 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
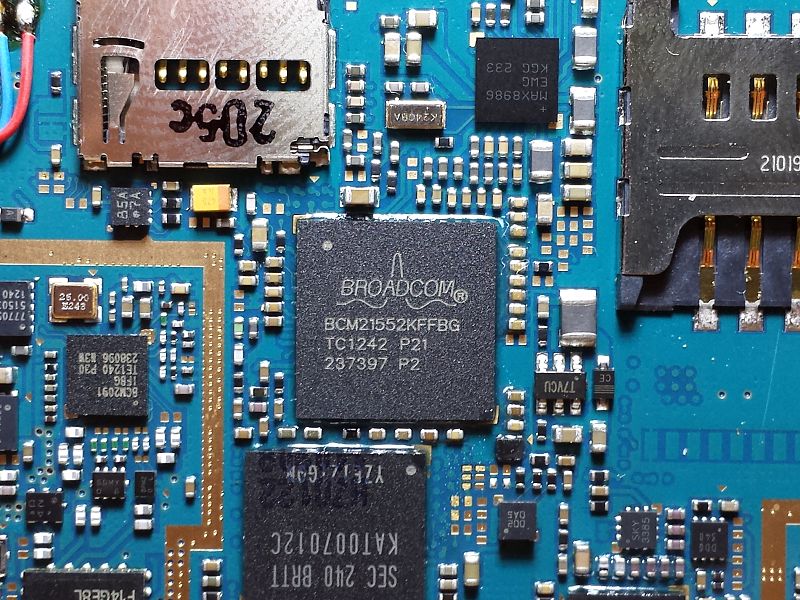
A vulnerability in Wi-Fi chipsets manufactured by Broadcom Ltd. and used in Android and iOS devices allows attackers to gain easy access to the devices, according to newly published research.
Details of the vulnerability, first published by Google’s Project Zero security team member Gal Beniamini, specify that a remote-code execution vulnerability lies in Broadcom’s Wi-Fi stack that allows hackers to execute malicious code by simply being within the same Wi-Fi range of the targeted phone or device. Worse still, a successful exploitation requires no user input, meaning that an attack can take place without users even knowing they have been targeted.
The proof-of-concept exploit uses Wi-Fi signals that contain irregular values that in turn cause the firmware behind Broadcom’s chip to overflow its stack. A stack is the data structure that stores information about the active subroutines of a computer program. That means that by pumping unexpected irregular data into the stack, the stack itself overflows. That is, it exceeds the amount of data it can hold (think of an overflowing bath tub), causing it to become dysfunctional.
Once the stack is in this situation, Beniamini was able to target the timers responsible for regularly occurring events such as scans, providing the ability to overwrite specific regions of the device memory with nefarious code.
Beniamini warned that the lack of security protections built into many platforms made the Broadcom chipset a prime target.
“We’ve seen that while the firmware implementation on the Wi-Fi SoC is incredibly complex, it still lags behind in terms of security,” he noted. “Specifically, it lacks all basic exploit mitigations — including stack cookies, safe unlinking and access permission protection (by means of an MPU).”
The good news is that prior to publication, both Google and Apple were informed of the vulnerability. Apple patched it with the release of iOS 10.3.1 on Monday and Google released a patch in its April security release. That said, the risks still remain particularly for Android users because many devices never receive security updates. And even those that do often have to wait for the device maker or telecommunications company to release the update to them.
THANK YOU