 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Chief information security officers cite trust as the most important value attribute they can deliver to their organizations. And when it comes to security, identity is the new attack surface.
As such, identity and access management continue to be the top priority among technology decision-makers. It also happens to be one of the most challenging and complicated areas of the cybersecurity landscape. Okta Inc., a leader in the identity segment, has announced its intent to converge privilege access and identity governance in an effort to simplify the landscape and reimagine identity.
Our research shows that interest in this type of consolidation is high, but organizations believe technical debt, compatibility issues, expense and lack of talent are barriers to reaching cybersecurity nirvana with their evolving zero trust networks.
In this Breaking Analysis, we explore the complex and evolving world of identity access and privileged account management, with an assessment of Okta’s market expansion aspirations and fresh data from Enterprise Technology Research and input from ETR’s Erik Bradley.
The pandemic accelerated digital transformation and digital raises the stakes in cybersecurity. We’ve covered this extensively, but today we’re going to drill into identity, which is one of the hardest nuts to crack in security. If hackers can steal someone’s identity, they can penetrate networks. If that someone has privileged access to databases, financial information, HR systems, transaction systems, the backup corpus …well, you get the point.

There are many bespoke tools to support a comprehensive identity access management and privileged access system. Single-sign-on, identity aggregation, deduplication of identities, identity creation, governance and group management, to name several. Many of these tools are open source. So you have lots of vendors, lots of different systems and often many dashboards to scan.
Practitioners tell us that it’s the “paper cuts” that kill them — meaning small things such as patches that aren’t applied, open ports or orphaned profiles that aren’t disabled. They’d love to have a single dashboard, but it’s often not practical for large organizations because of the sprawling nature of the tooling and the skills to manage them.
Adding to the complexity, many organizations have different identity systems for privileged accounts, the general employee population and customer identity. For example, around 50% of ETR respondents in a recent survey use different systems for workforce identity and consumer identity.
This is often done because consumer identity is a totally different journey: The consumer is out in the wild and takes an unknown, nonlinear path… and then enters the known inside a brand’s domain. The employee identity journey is known throughout, from onboarding to increasing responsibilities and access to offboarding. Privilege access may have different attributes, such as no email or no shared credentials. And we haven’t even touched on the other identity consumers in the ecosystem, such as selling partners, suppliers and machines.
Like I said: It’s complicated. And meeting the needs of auditors is stressful and expensive for CISOs — open chest wounds such as sloppy histories of privileged access approvals, obvious role conflicts, missing data, inconsistent application of policy… and the list goes on. The expense of securing digital operations goes well beyond the software and hardware acquisition costs.
So there’s a real need and often desire to converge these systems, but technical debt makes it difficult. Companies have spent a lot of time, effort and money on their identity systems and they can’t justify rip-and-replace. So they often build by integrating piece parts or they add on to their quasi-integrated, monolithic system.
And then there’s the concept of zero trust. It means different things to different people, but folks are are asking: If I have zero trust, does it eliminate the need for identity? And what does that mean for my architecture going forward?
Below is an XY graph that shows Net Score or spending momentum on the vertical axis and Market Share or presence in the ETR data set on the horizontal axis. Note the chart insert, which shows the actual data for Net Score and Shared N, which in turn informs the position of the plot.
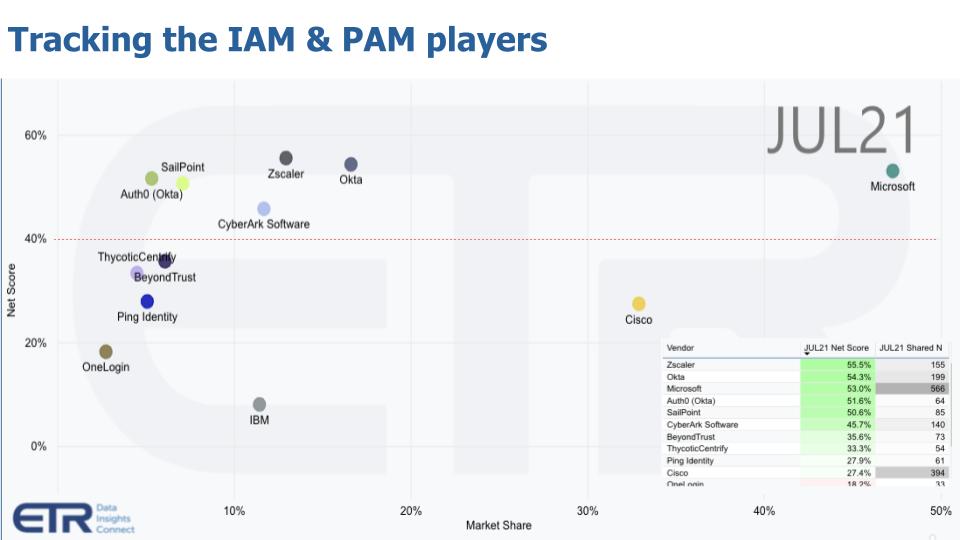
The red dotted line indicates an elevated level. Anything over that 40% mark we consider the strongest spending velocity. In this subset of vendors, chosen to represent identity, you can see six are above that 40% mark, including Zscaler Inc., which tops the charts. Okta has been at or near the top for several quarters. Note: There’s an argument to be made that Okta and Zscaler are on a collision course as Okta expands its total addressable market, but let’s just park that thought for a moment.
You see Microsoft Corp. with a highly elevated spending score and a massive presence on the horizontal axis as well; CyberArk Software Ltd.; SailPoint Technologies Holdings Inc., which Okta is now aiming to disrupt; and Auth0 Inc., which Okta officially acquired in May of this year — more on that later.
Below that 40% mark you can see Cisco Systems Inc., which has largely acquired companies in order to build its security portfolio – for example Duo, which focuses on access and multifactor authentication. Now a word of clarification: Cisco and Microsoft in particular are overstated on the horizontal axis because this includes their entire portfolio of security products, whereas the others are more closely aligned as pure plays in identity and privileged access.
ThycoticCentrify is pretty close to that 40% mark and came about as the result of the two companies merging in April of this year — more evidence of consolidation in this segment. BeyondTrust Corp. is close to the red line as well, which is interesting because this is a company whose roots go back to the VAX/VMS days in the mid 1980s (Google it if you’re under 40 years old) and the company has evolved to provide more modern privileged access management or PAM solutions.
Ping Identity Corp. is also notable in that it emerged after the dotcom bust as an identity solution provider of single-sign-on and multifactor authentication solutions. It went public in the second half of 2019 prior to the pandemic and has a $2 billion market cap, down from its highs of around $3 billion earlier this year and last summer. Like many of the remote-work stocks, it has bounced around as the reopening trade and lofty valuations have weighed on many of these names, including Okta and SailPoint — although CyberArk acted well after its Aug. 12 earnings call as its revenue growth about doubled year-over-year.
So it’s a hot segment, and a big theme this year is around Okta’s acquisition of Auth0 and its announcements at Oktane 2021, where it entered the PAM market and made plain its thrust to converge its platform around PAM and identity governance and administration. We spoke earlier this week with Okta Chief Product OfficerDiya Jolly and will share some of her thoughts later in this article.
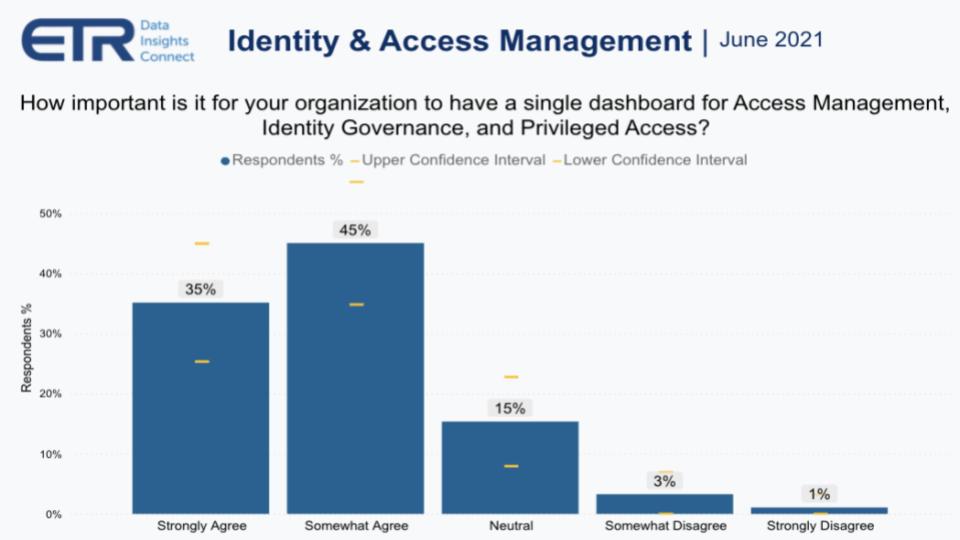
The data below is from a recent ETR drill-down study asking organizations how important it is to have a single dashboard for access management, identity governance and privileged access. This goes directly to Okta’s strategy that it announced in April at its Oktane user conference. Basically 80% of the respondents want this, no surprise.
Staying on this theme of convergence for a moment, ETR asked security pros if they thought convergence between access management and identity governance would occur within the next three years.
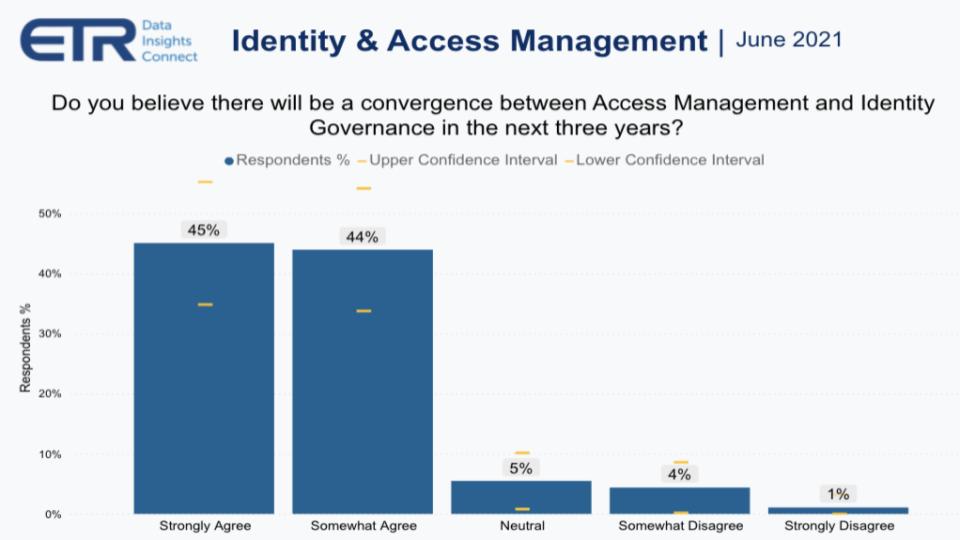
As you can see above, 89% believe this is going to happen – strongly agree or somewhat agree. It’s almost as though the CISOs are willing this to occur. And this seemingly bodes well for Okta. Jolly stressed to us that this move was in response to customer demand and this chart confirms that. But there’s a deeper analysis worth exploring.
The traditional tools of identity, single sign on or SSO and multifactor authentication or MFA are being commoditized. The most obvious example is OAth or Open Authorization – log in with Twitter, Google, LinkedIn, Amazon or Facebook.
Today, Okta has around a $35 billion market cap, off from its highs which were well over $40 billion earlier this year. Okta’s stated total addressable market has been around $55 billion. So Chief Executive Todd McKinnon had to initiate a TAM expansion play, which this move puts in motion. It increases the company’s TAM by $20 billion to $30 billion in our view. Moreover, the top criticism of Okta is “your price is too high” – a good problem to have, we’d say.
Regardless, Okta has to think about adding more value to its customers and prospects and this move both expands its TAM and supports a longer-term vision to enable a secure, user-controlled, ubiquitous digital identity, supporting federated users and data in a centralized system.
The other thing Jolly stressed to us is that Okta is heavily focused on the user experience, making it simple and consumer-grade easy. At Oktane 2021, she gave a keynote laying out the company’s vision and it was a compelling presentation designed to show how complex the problem is and how Okta plans to simplify the experience for end-users, service providers, brands and the technical community, across the entire ecosystem. Essentially it’s aiming to be a one-stop shop for identity.
There are many challenges Okta faces, so let’s dig into that a bit. Zero trust has been the buzzword and it’s a direction the industry is moving toward, although there are skeptics. Zero trust is aspirational today. It essentially says you don’t trust any user or device and the system can ensure the right people or machines have the proper level of access to the resources they need, all the time… with a fantastic user experience.
So you can see why we called this nirvana earlier. In previous Breaking Analysis segments we’ve laid out a map for protecting your digital identity, your passwords, crypto wallets, how to create air gaps – it’s a bloody mess.
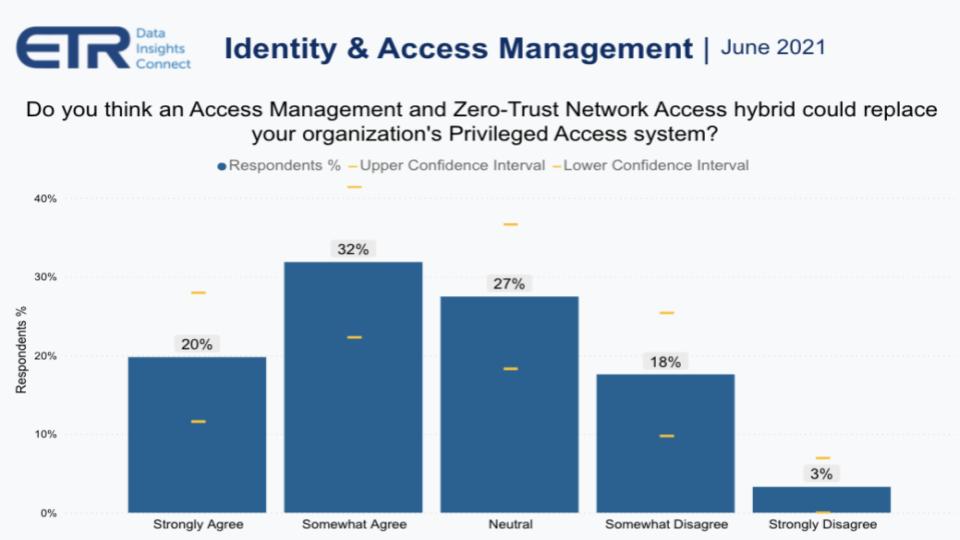
ETR asked security pros, shown in the chart above, if they thought a hybrid of access management and zero trust network could replace their PAM system. Because if you can achieve zero trust in a world with no shared credentials and real time access – a direction which Jolly clearly told us Okta is headed – then in theory you can eliminate the need for privileged access management. Another way of looking at this is that you do for every user what you do for PAM. And that’s how you achieve zero trust.
But you can see from this picture that there’s more uncertainty here, with nearly 50% of the sample not in agreement that this is achievable. Practitioners in Erik Bradley’s roundtables tell us that you’ll still need the PAM system to do things such as session auditing and credential checkouts, but much of the PAM functionality could be handled by zero trust in our view.
ETR then asked the security pros how difficult it would be to replace their PAM systems, and this is where it gets interesting.

You can see by this picture above that the enthusiasm wanes quite a bit when the practitioners consider the challenges of replacing privileged access systems with a new hybrid. Only 20% of the respondents see this as something that is easy to do – likely because they are smaller and don’t have a ton of technical debt.
Below is a chart that shows the blockers. Some 53% say gaps in capabilities, 26% say there’s no clear return on investment – that is, it’s too expensive — and 11% interestingly said they want to stay with best-of-breed solutions, handling much of the integration of bespoke capabilities on their own, presumably. Speaking with Erik Bradley, he shared that there’s concern about rip-and-replace and the ability to justify that internally. There’s also a significant buildup in technical debt.
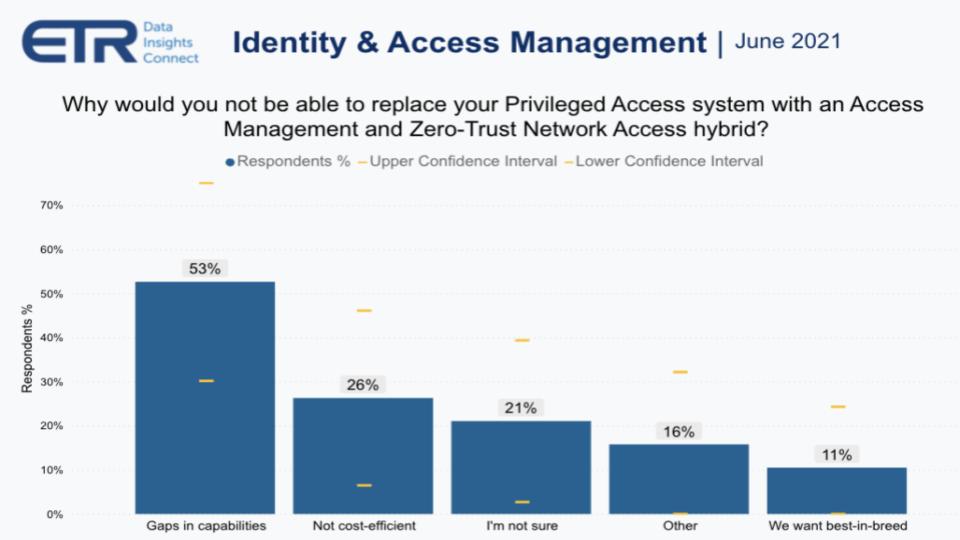
One CISO on an Erik Bradley ETR Insights panel explained that the big challenge Okta will face here is the inertia of entrenched systems from the likes of SailPoint, Thycotic and others. Specifically, these companies have more mature stacks and have built connectors to legacy systems over many years. And processes are wired to these systems and will be very difficult to change.
Another practitioner told us that he went with SailPoint almost exclusively because of its ability to interface with SAP. Further, he said that he believed Okta would be great at connecting to other cloud API-enabled systems, but there’s a large market of legacy systems for which Okta would have to build custom integrations.
Another said it’s not implementing Okta but strongly considered it. The reason the company didn’t go with Okta was that it had a lot of on-premises legacy apps, so it went with Microsoft Identity Manager – but it didn’t meet the grade because the user experience was subpar. So it’s searching again for a solution that can be good at both cloud and on-premises.
A fourth CISO said, “I’ve spent a lot of money writing custom connectors to SailPoint. A lot of money. So who is going to write those custom connectors for me? Will Okta do it for free? I just don’t see that happening.” Further, this individual said, “It’s just not going to be an easy switch… and to be clear, SailPoint is not our PAM solution, that’s why we’re looking at CyberArk.” So the complexity and fragmentation continues and we actually see this as a positive trend for Okta if it can converge these capabilities.
I’ve spent a lot of money writing custom connectors to SailPoint. A lot of money. So who is going to write those custom connectors for me? Will Okta do it for free? I just don’t see that happening… – CISO, large financial services company
We questioned Okta’s Jolly on these challenges and the difficulties of replacing the more mature stacks of competitors. She admitted that this was a real issue but her answer was that Okta is betting on the future of microservices and cloud disruption. Her premise is that Okta’s platform is better-suited for the new application environment and it’s essentially betting on organizations modernizing their application portfolios. Okta believes that will ultimately be a tailwind for the company.
Let’s now look at the age old question of best-of-breed versus incumbent integrated suites.
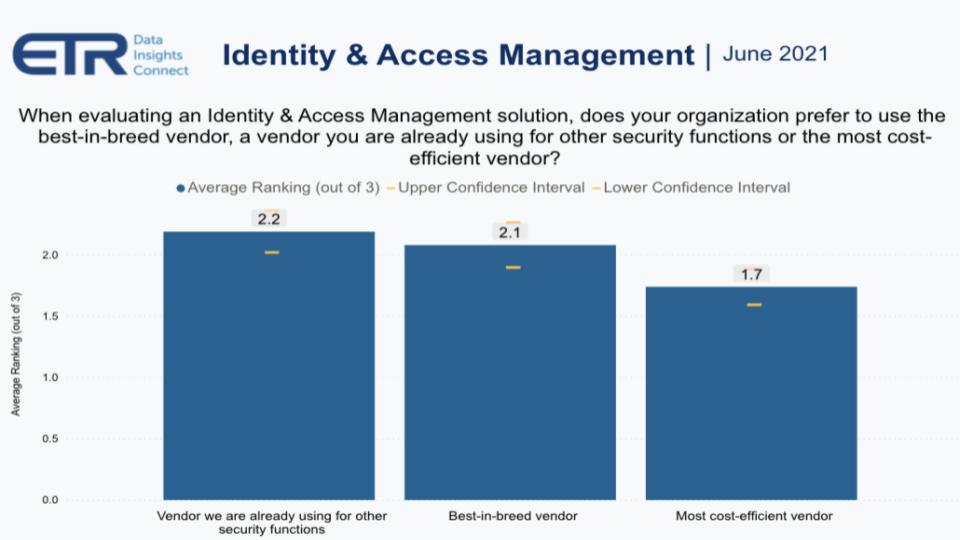
ETR in its drill-down study asked customers, when thinking about identity and access management solutions, do you prefer best-of-breed, an incumbent that you’re already using or the most cost-efficient solution.
The respondents were asked to force rank 1, 2, 3. And you can see above, incumbent just edged out best-in-breed with a 2.2 score versus a 2.1, with the most cost-effective choice at 1.7.
Overall we would say this is good news for Okta. Yes, it faces the big migration issues we brought up earlier, but as digital transformations lead to modernizing much of the application portfolio with containers and microservices layers, Okta will be in a position to pick up much of this business– assuming it stays paranoid and continues to innovate.
And to the point earlier where the CISO told us they’re going to use both SailPoint and CyberArk: When ETR asked practitioners which vendors are in the best position to benefit from the zero trust trend, the answers were, not surprisingly, all over the place. Lots of Okta and Zscaler (there’s that collision course). But plenty of SailPoint, Palo Alto Networks Inc., Microsoft, Netskope Inc., Thycotic, Cisco… all over the map.
Let’s now look specifically at how practitioners are thinking about Okta’s latest announcements.
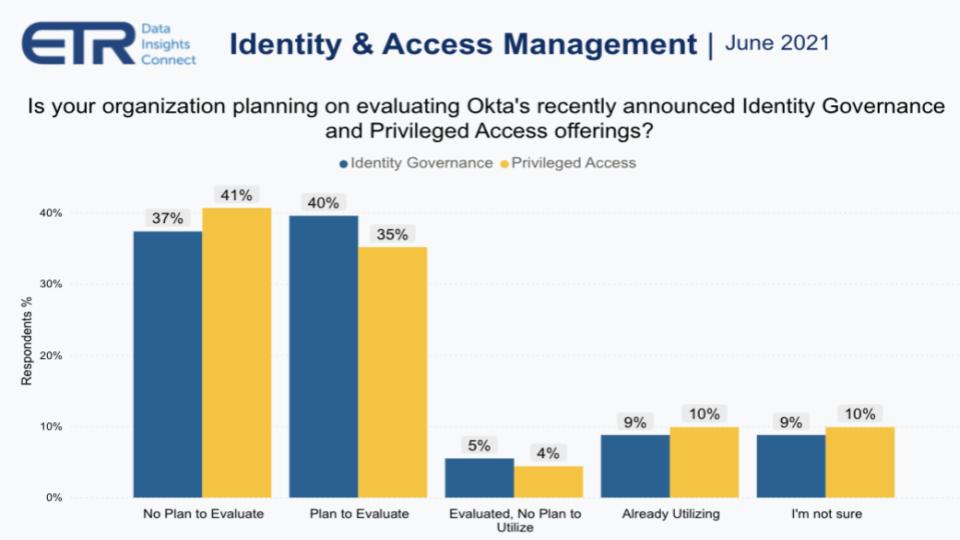
The chart above shows the results of the question: Are you planning to evaluate Okta’s recently announced identity governance and PAM offerings?
Forty-five percent to nearly 50% of the respondents either were already using or plan to evaluate Okta in this context, with just around 40% saying they had no plans to evaluate. We see this data as positive for Okta because a huge portion of the market will take a look at what Okta’s doing. Combined with the underlying trends we shared earlier related to the need for convergence, this is goodness for the company.
Even if the blockers are too severe to overcome in the near term, Okta is on the radar of most companies and, as with the Microsoft MIM example, the company will be seen as increasingly strategic and could get another bite at the apple.
Even if customers don’t buy Okta’s convergence offerings in the near term, disaffection with other products could give Okta another bite at the apple.
Moreover, Okta’s acquisition of Auth0 is strategically important. One of the other things Jolly told us is that the company sees initiatives having two distinct starting points. On the one side, devs initiate and then hand it to the information technology department to implement. The reverse is also common, where IT is the starting point and then it goes to devs to productize the effort. The Auth0 acquisition gives Okta plays in both games.
The effects of the Auth0 acquisition are somewhat counterpoised. On the one hand, when you talk to practitioners, they’re excited about the joint capabilities and the gaps that Auth0 fills. On the other hand, it takes out one of Okta’s main competitors. And customers like competition because it accelerates innovation and gives pricing leverage to buyers.
We look at it this way: Many enterprises will spend more money to save time, and that’s where Okta has traditionally been strong. Other enterprises look at the price tag of an Okta and they have development capabilities, so they prefer to spend engineering time to save money. That’s where Auth0 has seen momentum.
Now, Todd McKinnon and company can have it both ways. If the price of Okta classic is too high, here’s a lower-cost solution with Auth0 that can save you money, if you have the developer talent and the time. It’s a compelling advantage for Okta despite the perceived downside from less competition.
The road to zero-trust networks is long and arduous. The goal is to understand, support and enable access for different roles safely and securely across an ecosystem of consumers, employees, partners and suppliers. You’ve got to simplify the user experience, today’s kludge of password management and security exposures just won’t cut it in a digital future.
Supporting users in a decentralized, no perimeter world is compulsory, but you must have federated governance.
There will always be room for specialists in this segment, especially for industry-specific solutions, such as within healthcare, education or government.
Hybrids are the reality for companies that have any substantive legacy apps on-premises.
Okta has put itself in a leadership position but is not alone. Complexity and fragmentation will likely remain. This is a highly competitive market with lots of barriers to entry, which is both good and bad for Okta. On the one hand, disrupting incumbents will not be easy. On the other hand, Okta is scaling up and growing rapidly – almost 50% per annum. With its convergence agenda and Auth0 acquisition, it can build a nice moat to its business and keep others out.
The vision is pretty clear. Next up: execution.
Remember we publish each week on Wikibon and SiliconANGLE. These episodes are all available as podcasts wherever you listen.
Email david.vellante@siliconangle.com, DM @dvellante on Twitter and comment on our LinkedIn posts.
Also, check out this ETR Tutorial we created, which explains the spending methodology in more detail. Note: ETR is a separate company from Wikibon and SiliconANGLE. If you would like to cite or republish any of the company’s data, or inquire about its services, please contact ETR at legal@etr.ai.
Here’s the full video analysis:
THANK YOU