 SECURITY
SECURITY
 SECURITY
SECURITY
 SECURITY
SECURITY
A newly discovered Android vulnerability being exploited in the wild allows attackers to insert fake login screens into legitimate apps to steal credentials as well as undertake various other nefarious activities.
Detailed today by security researchers at Promon, the vulnerability, dubbed “StrandHogg,” exists as a result of the way Android handles multitasking. Found in all versions of Android including Android 10, the vulnerability allows a malicious app installed on an Android device to trigger malicious code when a user opens another app.
The malicious code can include fake login screens that appear to be from the legitimate app but are instead generated from the malicious app. Those currently exploiting the vulnerability are doing exactly that, specifically targeting banking apps, tricking users into entering their login details on a fake login screen, the users none the wiser as they’ve clicked on their banking app.
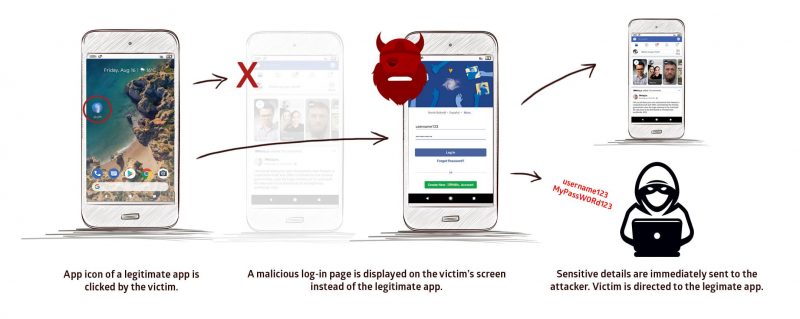
The discovery of the vulnerability came about after Promon was contacted by a Czech bank that couldn’t work out how money was being siphoned from customer accounts. It’s now believed that up to 60 different financial institutions may be have been targeted with 36 malicious apps found to be designed to exploit StrandHogg including some in the Google Play Store.
While stealing banking login details has been the initial focus of those exploiting the vulnerability, the researchers warn that it can be used various other purposes. StrandHogg opens the door for attackers to listen to a user through a microphone, take photos using the device’s camera, read and send SMS text messages, make or record phone conversations, phish login credentials, obtain access to all files and logs on a device and finally access location and GPS information.
Craig Young, computer security researcher for enterprise cybersecurity firm Tripwire Inc.’s vulnerability and exposure research team, told SiliconANGLE that user interface redressing vulnerabilities can be particularly dangerous in mobile platforms where there are typically already fewer on-screen indicators to confirm what site a user is interacting with.
“In general, users must be careful about installing apps which request the screen overlay permission or require accessibility settings,” Young said. “Where available, users should also make sure that the ‘Verify Apps’ setting is enabled in Android’s security settings.”
THANK YOU