 NEWS
NEWS
 NEWS
NEWS
 NEWS
NEWS
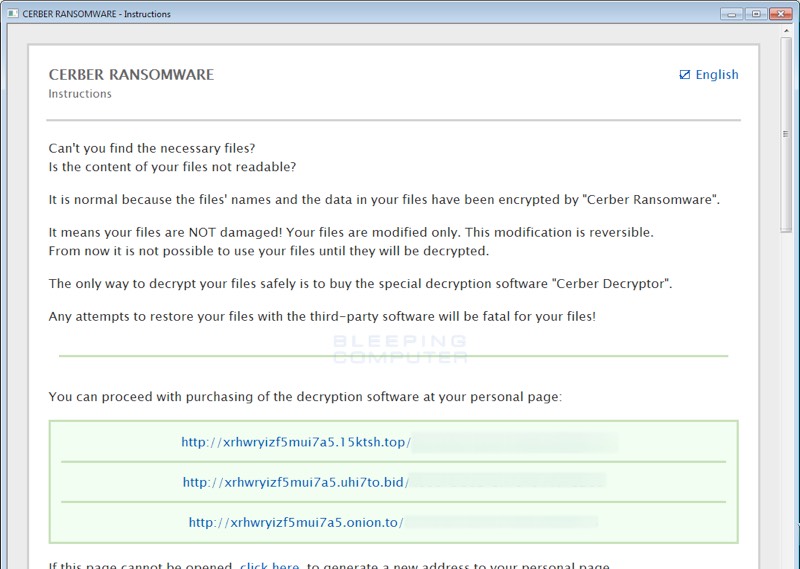
A new version of the notorious Cerber ransomware has been discovered that can kill database server processes.
Ransomware is malicious software that makes files unavailable until money is paid to restore access. The Cerber ransomware first emerged in March when it was discovered to encrypt a victim’s data files using AES encryption, with users then being asked to pay a ransom of 1.24 bitcoin to get their files back.
According to reports, Cerber is said to have accounted for over a quarter of the total ransomware detections in the past three months and has generated $2.3 million in annual revenue since it was launched. Cerber 3.0, according to Bleeping Computer, which made the discovery, now not only scrambles filenames on an infected system, but the extension is now replaced as well. This means that a file that was previously encrypted as 5NgPiSr5zo.cerber3, for example, would now be encrypted to a name like 1xQHJgozZM.b71c.
In addition, and perhaps more disturbingly, the ransomware can now kill database processes through the close-process directive present in its configuration file. On an infected system, Cerber 3.0 terminates all or some of the processes prior to starting the data encryption process. The reason it closes the processes is to enable the data files to be encrypted, something it cannot do when the data files are being used.
Cerber has been previously distributed via exploit kits, malware scams and spam emails. Now, it is being spread by Betabot, a trojan that infects computers and attempts to prevent users from accessing security websites while also disabling their antivirus and malware scan software.
An updated ransom note also appears in the new version with a demand for a smaller amount to release files, but like earlier versions also includes an audio file that alerts the user to its request for a ransom payment. The malware is said to be being sold on the dark web as a service and is used by cyber criminals who pay its creators a consistent part of their earnings.
Given that Betabot trojans usually bypass anti-virus programs, practicing safe internet won’t work in this case, however, Cerber can only run from privileged accounts, so in a workplace daily activities should only occur from limited accounts with Administrator accounts disabled on workstations to prevent infection.
THANK YOU