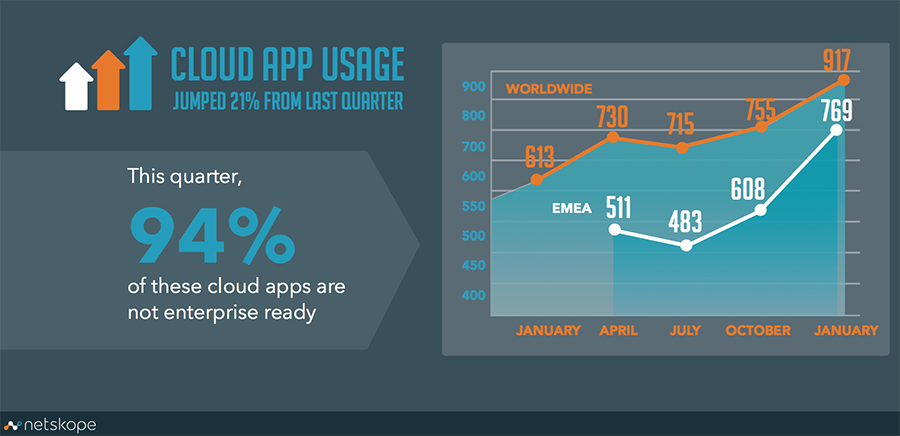
Enterprises use more cloud-based apps than ever. Over the past three months, the average number used jumped to 917 from 755, with Microsoft Office 365 apps moving past Google to take the second and third spots in Netskope Inc.’s new Cloud Report.
Microsoft Office 365 Outlook.com ranks second, and Microsoft Office 365 OneDrive for Business ranks third. While Google’s Gmail ranks fifth, and Google Drive sits in sixth position.
While those apps improve productivity by enabling users to sync and share documents, they also have the potential to introduce malware and cause sensitive data to be leaked. Even cloud-based apps that are considered enterprise-ready, including Microsoft Office 365 apps, can be vulnerable, said Sanjay Beri, co-founder and CEO of Netskope.
That’s because user activity, as well as applications that move data in an out of the suite, can create risk.
“Security isn’t just about the inherent security of the app. It’s about what users are doing in the app,” he said. “We call this a ‘shared responsibility’ model, where the app is responsible for being inherently enterprise-ready and the enterprise is responsible for governing usage and data.”
A user may upload sensitive data to the cloud that is supposed to stay on premises. Data that is supposed to remain in the company’s control might be shared or sent to people. And data that is supposed to remain in the cloud can be downloaded by an unauthorized user or to a personal device.
Enterprises may also run sanctioned apps that have malware, Beri said. According to the report, 4.1 percent of enterprises run apps that are infected with viruses, worms, Trojans and/or ransomware. Because of the cloud’s many connected endpoints, and users unwittingly spreading the infection through sync, share and collaboration mechanisms, malware can spread exponentially in a short period of time, creating a fan-out effect.
“While the Office 365 apps tend to be enterprise-ready, enterprises can’t always say that for the ecosystem apps that are ‘hanging off’ the suite,” Beri said. “Information security teams need to make sure they enforce their usage and data leakage policies not just in the Office 365 suite, but also of all the other cloud apps that shuttle corporate data in and out of the suite.”
Beri said organizations should take three steps to ensure their applications and data are secure:
“By enforcing policies at the activity level or data level, IT can go from using a sledgehammer approach, using perimeter technologies such as firewalls, to a scalpel approach and carve out risky behavior while still allowing the app to be used,” Beri said.
He also suggested companies coach employees on why certain actions and applications are hazardous. Don’t just block them from doing something.
“Some of our most lean-forward customers accomplish this by coaching users about the use of unsanctioned apps and sanctioned alternatives. Some give users an opportunity to continue with non-compliant behavior by allowing them to enter a justification for the action,” Beri said. “This puts power in the users’ hands, and IT often finds that users make the right choice when presented with the ‘why.’”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.