 INFRA
INFRA
 INFRA
INFRA
 INFRA
INFRA
First the good news: Ransomware attacks are on the decline.
But there’s plenty of bad news as well. The volume of malware that security researchers are finding in the wild has risen dramatically. Cybercriminals are targeting cryptocurrency wallets and hijacking computers to mine bitcoin. Some old favorite malware types, such as banking Trojan viruses, are also reappearing in malicious new forms.
Those are among the findings of Malwarebytes Corp.’s annual “State of Malware” report, which was released today. The report, which Malwarebytes creates by mining data collected from the company’s own threat-facing honeypots with analysis by its own researchers, shows how fast the threat landscape is changing. Malwarebytes’ findings jibe with those of Check Point Software Technologies Ltd.’s Global Threat Intelligence Trends report for the second half of 2017, also released today. It found that one in five organizations have felt the impact of cryptomining malware.
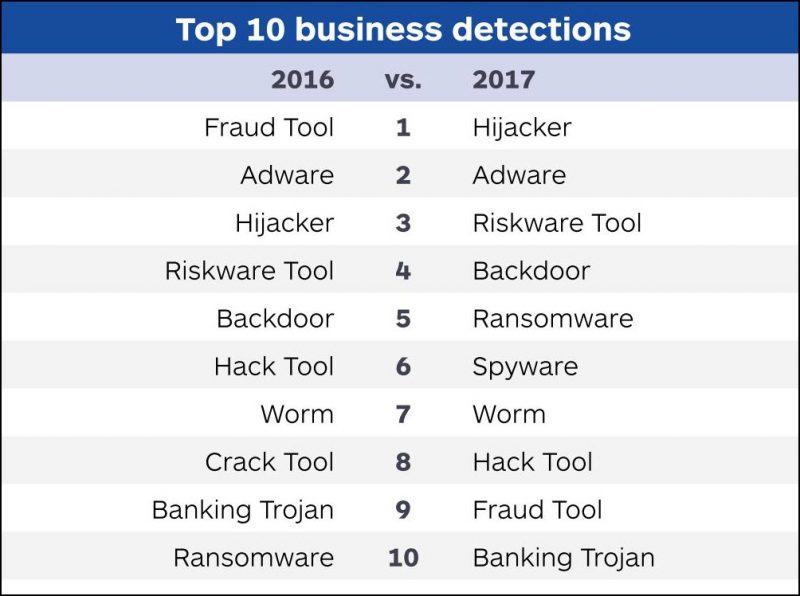
Although ransomware detections increased 90 percent for business customers, development of new strains of the disk-encrypting attack declined toward the end of the year. Researchers speculated that increased user awareness and better backup procedures have made organizations less vulnerable to attack, and less likely to pay when attacked. Ransomware was never a big-money business to begin with. “The ROI for criminals in ransomware attacks isn’t worth it anymore,” said Adam Kujawa, director of Malwarebytes Labs.
So attackers have gone back to some of their old reliable tools. Adware detection grew 132 percent, making it the most common consumer threat on the list for 2017. Adware now represents about 40 percent of consumer threat detections, double the percentage of a year earlier. Adware attacks serve up unwanted ads to users and charge advertisers for them.
“There’s been a shift from stealing money directly from users to using the framework of the advertising industry,” Kujawa said. With the decline in adware infections over the last couple of years, the remaining adware makers are able to gather bigger returns.
The report also cites a 40 percent jump in hijackers and a 30 percent increase in spyware detections, along with more than a doubling of financial data-stealing banking Trojans.
 The big news of 2017 from the malware standpoint was cryptomining. Attackers use conventional malware, along with malicious spam and exploit kits, to hijack PCs and use their spare cycles to mine bitcoin and other cryptocurrencies. The process of creating new bitcoins involves solving complex mathematical problems that require large amounts of computing power, so attackers distribute the load across large numbers of compromised machines to save money.
The big news of 2017 from the malware standpoint was cryptomining. Attackers use conventional malware, along with malicious spam and exploit kits, to hijack PCs and use their spare cycles to mine bitcoin and other cryptocurrencies. The process of creating new bitcoins involves solving complex mathematical problems that require large amounts of computing power, so attackers distribute the load across large numbers of compromised machines to save money.
“By the end of 2017, basically anyone doing any kind of cybercrime was also likely dabbling in cryptomining,” researchers wrote. Conventional malware is also being used to cash in on bitcoin mania by attempting to break into cryptocurrency wallets.
“The last few months of the year has been insane for the amount of attacks related to bitcoin mining,” Kujawa said. “We see miners coming through bundled software, exploit kits and spam campaigns in massive amounts.” There are also browser-based infections that can hijack a CPU from within a single open window.
Verifying that you’ve been the victim of cryptomining is much like checking for the presence of any other malware, Kujawa said. “Look for especially slow system performance, high levels of network traffic and [graphics processing unit] usage,” he said. “Look at performance tab. If you see 100 percent of your CPU is being used, then that’s a problem.” Check Point said mining attacks use as much as 65 percent of CPU power.
“The second half of 2017 has seen crypto-miners take the world by storm to become a favorite monetizing attack vector,” said Maya Horowitz, threat intelligence group manager at Check Point. “While this is not an entirely new malware type, the increasing popularity and value of cryptocurrency has led to a significant increase in the distribution of crypto-mining malware.”
Check Point also pointed to a growing trend toward attacks originating with mobile devices. Mobile malware that attempts to attack network elements such as routers and switches redirect network traffic to a malicious server under the attacker’s control, the report said.
Other highlights of the Malwarebytes report:
To protect yourself, stick to the basics, Kujawa advised. “Keep your antivirus and antimalware definitions up to date. Patch systems within a few days of a patch’s release. And use two-factor authentication,” which verifies identity via a secondary method, such a code sent to a cell phone, he said. And guard logins and passwords carefully. “You should never be under the impression that your credentials are secure anymore,” Kujawa said.
Support our mission to keep content open and free by engaging with theCUBE community. Join theCUBE’s Alumni Trust Network, where technology leaders connect, share intelligence and create opportunities.
Founded by tech visionaries John Furrier and Dave Vellante, SiliconANGLE Media has built a dynamic ecosystem of industry-leading digital media brands that reach 15+ million elite tech professionals. Our new proprietary theCUBE AI Video Cloud is breaking ground in audience interaction, leveraging theCUBEai.com neural network to help technology companies make data-driven decisions and stay at the forefront of industry conversations.