 NEWS
NEWS
 NEWS
NEWS
 NEWS
NEWS
One in three organizations has experienced an insider cyber attack in the last year, and 74 percent of security professionals say they feel vulnerable to insider threats. Fifty-six percent think insider leaks have become more frequent over the past year.
Those are among the findings of a new report by cloud and mobile application security vendor Bitglass Inc., based upon a survey of more than 500 IT professionals on LinkedIn. Careless or malicious user behavior was cited as the top source of data leakage, up slightly from a year ago. Cybersecurity professionals said they’re concerned with inadvertent leaks that result from unsanctioned application usage, unintended external sharing and unsecured mobile devices.
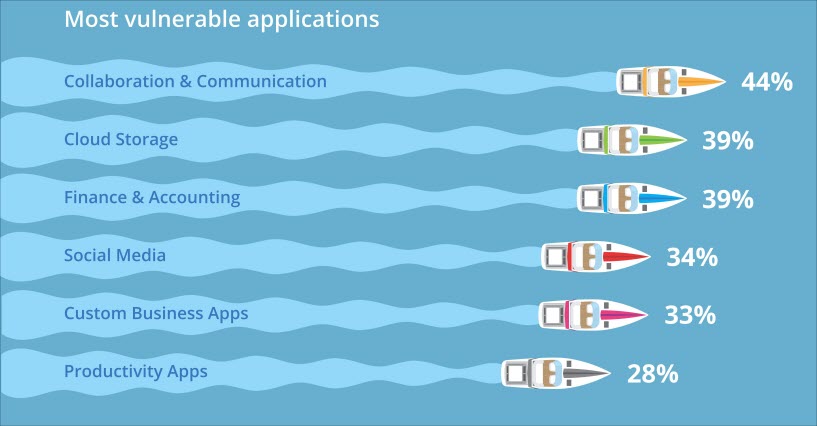
The survey highlights the growing risks presented by the bring-your-own-device (BYOD) phenomenon and unsanctioned use of cloud services. Employees may inadvertently share privileged information with others through cloud file stores or social networks, or they may download proprietary data to unsecured mobile phones. Not surprisingly, collaboration tools (44 percent) and cloud storage apps (39 percent) were perceived to be most vulnerable to insider threats. Privileged users were pegged as the greatest security risk because they typically have access to the most sensitive data.
While unintentional disclosure was seen as the top threat, a surprising 61 percent cited malicious insiders as a concern. However, that result may not be such a surprise in light of a survey earlier this year that found that 27 percent of U.S. office workers at large companies would sell their work password to an outsider, some for as little as $100.
Cloud services and mobile devices pose a whole new set of security problems for IT organizations. Even the most sophisticated firewalls and intrusion detection equipment are useless against activity by authorized employees. One-third of organizations don’t have analytics that can detect insider threats and only 15 percent use behavior analytics, a relatively new security technique that compares activity to a baseline to look for deviations that signal a breach.
Cybersecurity professionals agreed that lack of employee training (62 percent), insufficient data protection solutions (57 percent), an increase in devices with access to sensitive data (54 percent) and more data leaving the network perimeter (48 percent) are the biggest culprits of data leakage.
What’s the solution? Policies, identity/access management and encryption were all cited by 50 percent or more of the respondents. In general, respondents indicated they are focusing more on deterrence than on detection.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.