 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Last summer Capital One Financial Corp. was the victim of a massive data breach encompassing more than 100 million credit card applications and revealing 140,000 Social Security numbers. The cause: a misconfigured web application firewall, which is an appliance or software application that protects applications that run on the web.
The misconfiguration enabled the attacker, a former Amazon Web Services Inc. employee, to launch a server-side request forgery or SSRF, an attack that tricks a server into connecting to a server it wasn’t supposed to connect to.
If those terms sound unfamiliar, it’s because they had barely been heard of a few years ago. They’re a new kind of cybersecurity vulnerability that was born in the cloud.
“SSRF has become the most serious vulnerability facing organizations that use public clouds,” Evan Johnson, a product security manager at Cloudflare Inc., wrote in a detailed description of the breach posted on his personal blog. In an interview with Brian Krebs, Johnson elaborated that the potential damage of SSRF attacks are “being worsened by the offering of public clouds.”
Although the servers and data that were breached were on AWS infrastructure, Capital One assumed full responsibility for the incident. It had to. Under AWS’ Shared Responsibility Model, customers are responsible for configuring their own guest operating systems, databases and applications.
That may surprise some people. Cloud infrastructure providers make their services so simple to set up and administer that it’s tempting to assume that they also protect whatever customers run on them. But in most cases, everything above the infrastructure layer is the customer’s responsibility, including patches, data encryption, access control and malware prevention.
“A huge misconception is that the infrastructure-as-a-service model extends security to the customer’s systems when the providers are only securing the systems they are hosting,” said Jesse Emerson, vice president of Americas managed security services at managed security services firm Trustwave Holdings Inc.
“Simply put, when you use cloud services, the providers are responsible for securing the underlying infrastructure – customers are responsible for securing their data and applications,” said Robert Sadowski, trust and security marketing lead for Google LLC’s Cloud Platform.
And that misperception appears to be widespread. A recent survey of an undisclosed number of information technology and security professionals by Enterprise Management Associates Inc. found that 53% believed IaaS providers are accountable for most or all public cloud security.
The issue isn’t with the cloud itself. Most security professionals now agree that cloud infrastructure is at least as secure as the best enterprise data centers. Instead, the problem is with the free-wheeling and sometimes haphazard ways it’s adopted.
Cloud servers are basically no different than boxes in an on-premises data center. However, the ease with which cloud instances can be provisioned has led many organizations to delegate authority for using them in ways they would never do with their own infrastructure.
Many IT organizations have embraced the cloud as an expedient way to satisfy demands from their developers and end users for faster provisioning and greater control over their applications. Cloud providers have made it easy for people with only modest technical skills to install applications and upload data.
But ease of use can also create a sense of false security. “The objective of making cloud management user-friendly can have unintended side effects, such as making it easier to make serious mistakes — one-click disasters, if you will,” said Kon Leong, chief executive officer of ZL Technologies Inc., a maker of records management and governance software.

ESG’s Cahill: “Line-of-business people are clouding on their own and they may not be clouding properly.” Photo: ESG
“The speed with which organizations are adopting cloud is ahead of their ability to secure that usage,” said Doug Cahill, a senior analyst at The Enterprise Strategy Group Inc. “The security operations team isn’t always involved. You’ve got line-of-business people who are clouding on their own and they may not be clouding properly.”
Ninety percent of the 1,000 respondents to a recent McAfee LLC report, in fact, said they had experienced some security issues with IaaS. “It’s possible the speed of cloud adoption is putting some practitioners behind,” the report stated.
Lack of security procedures or simple carelessness can blindside even the most web-savvy organizations. In September, thieves swiped more than 24 million account records for users of Lumin, a cloud-native PDF reader produced by New Zealand-based Nitrolabs Ltd., after the data was left in the open for months on a public-facing MongoDB database on a cloud server.
Early last year Fedex Corp. was embarrassed when nearly 119,000 documents, many containing highly sensitive customer information, were left unprotected on an Amazon S3 storage instance.
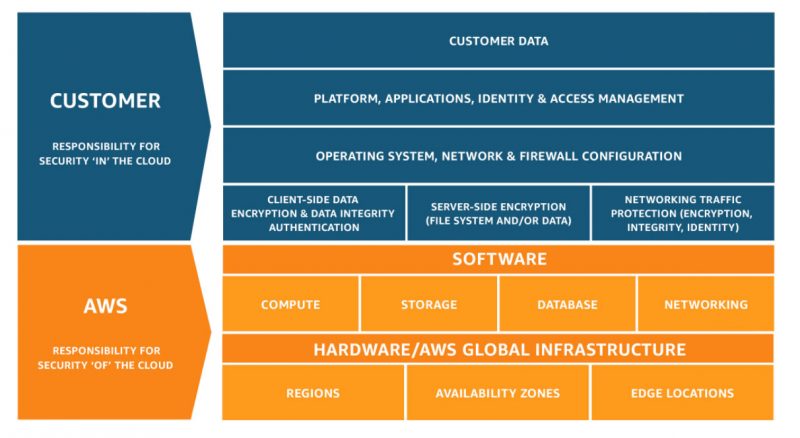
Amazon Web Services’ shared responsibility model defines accountability for both customers and cloud providers. Image: AWS
None of these incidents was the fault of the big cloud providers, all of which offer world-class security controls. However, each defines its offerings a bit differently and many services are extra-cost options. Controls also aren’t necessarily simple to understand. Amazon overhauled security controls on its S3 cloud storage service two years ago after numerous customers accidentally left confidential data publicly exposed because of confusion about nested and overlapping permissions.
Incidents such as these highlight the need for organizations to understand their responsibilities better when using cloud infrastructure and to develop procedures that protect users from themselves. Gartner Inc. estimates that over the next six years, 99% of cloud security failures will be caused by human error and “90% of the organizations that fail to control public cloud use will inappropriately share sensitive data,” wrote Gartner Brand Content Manager Kasey Panetta. “CIOs must change their line of questioning from ‘Is the cloud secure?’ to ‘Am I using the cloud securely?’”
Perceptions about cloud security have shifted markedly in recent years. No long ago, the issue consistently ranked within the top two reservations chief information officers expressed about moving to the cloud, but those fears have largely subsided. A recent study of U.S. and U.K. security professionals by British domain registrar and cybersecurity firm Nominet UK found that 61% say cloud environments are at least as secure as on-premises infrastructure. CIOs recognize that cloud infrastructure providers can commit resources to cybersecurity that dwarf that of all but the largest institutions.
“In general, cloud is more secure than an enterprise data center,” said John Veizades, vice president of engineering and product at Megaport Ltd., a provider of cloud connectivity services. For example, he noted, cloud providers are better able to respond to “zero-day” or heretofore undiscovered threats because they monitor so many attack points. “Cloud vendors are aware of these things much sooner than you are as an IT administrator,” he said.
The quality of cloud security is now so high that it’s easy to become lulled into thinking that the platform provider takes care of everything. But as AWS’ Shared Responsibility Model illustrates, there are clear lines of demarcation.
In an essay about the distinctions between on-premises and cloud security, Red Hat Inc. draws the analogy to an apartment building. Landlords secure the building perimeter but leave the security of individual apartments to their tenants. In a similar way, cloud providers defend the infrastructure that customers rent from them but leave control of the systems software, applications and data to the customer.
The most common cloud security risks are the same as those inside the walls of a company. Cloud can magnify their impact, however. Take password security. Weak passwords have long been one of the most stubbornly difficult problems for enterprises to solve, but when the asset being protected is a cloud administration account, the risk to the business can be severe.
“If I can get into the console, I may have unfettered access to all servers on the account,” Cahill said. “The best practices we use for securing customer-managed environments still apply.” Multifactor authentication is a relatively simple remedy that all cloud providers offer, but none imposes it by default.
An even bigger problem in recent years has been misconfigured cloud services like the one that was at the root of the Capital One breach.
The volume of cloud security incidents attributed to misconfiguration rose 20% in 2018, making misconfiguration “the single-biggest risk to cloud security, with 62% of surveyed IT and security professionals noting it as a problem,” said IBM Corp.’s 2019 X-Force Threat Intelligence Report.
Risk Based Security Inc.’s 2019 mid-year report documented 149 incidents in which misconfigured cloud databases and services collectively exposed over 3.2 billion records, up 54% from the previous year.
McAfee’s survey found that users identify, on average, 37 misconfiguration incidents per month. But researchers also estimated that about 99% of misconfigurations go unnoticed. “Our real-world data shows that companies actually experience closer to 3,500 such incidents” per month, they wrote.
Cloud providers are aware of the risks and responding. “We encourage customers to turn on additional layers of protection from across our threat protection stack, not just address misconfigurations we help identify through Azure security services,” said Scott Woodgate, senior director of Microsoft Azure.
The “sheer complexities of navigating cloud infrastructure” can lead to configuration errors, said Trustwave’s Emerson. “Seemingly minute mistakes can easily lead to a catastrophic compromise if they aren’t caught.”
Software developers have embraced the cloud with fervor because of the speed with which they can spin up servers that match the target destinations for their applications. And many IT organizations oblige by giving their development teams the means to provision their own cloud infrastructure. The increasingly popular agile programming technique called DevOps encourages this by giving developers control of both the application and the environments they run upon. DevOps also promotes continuous integration and delivery or CI/CD, with changes pushed daily or even more frequently.

BMC’s Srinivasan: “Automation is not a luxury, but a necessity.” Photo: Twitter
Developers aren’t known for their attention to security, however. “With each update comes the risk of a single mistake, misconfiguring a cloud IaaS or platform-as-a-service resource and rendering it vulnerable,” said Vidhya Srinivasan, vice president of marketing, digital service and operations management at BMC Software Inc.
ESG’s Cahill was even more blunt. “To the security team, DevOps is like running with scissors,” he said. “There’s a huge cultural dynamic. Development teams are empowered to get applications built quickly and they fear the security team will slow them down.” A variation of DevOps called DevSecOps bundles security into the development process and is a good discipline for enterprises to adopt, experts recommend.
Some of the most notorious cloud breaches have been the result of sensitive data being left in the open on cloud servers. Human error is again to blame. Amazon’s S3 storage is configured to notify users when data is exposed on the public internet but people sometimes either don’t understand the warnings or ignore them, said Leigh-Anne Galloway, cybersecurity resilience lead at PT Global Solutions Ltd., which does business as Positive Technologies. “The default stores are created with a secure configuration, so all leaks are associated with user actions,” she said.
Cloud service providers aren’t entirely blameless. The frequency with which they roll out new services can be dizzying for administrators who are accustomed to the relatively static nature of their own environments. The EMA study reported that 73% of enterprise security teams said lack of visibility within cloud infrastructure limits their effectiveness.
“Cloud service providers are constantly releasing new services, and while they may be similar, they are not identical,” said Srinivasan. “Each instance must be configured appropriately.”
Many of those new services are meant to strengthen security. At Microsoft Corp.’s Ignite conference this past week, for example, the company introduced a broad range of new and enhanced services addressing everything from authentication to insider risk management. Amazon and Google maintain a similar innovation pace.
That can challenge the ability of a security team to keep up. “Manual or ad-hoc security cannot keep pace with a growing or large-scale cloud footprint that is inherently dynamic,” Srinivasan said. “Automation is not a luxury, but a necessity.”
The task gets harder in a multicloud environment, which is fast becoming the norm for organizations that want to pick and choose the best platforms for each workload. Gartner says 81% of public cloud adopters are already working with two or more service providers, but multicloud complexity is a daunting challenge. While the services cloud providers offer are similar, they aren’t identical. Each must be mastered and configured individually.
All those factors don’t add up to a case against using the public cloud. Service providers have made huge strides in hardening their services and their pace of innovation will continue to outstrip that of most of their customers. Microsoft alone employs 3,500 cybersecurity professionals and has invested more than $1 billion in Azure security, Woodgate said.
Cloud security services are typically tightly integrated with the underlying infrastructure, unlike the patchwork of point products that are common in enterprise security operations centers. “Our tools can actually help save employees’ time so they can focus on doing more innovative work instead of plumbing,” said Google’s Sadowski, who claims that cloud security services are far less complicated than people think.
Cloud providers can also apply best practices that may be overlooked in a data center, he added. “For example, we encrypt customer data at rest and in transit to our cloud by default,” Sadowski said. “Data automatically defaults to HTTPS between the customer and Google and we never give any government entity backdoor access.”
Microsoft recently added automatic malware detection that alerts customers if they inadvertently upload malware, Woodgate said. The service encrypts data at rest by default with a Microsoft- or customer-managed key and offers a fully audited troubleshooting process that grants limited access to a support technician to fix a problem. For security professionals, there are machine learning-based filters in Azure Sentinel that cut down on noise and enable them to pinpoint problems more precisely.
“These tools exist; the key is turning them on and using them,” Woodgate said.
Experts say the fundamentals of securing the cloud are the same as securing the data center. Multifactor authentication is mandatory, Woodgate said. “It helps eliminate a lot of vulnerabilities,” he said.
Cloud providers also suggest imposing strict access controls, always encrypting data and knowing what infrastructure the organization controls: Any that uses public cloud should also become familiar with the shared responsibility model. “It’s important to highlight that security in the cloud is a shared responsibility between the customer and their cloud provider,” said Sadowski.
The complexity of administering multicloud and hybrid cloud environments raises the bar on asset management, said BMC’s Srinivasan. “It is mandatory to know what hardware, services and applications you have, where they are running and how they are configured,” she said. “Having an automated way to map and catalog systems, services and relationships is now crucial.”
All major cloud providers offer security hubs that provide comprehensive views of a customer’s services, but they’re only useful for instances the customer knows about. All services should be provisioned under the watchful eye of the IT department.
ESG’s Cahill recommends adopting the practice of “least privilege access,” which restricts access rights to only those resources a user absolutely needs. Network segmentation, which is commonly used on-premises to split networks into multiple subnetworks for performance and security purposes, can be applied at a finer-grained level in the cloud, said Megaport’s Veizades.
“You can think of a network as supporting one application whereas in a data center is supports many applications,” he said. “You can now think about micro-segmentation of network access.”
Automating asset discovery using automated tools from cloud providers is also important because the process is impractical to manage manually, Srinivasan said. “Integrating an automated cloud security process with the service desk for closed-loop change management is also critically important,” she said. “This provides documentation and an audit trail of security problems found and changes made.”
Organizations should make regular scanning and continuous monitoring of all databases routine as well, taking advantage of the rich logging and event management tools cloud providers offer, said Trustwave’s Emerson. “If a vulnerability is caught early, it can be stopped from evolving into a major security incident,” he said.
But even the most meticulous precautions are no match for a careless or poorly trained user. For all the firepower cloud giants have brought to protecting their customers, the greatest threat is at the keyboard.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.