 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
Microsoft security researcher Vladimir Tokarev demonstrated an interesting attack on the industrial internet of things automation software called Codesys.
Tokarev, who showed the exploit last week at the annual BlackHat security conference in Las Vegas, used a miniature elevator model to demonstrate how the attack could crash its cab. The software – and more importantly, its software development kit — is widely used in millions of programmable logic controller or PLC chips that run everything from traffic lights and water treatment plants to commercial building operations automation and energy pipelines.
Last September, Tokarev found 16 vulnerabilities he collectively calls CoDe16. These employ both remote code execution and denial-of-service techniques to take control over the PLCs and enable attackers to insert malware.
“With Codesys being used by many vendors, one vulnerability may affect many sectors, device types, and verticals, let alone multiple vulnerabilities,” he said in a blog post describing the research. Microsoft Corp. estimates the software is used in 1,000 different types of devices made by more than 500 manufacturers.
This isn’t the first Codesys vulnerability. Last November, Forescout researchers found another problem with the software that affects its logic processes.
Tokarev posted his analysis and code on GitHub for others to examine, along with a tool that businesses can use to identify at-risk components. The Codesys framework uses its own network protocols and special TCP/IP port numbers that he had to reverse-engineer to understand its operation and discover these vulnerabilities.
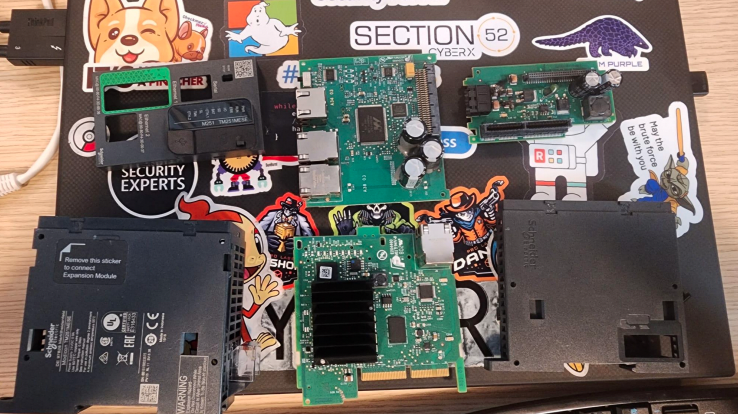
Many of the attacks made use of buffer overflow conditions. Tokarev assembled a variety of gear in his work and showed the conference attendees this photo:
Codesys comes with Windows-based management software and a simulator that’s used for testing purposes. “Because of its popularity and because of its wide usage around the globe, it’s a very interesting, critical attack vector that should be protected and mitigated,” he said at the conference session.
Codesys versions prior to c.3.5.19.0 are vulnerable to the discovered vulnerabilities, and users should upgrade their firmware using this link. Microsoft has other recommendations, including network segmentation to isolate the PLCs from direct online access, as well as least-privilege management techniques to restrict users who have access to the devices and have the ability to post changes to the components.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.