 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
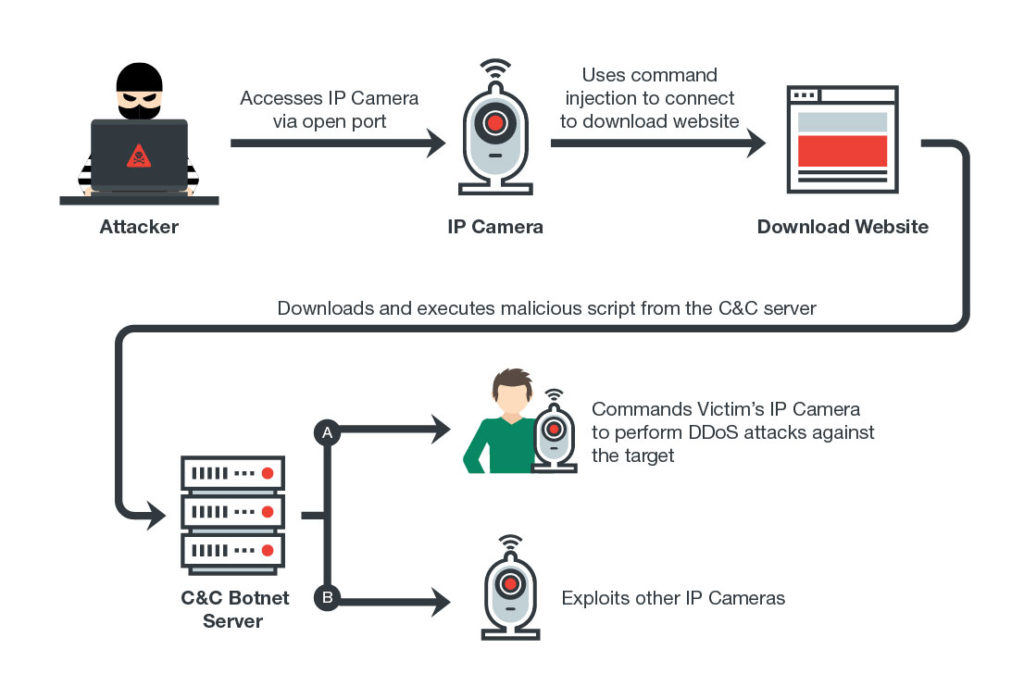
Another day, another Internet of Things botnet. This time, a new botnet discovered in the wild is believed to have infected over 120,000 Internet-connected cameras.
Dubbed Persirai by researchers at Trend Micro Inc., the botnet is targeting more 1,000 Internet Protocol camera models from various off-brand producers. Discovered using Shodan’s recently released command-and-control center search service, Persirai varies from the better-known Mirai botnet in that it exploits a known zero-day vulnerability found in software commonly used by IoT cameras. Mirai uses brute-force login attempts to steal credentials.
Once the botnet gains access to a targeted camera, hackers can use the infected device to perform distributed denial-of-service attacks on targeted IP addresses. They can also use the infected camera to discover other devices to infect, allowing it to spread further.
Persirai also takes steps to hide itself and to prevent competition, deleting itself from the device once it has been installed to continue to run only in memory. At the same time it blocks the new exploit on the infected device to prevent other hackers and botnets from being able to gain access.
Interestingly, the researchers found that the C&C server for the botnet uses the .IR country code, the Iranian top-level domain extension, and that Persian characters were found in the malware code used by the botnet. However, they note that this doesn’t necessarily indicate that the hacker behind the botnet is Iranian.
The researchers not surprisingly recommend that IP camera owners implement steps other than password protection alone to ensure that their devices are protected from external attacks. That includes disabling Universal Plug and Play on their routers to prevent devices opening ports to the external Internet without any warning. The Trend Micro researchers added that device manufacturers need to step up their game.
“The burden of IoT security does not rest on the user alone—it’s also dependent on the vendors themselves, as they should be the ones responsible for making sure that their devices are secure and always updated,” they noted. “In line with this, users should make sure that their devices are always updated with the latest firmware to minimize the chance of vulnerability exploits.”
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.